The National Security Agency (NSA) and Cybersecurity and Infrastructure Security Agency (CISA) Kubernetes Hardening Guide is a resource that provides detailed recommendations and best practices for securing Kubernetes clusters. This guide is developed by the U.S. government agencies to help organizations enhance the security posture of their Kubernetes environments, following industry standards and security principles.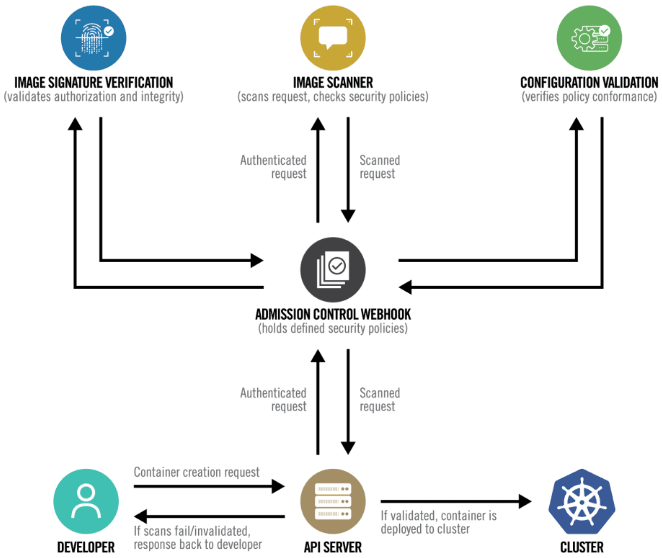
Key benefits and aspects of NSA and CISA Kubernetes Hardening Guide
- Government Authority: The guide is developed by authoritative U.S. government agencies, lending credibility to its recommendations and making it a reliable resource for organizations seeking to secure their Kubernetes clusters.
- Comprehensive Security: The guide offers comprehensive guidance on a wide range of security considerations for Kubernetes clusters, covering various aspects of cluster setup, configuration, and operation.
- Adherence to Standards: The recommendations provided in the guide are often aligned with industry best practices and established security standards, ensuring that security measures are consistent with widely accepted norms.
- Risk Mitigation: By implementing the guide's recommendations, organizations can effectively mitigate risks associated with common security vulnerabilities, unauthorized access, and potential cyberattacks.
- IAM and RBAC: The guide emphasizes the importance of Identity and Access Management (IAM) and Role-Based Access Control (RBAC) in controlling access to Kubernetes resources, enhancing the overall security posture.
- Pod Security Policies: Detailed insights are provided on enforcing strict pod security policies to prevent unauthorized or malicious activity within containers.
- Network Security: The guide covers network security practices within Kubernetes clusters, including network policies, service mesh security, and encryption of communication.
- Configuration Hardening: Recommendations are offered for hardening Kubernetes cluster configuration to minimize attack surfaces and vulnerabilities.
- Logging and Monitoring: The guide highlights the significance of robust logging and monitoring practices for detecting and responding to security incidents effectively.
- Ongoing Updates: The guide is regularly updated to address new security challenges, emerging threats, and changes in the Kubernetes ecosystem, ensuring that its recommendations remain relevant.
- Open Source: The NSA and CISA Kubernetes Hardening Guide is often shared as an open-source resource, allowing organizations to freely access and utilize the security recommendations.
- Risk-Appropriate Measures: The guide acknowledges that security measures should be proportionate to the organization's risk profile, allowing for customization based on specific needs and risk tolerance.
- Incident Response: The guide may provide guidance on incident response procedures, helping organizations handle security breaches effectively and minimize damage.
By following the NSA and CISA Kubernetes Hardening Guide, organizations can implement robust security practices in their Kubernetes clusters, reducing vulnerabilities, enhancing the defense against cyber threats, and aligning with the recommendations of reputable government cybersecurity agencies.
[ Download NSA and CISA Kubernetes Hardening Guide ]
To learn more about NSA and CISA Kubernetes Hardening Guide, visit the following link:
https://www.nsa.gov/Press-Room/News-Highlights/Article/Article/2716980/nsa-cisa-release-kubernetes-hardening-guidance