Penetration Testing (PenTest) is a structured approach to probing and evaluating the security posture and model of a product. It involves a combination of off-the-shelf tools, custom tools, and assessment workflows, some of which are derived from open-source standards like OWASP. The primary objective is to thoroughly test the live product and identify potential attack vectors that could lead to exploits or vulnerabilities. The scope of testing can encompass the entire product functionality or specific functionalities in a new or updated release.
Penetration testing applies to various types of products, ranging from hardware, firmware, and appliances to web-based software and RESTful API platforms. It serves as a comprehensive assessment technique for assessing security across different product categories.
Penetration testing can be conducted internally by an organization's information security team and/or externally by a third-party or independent assessor. The choice of internal or external testing depends on factors such as resource availability, expertise, and the need for an objective evaluation.
By conducting penetration testing, organizations gain valuable insights into their product's security vulnerabilities and potential exploits. The findings help identify areas that require remediation and allow for proactive measures to strengthen the product's overall security.
Methodology
A penetration testing methodology refers to the structured approach and execution of a penetration test. It serves as a framework for identifying security vulnerabilities within an organization. Each methodology outlines a distinct process that companies can adopt to uncover these vulnerabilities. While organizations have the option to develop their own custom processes, there are established and widely recognized methodologies available in the industry. These methodologies can be utilized as ready-made solutions or used as a foundation to build upon, depending on the organization's specific needs and goals.
There are various standards and methodologies that ensure the penetration test is authentic and covers all important aspects. Here are 5 penetration testing methodologies and standards that will guarantee a return of security investment:
 OSSTMM: OSSTMM is short for Open-Source Security Testing Methodology Manual. The OSSTMM framework is widely recognized as one of the industry's leading standards, providing a scientific methodology for network penetration testing and vulnerability assessment. It offers a comprehensive guide for testers to identify security vulnerabilities within a network and its components, utilizing various angles of attack. This methodology relies on the tester's expertise and experience, along with human intelligence, to interpret the identified vulnerabilities and assess their potential impact on the network. The OSSTMM framework is designed to support network development teams. Many developers and IT teams base their firewalls and networks on this manual and its provided guidelines. Although the framework does not endorse any specific network protocol or software, it emphasizes best practices and the necessary steps to ensure network security.
OSSTMM: OSSTMM is short for Open-Source Security Testing Methodology Manual. The OSSTMM framework is widely recognized as one of the industry's leading standards, providing a scientific methodology for network penetration testing and vulnerability assessment. It offers a comprehensive guide for testers to identify security vulnerabilities within a network and its components, utilizing various angles of attack. This methodology relies on the tester's expertise and experience, along with human intelligence, to interpret the identified vulnerabilities and assess their potential impact on the network. The OSSTMM framework is designed to support network development teams. Many developers and IT teams base their firewalls and networks on this manual and its provided guidelines. Although the framework does not endorse any specific network protocol or software, it emphasizes best practices and the necessary steps to ensure network security.
The OSSTMM methodology (Open Source Security Testing Methodology Manual) offers flexibility, enabling testers to customize assessments according to their company's specific needs and technological context. By adopting these standards, organizations can gain an accurate overview of their network's cybersecurity posture and receive tailored solutions that align with their technological environment. This empowers stakeholders to make informed decisions to effectively secure their networks. OWASP: The Open Web Application Security Project (OWASP) stands as the industry's foremost standard for application security. Supported by a highly knowledgeable community that stays at the forefront of emerging technologies, this methodology has proven invaluable in helping countless organizations mitigate application vulnerabilities. Widely known, this pentest standard is developed and updated by a community keeping in trend with the latest threats. Apart from application vulnerabilities, this also accounts for logic errors in processes.
OWASP: The Open Web Application Security Project (OWASP) stands as the industry's foremost standard for application security. Supported by a highly knowledgeable community that stays at the forefront of emerging technologies, this methodology has proven invaluable in helping countless organizations mitigate application vulnerabilities. Widely known, this pentest standard is developed and updated by a community keeping in trend with the latest threats. Apart from application vulnerabilities, this also accounts for logic errors in processes.
The OWASP framework provides a robust methodology for web application penetration testing. It not only identifies common vulnerabilities within web and mobile applications but also uncovers complex logic flaws resulting from unsafe development practices. The comprehensive guidelines included in the updated guide cover each penetration testing method, encompassing over 66 controls in total. This breadth allows testers to identify vulnerabilities across a wide array of functionalities present in modern applications. NIST: National Institute of Standards and Technology (NIST) offers very specific pentesting methodology for pentesters to help them improve the accuracy of the test. Both large and small companies, in various industries, can leverage this framework for a penetration test. Unlike many other information security manuals, the National Institute of Standards and Technology (NIST) offers highly specific guidelines tailored for penetration testers. NIST's manual is well-suited to enhance the overall cybersecurity of organizations. The latest version, 1.1, places increased emphasis on Critical Infrastructure Cybersecurity. Compliance with the NIST framework is often a regulatory requirement for various American providers and business partners.
NIST: National Institute of Standards and Technology (NIST) offers very specific pentesting methodology for pentesters to help them improve the accuracy of the test. Both large and small companies, in various industries, can leverage this framework for a penetration test. Unlike many other information security manuals, the National Institute of Standards and Technology (NIST) offers highly specific guidelines tailored for penetration testers. NIST's manual is well-suited to enhance the overall cybersecurity of organizations. The latest version, 1.1, places increased emphasis on Critical Infrastructure Cybersecurity. Compliance with the NIST framework is often a regulatory requirement for various American providers and business partners.
Through its framework, NIST addresses information security across a range of industries, including banking, communications, and energy. Both large and small firms can adapt the standards to suit their specific needs and requirements. To meet NIST's rigorous standards, companies must conduct penetration tests on their applications and networks following established guidelines. This American information technology security standard ensures that organizations fulfill their cybersecurity control and assessment obligations, mitigating the risks of cyberattacks to the greatest extent possible. NIST's exceptional standards and technology significantly contribute to cybersecurity innovation across numerous American industries. PTES: The PTES Framework (Penetration Testing Methodologies and Standards) is a comprehensive guide that outlines the recommended approach for structuring a penetration test. This standard provides valuable direction to testers, covering various crucial steps such as initial communication, information gathering, and threat modeling phases. The goal of PTES is to create a comprehensive and up-to-date standard for penetration testing as well as to build awareness among businesses as to what to expect from a pentest.
PTES: The PTES Framework (Penetration Testing Methodologies and Standards) is a comprehensive guide that outlines the recommended approach for structuring a penetration test. This standard provides valuable direction to testers, covering various crucial steps such as initial communication, information gathering, and threat modeling phases. The goal of PTES is to create a comprehensive and up-to-date standard for penetration testing as well as to build awareness among businesses as to what to expect from a pentest.
By adhering to this penetration testing standard, testers thoroughly familiarize themselves with the organization and its technological landscape. This in-depth understanding allows them to prioritize potentially vulnerable areas and identify advanced attack scenarios that may be attempted. Additionally, the framework offers guidelines for conducting post-exploitation testing, enabling testers to verify the successful remediation of identified vulnerabilities. The seven phases defined within this standard ensure a well-executed penetration test and provide practical recommendations that management teams can rely on when making informed decisions. ISSAF: The ISSAF standard (Information System Security Assessment Framework) provides a highly structured and specialized approach to penetration testing, surpassing previous standards and supported by the Open Information Systems Security Group. If an organization requires an advanced and customized methodology tailored to its unique context, this manual is invaluable for the specialists responsible for conducting a penetration test. These comprehensive standards empower testers to meticulously plan and document every step of the penetration testing procedure, from initial planning and assessment to reporting and artifact destruction. The ISSAF standard covers all aspects of the process. It proves particularly vital for pentesters who utilize a combination of different tools, as they can align each step with specific tools in their arsenal.
ISSAF: The ISSAF standard (Information System Security Assessment Framework) provides a highly structured and specialized approach to penetration testing, surpassing previous standards and supported by the Open Information Systems Security Group. If an organization requires an advanced and customized methodology tailored to its unique context, this manual is invaluable for the specialists responsible for conducting a penetration test. These comprehensive standards empower testers to meticulously plan and document every step of the penetration testing procedure, from initial planning and assessment to reporting and artifact destruction. The ISSAF standard covers all aspects of the process. It proves particularly vital for pentesters who utilize a combination of different tools, as they can align each step with specific tools in their arsenal.
The assessment section, with its detailed approach, governs a significant portion of the procedure. For each vulnerable area within the system, ISSAF provides complementary information, various attack vectors, and potential outcomes when vulnerabilities are exploited. Testers may also find information on commonly used tools employed by real attackers to target these areas. This wealth of information enables the planning and execution of advanced attack scenarios, offering a substantial return on investment for organizations seeking to fortify their systems against cyberattacks.
Prerequisites for Penetration Testing
- Access to the testing environment.
- Access to a document repository containing design and architecture documents.
- Access to the source code (for whitebox engagement).
- Proper user and access provisioning to enable the appropriate level of testing.
- Access to a pre-production product instance or environment to conduct testing.
- Functional workflows with roles and permissions should be available (for whitebox engagement) .
- Business use cases with personas and relevant information should be provided (for whitebox engagement).
- Authentication and authorization details should be accessible (for whitebox engagement).
- Integration with code scanning tools, such as Code Quality Scanning and Static Code Analysis (for whitebox engagement).
- Inform internal and external infrastructure teams, as well as cloud or VPC providers, in advance and obtain their permission for the penetration testing activities.
Penetration Testing Output
The output of penetration testing is a comprehensive report that outlines the identified issues and provides recommended resolutions. The report ensures clear understanding and reproducibility by including the following elements:
- Security Issue Documentation: The report documents the discovered security issues in a clear and concise manner. Each issue is described, providing relevant information and context to aid comprehension.
- Formal Penetration Testing Report: A formal report is submitted, summarizing the findings, observations, and recommendations resulting from the penetration testing exercise. This report serves as a valuable resource for stakeholders to understand the security status of the tested product.
- Detailed Explanation and Reproducibility: The report includes a detailed explanation of the identified issues, enabling stakeholders to comprehend the vulnerabilities and their potential impact. Additionally, the report provides sufficient information for the issues to be reproduced, facilitating validation and verification of the findings.
- Severity Assessment Documentation: The report documents the reasoning behind assigning severity levels to each identified issue. This documentation clarifies the criteria and considerations used to assess the potential impact and urgency of remediation efforts.
- Documentation of Example Workflows, Source Code, and Scenarios: For each security issue, the report includes relevant information such as example workflows, source code snippets, or scenarios that demonstrate how the issue can be exploited. This documentation aids in understanding the specific context and technical aspects of the vulnerabilities.
- Risk Rating using the DREAD Model: The report employs the DREAD model (Damage, Reproducibility, Exploitability, Affected Users, Discoverability) to assess the risk posed by each identified vulnerability. This risk rating helps prioritize remediation efforts based on the potential impact and likelihood of exploitation.
By providing a comprehensive and well-documented report, the penetration testing output enables organizations to understand the security risks they face and make informed decisions regarding remediation strategies and risk mitigation.
Ranking of Vulnerabilities
Vulnerabilities can be ranked from the perspective of risk factors. By determining the risk factor posed by the various identified vulnerabilities, it is possible to create a prioritized list of vulnerabilities to support a risk mitigation strategy, such as prioritizing the vulnerabilities to be mitigated first. Different risk factors can be used to rank vulnerabilities as Critical, High, Medium, or Low risk. In general, Vulnerability risk models use different factors to model risks such as those shown below: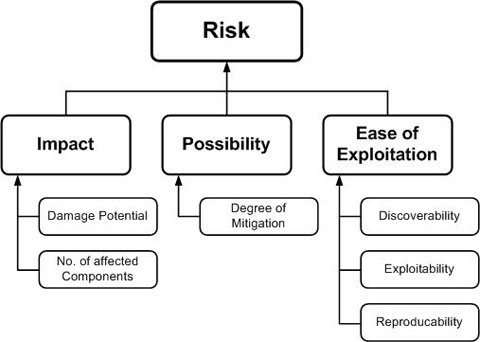
Ranking Risk Factors
A finding contains analysis and documentation of the vulnerability identified within the assessed application. This analysis includes:
- Identifying the application’s security objectives, and surveying the application’s architecture and design documentation
- Decomposing the application and identifying vulnerabilities
- Classifying known vulnerabilities and assigning the appropriate risk rating
- Formulate actionable recommendations that improve the security posture of the application
Vulnerabilities are grouped according to risk rating. Information for each of the threats includes the following:
- Name: The name of the vulnerability.
- Description: Comprehensive explanation of the vulnerability that was identified, including a high-level summary of the vulnerability.
- Privileges required: User privileges required to exploit the vulnerability.
- Threat Traceability Matrix: A simplified vulnerability model that describes how a vulnerability agent can attack the application, the business impact and attack mitigation strategies.
The Threat Traceability Matrix
- Threat agent: an entity that can act against an asset and cause harm.
- Attack surface: the collection of points that the threat agent directly interacts with the system.
- Attack: the category, based on the STRIDE threat model, of the kinds of exploits the threat agent can use to attack the system.
- Assets: data, functionality, or a property of the system that a threat agent wants to access.
- Impact: the impact severity associated with a successful attack.
- Mitigation: recommended controls to implement that mitigate the threat.
DREAD Score
DREAD is a classification scheme for quantifying, comparing and prioritizing the amount of risk presented by each evaluated threat. DREAD risk assessment model, risk factorization allows the assignment of values to the different influencing factors of a vulnerability. This provides a subjective process to rank vulnerabilities. To determine the ranking of a vulnerability, the vulnerability analyst answers questions for each factor of risk, for example:
| Risk Category | Meaning | Dread Average Ranking |
|---|---|---|
| Damage Potential | How big would the damage be if the attack succeeded? | If a threat exploit occurs, evaluate the damage caused 1= Nothing 5= Individual user data compromised 10=Complete system or data destruction/just a web browser is enough |
| Reproducibility | How easy is it to reproduce an attack? | How easy is it to reproduce the vulnerability exploit? 1 = Very hard or impossible even for administrators/DBAs 5 = One or two steps required, may need an authorized user 10= Possible by an unauthorized user |
| Exploitability | How much time, effort, and expertise is needed to exploit the vulnerability? | What is needed to exploit this vulnerability? 1 = Advanced programming & networking knowledge 5 = Malware exists on the Net, or any tolls available 10 = Just a web browser is enough |
| Affected Users | If a threat were exploited, what percentage of users would be affected? | How many users are affected? 1 = None 5 = Some users, but not all 10 = All users |
| Discoverability | How easy is it for an attacker to discover this vulnerability? | How easy is it to discover the vulnerability? 1 = Very hard or impossible; needs source code or admin access 5 = Can figure it out by guessing or monitoring network traces 10 = Information is visible in the web browser or address bar or in the form or as a hidden variable |
A point system of numbers 1-10, representing low to high severity, is used to calculate a DREAD score that can help compare one threat to another. Each category above is given a score between 1-10, then following formula is used to calculate the risk of a vulnerability:
DREAD SCORE = Damage + Reproducibility + Exploitability + Affected Users + Discoverability
The threat is then assigned a risk rating using the DREAD score and table below:
| Risk Rating | DREAD Score | Risk Description |
|---|---|---|
| Critcal |
40-50 |
Critical risk findings and vulnerabilities should be considered immediately for review and resolution. Exploitation of critical vulnerabilities is relatively easy and can lead directly to a malicious actor gaining privileged access (root or administrator) to the system. Findings with this risk rating, if not quickly addressed, may pose risks that could negatively impact business operations or business continuity. |
| High | 25-39 | High risk findings and vulnerabilities should be considered for review and resolution within a short time frame. These vulnerabilities can lead to a malicious actor gaining non-privileged access (standard user) to a system, or the vulnerability can be leveraged to gain elevated level of access. |
| Medium | 11-24 | Medium risk findings and vulnerabilities should be considered once the critical and severe risks have been addressed. These vulnerabilities may leak sensitive data that a malicious actor can use to assist in the exploitation of other vulnerabilities. Moderate findings do not pose a substantial threat to business operations. |
| Low | 1-10 | Low risk findings and vulnerabilities are informational and do not pose significant risk to the environment. |
Recommendations
There are a few recommendations to incorporate a successful penetration test into a project plan :
- Engage with the Application Security team as early as possible in the project lifecycle to ensure timely assignment of a security engineer to this activity.
- It is advisable to start planning right after the Security Architecture Review.
- For larger releases that require ample testing time or have fixed delivery dates (e.g., contract or sales/marketing promotions).
- Utilize a non-production environment for the penetration testing activity. This helps mitigate the risk of product instability resulting from loading, fuzz testing, or similar activities.
- Schedule the penetration testing after the "feature complete" and "product stabilization" cycles are finished. This ensures that the results primarily indicate security issues rather than functional, scaling, or stability concerns.
Time & Effort Needed
- The time and effort needed for penetration testing depend on the complexity of the product and the scope of the pentest effort.
- The duration of a penetration test is influenced by the scope of the application, with 1-2 weeks being a common timeframe.
- If necessary, a time-boxed engagement can be scheduled, allowing for maximum test coverage within a specified time period.
Penetration Testing Tools
Depending on the product being assessed or tested, penetration testers may employ off-the-shelf tools, such as security scanners, to gather data as part of the reconnaissance phase. These tools assist in providing background information and facilitating the actual security assessment and penetration testing process.
- Dynamic Application Security Testing (DAST) is a methodology and approach used to assess the security of web applications by analyzing them while they are running. DAST involves actively probing the application in a live environment to identify vulnerabilities and security weaknesses. DAST simulates real-world attack scenarios by sending malicious input to the application and analyzing the responses. It helps identify security flaws that may not be evident during static analysis or code review processes. DAST focuses on the application's runtime behavior, including input validation, authentication mechanisms, access controls, session management, and other potential vulnerabilities.
- Burp Suite is a popular and widely used integrated platform for web application security testing. Developed by PortSwigger, Burp Suite provides a comprehensive set of tools that assist security professionals in performing various security assessments, such as penetration testing, vulnerability scanning, and web application security analysis. Burp Suite is highly customizable and extensible, allowing users to add their own plugins or extensions to enhance its functionality and tailor it to their specific needs. It is widely used by security professionals, penetration testers, and developers to identify and mitigate security vulnerabilities in web applications. Burp Suite consists of several components that work together to support the entire security testing process:
- Proxy: The Proxy module acts as an intermediary between the user's browser and the target web application. It allows users to intercept and modify HTTP and HTTPS requests and responses, facilitating manual testing and analysis.
- Scanner: The Scanner module automates the process of identifying security vulnerabilities within web applications. It actively scans the target application for common vulnerabilities, including SQL injection, cross-site scripting (XSS), and more, helping to identify potential security weaknesses.
- Intruder: The Intruder module is designed to perform automated attacks against web applications. It enables users to create custom attack payloads and automate the process of testing multiple parameters or inputs for vulnerabilities.
- Repeater: The Repeater module allows users to manually modify and resend individual HTTP requests to the target application. It is helpful for testing and verifying vulnerabilities, as well as for understanding how the application responds to different inputs.
- Sequencer: The Sequencer module assesses the quality and randomness of session tokens or other values used for security purposes within the application. It helps identify weak session management practices that could lead to session hijacking or other attacks.
- Decoder: The Decoder module provides functionality for encoding and decoding various data formats, such as URL encoding, Base64 encoding, and more. It assists in manipulating and analyzing data during security testing.
- Metasploit is a powerful and widely-used penetration testing framework that provides tools and resources for security professionals to perform comprehensive security assessments and exploit vulnerabilities in systems, networks, and applications. It is an open-source project maintained by Rapid7, a leading cybersecurity company. Metasploit is widely used by penetration testers, ethical hackers, and security researchers to identify vulnerabilities, assess security risks, and validate the effectiveness of security controls. It is a versatile framework that combines both automated and manual testing techniques to simulate real-world attacks and assist in securing systems and networks. Metasploit is built into Kali Linux, which is a popular Linux distribution widely used for penetration testing and ethical hacking. Kali Linux is specifically designed for security testing and includes a wide range of pre-installed tools, with Metasploit being one of the key components. When installing Kali Linux, penetration tester will have access to the Metasploit Framework by default. It is accessible through the command line interface (CLI) and provides a powerful set of tools for conducting penetration testing assessments, exploit development, vulnerability scanning, and post-exploitation activities. Key features of Metasploit include:
- Exploit Development: Metasploit provides a vast collection of pre-built exploits, payloads, and auxiliary modules that can be used to target and exploit vulnerabilities in various systems and applications. It simplifies the process of developing and executing exploits against vulnerable targets.
- Vulnerability Scanning: Metasploit includes features for scanning and identifying vulnerabilities in target systems. It can scan for known vulnerabilities and misconfigurations, helping to identify potential entry points for exploitation.
- Post-Exploitation Framework: Once a system is compromised, Metasploit provides a post-exploitation framework to gain further access, escalate privileges, and maintain control over the compromised system. It offers a range of post-exploitation modules to perform various tasks, such as data exfiltration, lateral movement, and persistence.
- Payload Generation: Metasploit enables the generation of custom payloads to deliver specific malicious code to target systems. These payloads can be designed to evade detection and perform specific actions, such as command execution, reverse shell connections, or data manipulation.
- Social Engineering Toolkit (SET): Metasploit includes the Social Engineering Toolkit (SET), which helps in conducting targeted social engineering attacks. It provides pre-built templates for various attack vectors, such as phishing emails, malicious websites, and USB attacks, to exploit human vulnerabilities.
- Reporting and Collaboration: Metasploit provides reporting features to generate detailed reports of the penetration testing assessments. It allows security professionals to document their findings, track progress, and collaborate with team members.
- SQLMap is an open-source penetration testing tool specifically designed for detecting and exploiting SQL injection vulnerabilities in web applications that use a SQL database. SQL injection is a common web application vulnerability that occurs when an attacker can manipulate input fields to inject malicious SQL statements into the application's database query. SQLMap automates the process of identifying and exploiting SQL injection flaws by performing a series of predefined and customizable tests. It supports a wide range of database management systems, including MySQL, Oracle, PostgreSQL, Microsoft SQL Server, and others. It's important to note that SQLMap should only be used for legitimate and authorized security testing purposes. Unauthorized use of SQLMap or exploiting SQL injection vulnerabilities without proper permission is illegal and unethical. It's always recommended to seek proper authorization and follow ethical guidelines when performing security assessments or penetration testing. Here are some key features and capabilities of SQLMap:
- Automatic Detection: SQLMap can automatically identify SQL injection vulnerabilities in a target web application by analyzing the input parameters and payloads that can trigger SQL errors or produce unexpected application behavior.
- Exploitation: Once a SQL injection vulnerability is detected, SQLMap can perform various exploitation techniques to extract valuable information from the database, such as tables, columns, and data. It can also execute arbitrary SQL commands on the database server.
- Brute-Forcing: SQLMap has built-in features for brute-forcing databases, such as guessing table and column names, or even cracking hashed user passwords stored in the database.
- Enumeration and Dumping: SQLMap can enumerate the structure and content of the database, providing detailed information about tables, columns, data types, and sample data. It can also dump the entire database or specific tables to local files for further analysis.
- File System Access: In some cases, SQLMap can exploit SQL injection vulnerabilities to gain access to the underlying file system of the web server, allowing it to read/write files or execute arbitrary commands.
- Post-Exploitation: SQLMap provides post-exploitation modules that allow for further exploitation or exploration, such as executing operating system commands on the target server or establishing a reverse shell.
- Automatic Detection: SQLMap can automatically identify SQL injection vulnerabilities in a target web application by analyzing the input parameters and payloads that can trigger SQL errors or produce unexpected application behavior.
- OWASP ZAP (short for "Zed Attack Proxy") is a free and open-source web application security testing tool. It is designed to help developers, security professionals, and penetration testers identify and address vulnerabilities in web applications. OWASP ZAP is widely recognized and used within the security community as a powerful and effective tool for web application security testing. It promotes proactive security practices by identifying vulnerabilities early in the development lifecycle, helping organizations build more secure web applications. Here are some key features and capabilities of OWASP ZAP:
- Intercepting Proxy: OWASP ZAP acts as a proxy server, allowing users to intercept and inspect HTTP and HTTPS requests and responses between the web browser and the target application. This enables users to analyze and modify the application's traffic for security testing purposes.
- Active Scanning: OWASP ZAP can automatically scan web applications for common vulnerabilities, such as cross-site scripting (XSS), SQL injection, insecure direct object references, and more. It actively probes the application by sending various payloads and analyzing the responses to identify potential security flaws.
- Passive Scanning: In addition to active scanning, OWASP ZAP passively monitors application traffic and highlights potential security issues based on observed patterns or anomalies. This helps in identifying vulnerabilities that may not be easily detected through active scanning alone.
- Spidering and Crawling: OWASP ZAP can crawl and navigate through the application's structure to discover hidden or dynamically generated content. This helps in mapping the application's attack surface and ensuring comprehensive security testing coverage.
- Automated Attack Scripts: OWASP ZAP includes a scripting engine that allows users to create custom attack scripts or leverage existing ones to automate security tests. This can be particularly useful for repetitive or complex testing scenarios.
- Reporting and Integration: OWASP ZAP provides detailed reports summarizing the findings and vulnerabilities discovered during the scanning process. It supports various report formats and can be integrated into existing development and security workflows for seamless collaboration and issue tracking.
- Extensibility: OWASP ZAP offers a plugin architecture that allows users to extend its functionality and integrate with other security tools and systems. The community-driven nature of OWASP ZAP ensures a wide range of plugins and continuous updates to address emerging threats and vulnerabilities.
- Intercepting Proxy: OWASP ZAP acts as a proxy server, allowing users to intercept and inspect HTTP and HTTPS requests and responses between the web browser and the target application. This enables users to analyze and modify the application's traffic for security testing purposes.
- BeEF, short for Browser Exploitation Framework, is an open-source penetration testing tool designed to assess the security of web browsers and web applications. It focuses on exploiting client-side vulnerabilities and targeting users accessing web pages. The primary purpose of BeEF is to demonstrate the potential risks and vulnerabilities that exist within web browsers and how they can be leveraged for unauthorized access or malicious activities. It allows security professionals to assess the security posture of web applications and educate organizations about potential attack vectors. It's important to note that BeEF is a powerful tool that should only be used by authorized individuals in controlled environments for legitimate security testing purposes. Unauthorized use or malicious activities with BeEF can violate laws and regulations. It is primarily intended for security professionals to assess and improve the security of web applications, raise awareness about browser vulnerabilities, and reinforce security defenses. Here are some key features and capabilities of BeEF:
- Browser Exploitation: BeEF provides a range of client-side exploitation techniques to target vulnerabilities in web browsers. It can detect and exploit various weaknesses, such as cross-site scripting (XSS), HTML injection, and browser-specific vulnerabilities.
- Command and Control: BeEF establishes a command and control channel between the attacker and the compromised browser, allowing the attacker to interact with the victim's browser in real-time. This enables activities like manipulating web pages, executing JavaScript payloads, and gathering information about the target system.
- Web Application Security Assessment: BeEF can be used to assess the security of web applications by injecting malicious code into web pages. It helps identify vulnerabilities, such as reflected or stored XSS, that can be exploited to compromise users' browsers.
- Client-Side Reconnaissance: BeEF provides capabilities for gathering information about the victim's browser, including the installed plugins, operating system, and network details. This information can be valuable for understanding the target's environment and potential attack vectors.
- Extension Modules: BeEF supports a modular architecture, allowing the integration of additional functionalities through extensions. These modules provide advanced capabilities for specific attacks or techniques, extending the tool's capabilities.
- Browser Exploitation: BeEF provides a range of client-side exploitation techniques to target vulnerabilities in web browsers. It can detect and exploit various weaknesses, such as cross-site scripting (XSS), HTML injection, and browser-specific vulnerabilities.
- Core Impact is a commercial penetration testing and vulnerability assessment tool developed by Core Security. It is widely recognized as a comprehensive and powerful platform for conducting security assessments and simulating real-world attack scenarios. Core Impact is primarily used by professional penetration testers, security consultants, and ethical hackers to conduct thorough security assessments and identify vulnerabilities in systems and networks. It is regularly updated with the latest exploits and attack techniques, ensuring that testers can evaluate the effectiveness of defensive measures against emerging threats. Core Impact offers a range of features and capabilities that assist security professionals in assessing the security posture of systems, networks, and applications. Key features of Core Impact include:
- Exploit Development: Core Impact provides an extensive library of exploits and attack vectors that can be leveraged to simulate real-world attacks. It supports both known and zero-day vulnerabilities, enabling testers to assess the effectiveness of defenses against various types of threats.
- Remote Access: The tool allows testers to gain remote access to target systems, providing them with control over compromised machines and network devices. This feature helps assess the impact and potential consequences of successful attacks.
- Reporting and Analysis: Core Impact offers robust reporting capabilities, allowing testers to generate detailed reports summarizing vulnerabilities, exploitation attempts, and compromised systems. These reports aid in the communication of findings and recommendations to stakeholders.
- Social Engineering: Core Impact includes social engineering capabilities to assess the human element of security. It enables testers to simulate phishing attacks, perform email spoofing, and evaluate user susceptibility to social engineering techniques.
- Collaboration and Workflow: The platform supports collaboration among security teams, allowing testers to share findings, tasks, and results. It provides workflow management features to streamline the penetration testing process and enhance team productivity.
- Acunetix is a web application security testing tool that helps identify vulnerabilities in web applications and websites. It is widely used by security professionals, penetration testers, and developers to assess the security posture of web applications and prevent potential attacks. Overall, Acunetix is a robust web application security testing tool that assists organizations in identifying and addressing vulnerabilities in their web applications. It helps enhance the overall security posture, protect against potential attacks, and ensure compliance with security standards and regulations. Key features and capabilities of Acunetix include:
- Automated Scanning: Acunetix performs comprehensive automated scans of web applications to identify common vulnerabilities, including SQL injection, cross-site scripting (XSS), insecure server configurations, and more. It examines both the frontend and backend of web applications to uncover potential security weaknesses.
- Vulnerability Detection: The tool provides detailed vulnerability detection reports, highlighting the exact vulnerabilities found, their severity, and recommended remediation steps. It helps prioritize the identified vulnerabilities based on their potential impact and allows organizations to address them promptly.
- OWASP Top 10 Coverage: Acunetix focuses on the OWASP (Open Web Application Security Project) Top 10 vulnerabilities, which represent the most critical security risks commonly found in web applications. By addressing these vulnerabilities, organizations can significantly enhance the security of their web applications.
- Integration with Development Tools: Acunetix integrates with popular development tools, such as issue trackers and bug tracking systems, allowing developers to seamlessly track and address identified vulnerabilities within their development workflow.
- Compliance and Reporting: The tool offers compliance and reporting features, enabling organizations to meet regulatory requirements and industry standards. It generates comprehensive reports that can be shared with stakeholders and used for audits and compliance assessments.
- Advanced Scanning Techniques: Acunetix employs advanced scanning techniques, including manual intervention capabilities, to discover complex vulnerabilities that may require human interaction to exploit. This helps simulate real-world attack scenarios and provides more accurate results.
- Automated Scanning: Acunetix performs comprehensive automated scans of web applications to identify common vulnerabilities, including SQL injection, cross-site scripting (XSS), insecure server configurations, and more. It examines both the frontend and backend of web applications to uncover potential security weaknesses.
- WebInspect is a web application security testing tool developed by Micro Focus. It is designed to assess the security of web applications by identifying vulnerabilities and potential weaknesses in their code and configuration. WebInspect is used by security professionals, penetration testers, and developers to evaluate the security posture of web applications. It helps identify vulnerabilities and weaknesses that could be exploited by attackers, enabling organizations to proactively address these issues and enhance the overall security of their web applications. WebInspect utilizes a combination of automated scanning and manual testing techniques to comprehensively evaluate web applications for security flaws. Key features of WebInspect include:
- Automated Scanning: WebInspect employs automated scanning techniques to crawl through web applications, identifying potential vulnerabilities such as cross-site scripting (XSS), SQL injection, and insecure authentication mechanisms. It analyzes the application's structure, inputs, and responses to detect security weaknesses.
- Dynamic Application Analysis: The tool performs dynamic analysis of web applications, simulating real-world attack scenarios to discover vulnerabilities that may only manifest during runtime. It interacts with the application, submitting malicious input and observing the resulting behavior.
- Manual Testing Support: WebInspect allows testers to perform manual testing alongside automated scanning. Testers can customize the tool's settings, configure specific tests, and validate the identified vulnerabilities manually. This combination of automated and manual testing provides a more comprehensive assessment.
- Reporting and Analysis: WebInspect generates detailed reports summarizing identified vulnerabilities, their severity, and suggested remediation steps. These reports assist in prioritizing and addressing security issues.
- Integration and Collaboration: WebInspect can integrate with other security testing tools and development environments, allowing for streamlined workflows and collaboration between security teams and developers. It supports various integration options, such as issue tracking systems and continuous integration pipelines.
- AppSpider is a web application security testing tool developed by Rapid7. It is designed to assess the security of web applications by identifying vulnerabilities and potential risks within their code and configurations. AppSpider is used by security professionals, penetration testers, and developers to proactively assess and improve the security of web applications. By identifying vulnerabilities and risks, organizations can address these issues and strengthen their web application's security posture. AppSpider employs a combination of automated scanning and manual testing techniques to comprehensively evaluate web applications for security flaws. Key features of AppSpider include:
- Automated Scanning: AppSpider uses automated scanning capabilities to crawl through web applications, examining the application's structure, inputs, and responses to identify potential vulnerabilities. It tests for common security issues such as cross-site scripting (XSS), SQL injection, insecure direct object references, and more.
- Advanced Scanning Techniques: AppSpider utilizes various advanced scanning techniques, including dynamic application analysis, to simulate real-world attack scenarios. It interacts with the application and analyzes its behavior to identify vulnerabilities that may only be detectable during runtime.
- Manual Testing Support: AppSpider allows testers to supplement automated scanning with manual testing. Testers can customize scanning policies, manually verify identified vulnerabilities, and provide additional context to the assessment. This combination of automated and manual testing helps ensure a comprehensive security evaluation.
- Reporting and Analysis: AppSpider generates detailed reports that summarize the identified vulnerabilities, their severity, and recommended remediation steps. These reports assist in prioritizing and addressing security issues effectively.
- Integration and Collaboration: AppSpider offers integration capabilities with other security tools and development environments, enabling seamless collaboration between security teams and developers. It supports integrations with issue tracking systems, allowing for streamlined workflows and efficient remediation processes.
- AppScan, also known as IBM Security AppScan, is a web application security testing tool developed by IBM. It is designed to identify and assess vulnerabilities in web applications to help organizations improve their security posture. AppScan is widely used by security professionals, penetration testers, and developers to assess and improve the security of web applications. By identifying vulnerabilities and providing actionable recommendations, AppScan helps organizations enhance their application security and protect against potential attacks. AppScan offers a range of features and capabilities to facilitate comprehensive security testing of web applications. Some key features of AppScan include:
- Automated Scanning: AppScan uses automated scanning techniques to crawl through web applications and identify potential security vulnerabilities. It analyzes the application's structure, inputs, and responses to detect common vulnerabilities such as cross-site scripting (XSS), SQL injection, and insecure authentication mechanisms.
- Interactive Application Security Testing (IAST): AppScan supports IAST, which allows for deeper analysis by monitoring the application at runtime. It helps identify vulnerabilities that may only manifest during execution and provides additional context to the assessment.
- Secure SDLC Integration: AppScan integrates with various stages of the Secure Software Development Lifecycle (SDLC), including development environments and build systems. This integration helps developers identify and remediate vulnerabilities early in the development process.
- Manual Testing Support: AppScan provides capabilities for manual testing alongside automated scanning. Testers can customize scanning policies, manually verify identified vulnerabilities, and provide additional context to the assessment.
- Reporting and Analysis: AppScan generates detailed reports summarizing identified vulnerabilities, their severity, and recommended remediation steps. The reports help prioritize and address security issues effectively.
- Integration and Collaboration: AppScan supports integration with other security tools and development environments, allowing for streamlined workflows and collaboration between security teams and developers. It facilitates the sharing of findings and supports the synchronization of vulnerability data with issue tracking systems.
- Burp Suite is a popular and widely used integrated platform for web application security testing. Developed by PortSwigger, Burp Suite provides a comprehensive set of tools that assist security professionals in performing various security assessments, such as penetration testing, vulnerability scanning, and web application security analysis. Burp Suite is highly customizable and extensible, allowing users to add their own plugins or extensions to enhance its functionality and tailor it to their specific needs. It is widely used by security professionals, penetration testers, and developers to identify and mitigate security vulnerabilities in web applications. Burp Suite consists of several components that work together to support the entire security testing process:
- Interactive Application Security Testing (IAST) is a dynamic application security testing technique that combines elements of both static and dynamic analysis. Unlike traditional dynamic application security testing (DAST) tools, which operate externally by interacting with the running application, IAST tools are embedded within the application itself. IAST instruments the application's code or runtime environment to monitor and analyze the application's behavior during runtime. It captures and analyzes application interactions, including user inputs, method calls, and data flows, to identify potential security vulnerabilities and weaknesses. By residing within the application, IAST tools have deeper visibility into the application's internal behavior, making them capable of providing more accurate and contextual security findings.
- Seeker is an interactive application security testing (IAST) tool designed to enhance the security of web applications during the development process. It is specifically focused on identifying and helping remediate security vulnerabilities related to authentication and authorization.Seeker operates as a security testing proxy that sits between the user's browser and the application being tested. It analyzes the application's behavior in real-time, monitoring and capturing various user actions and requests. Seeker provides immediate feedback to developers by identifying potential security weaknesses and suggesting remediation steps directly within the development environment. Seeker is a valuable tool for developers and security teams aiming to strengthen the security of their web applications by proactively addressing authentication and authorization vulnerabilities. It enables a more efficient and collaborative approach to secure software development, ultimately reducing the risk of unauthorized access and data breaches. Key features and benefits of Seeker include:
- Real-time Vulnerability Identification: Seeker actively scans and analyzes the application's authentication and authorization mechanisms in real-time, allowing for the immediate detection of security vulnerabilities during development.
- Contextual Security Analysis: Seeker provides contextual insights by analyzing the application's behavior within the user's session. It examines user interactions, request flows, and security-related parameters to identify potential weaknesses and security flaws.
- Interactive Remediation Guidance: Seeker offers actionable recommendations to developers on how to remediate the identified vulnerabilities. It provides specific code-level guidance and suggestions to address the security issues effectively.
- Integration with Development Environment: Seeker seamlessly integrates with popular development environments, such as IDEs and CI/CD pipelines, allowing developers to receive security feedback within their familiar workflows. This integration promotes a shift-left approach to security, enabling early vulnerability detection and timely remediation.
- Developer-friendly Interface: Seeker provides an intuitive and user-friendly interface that facilitates easy navigation and interpretation of the identified security vulnerabilities. It presents clear explanations and prioritizes issues based on their severity, enabling developers to focus on critical weaknesses first.
- Continuous Security Testing: Seeker supports continuous security testing by monitoring and analyzing the application's authentication and authorization mechanisms throughout the software development lifecycle. It can be incorporated into automated testing processes, ensuring that security assessments are performed consistently.
- Enhanced Developer Productivity: Seeker empowers developers to understand the security implications of their code and provides them with actionable insights to fix vulnerabilities early on. This helps improve developer productivity by fostering a proactive and security-conscious development environment.
- Seeker is an interactive application security testing (IAST) tool designed to enhance the security of web applications during the development process. It is specifically focused on identifying and helping remediate security vulnerabilities related to authentication and authorization.Seeker operates as a security testing proxy that sits between the user's browser and the application being tested. It analyzes the application's behavior in real-time, monitoring and capturing various user actions and requests. Seeker provides immediate feedback to developers by identifying potential security weaknesses and suggesting remediation steps directly within the development environment. Seeker is a valuable tool for developers and security teams aiming to strengthen the security of their web applications by proactively addressing authentication and authorization vulnerabilities. It enables a more efficient and collaborative approach to secure software development, ultimately reducing the risk of unauthorized access and data breaches. Key features and benefits of Seeker include:
- Thick Client penetration testing refers to the assessment and evaluation of the security of applications that run on desktop or client-side platforms, commonly known as thick clients. Unlike web applications that run in a browser, thick clients are standalone software applications installed and executed on the user's local machine. During thick client penetration testing, security professionals simulate attacks on the client-side application to identify vulnerabilities, security weaknesses, and potential entry points that attackers could exploit. This type of testing focuses on uncovering security flaws within the application itself, as well as any interactions it has with the underlying operating system and external resources.
- Echo Mirage allows us to see and edit the data being exchanged be it encrypted or unencrypted session. In the event wherein a user’s system has been compromised by an exploit/payload, Echo Mirage can be used to hook into the compromised process, and the communication between the attacker’s machine and the victim’s machine can be intercepted. This can give insight to what kind of information the attacker is looking for on the victim’s machine. Few more features of Echo Mirage:
- Traffic Log: Traffic log, as the name suggests, keeps a detailed history of the entire communication that took place. We can, at any given point of time, go back to the logs and re-check any data that we might’ve missed.
- Rules: Echo Mirage has another feature called rules. This feature enables us to make custom rules that would intercept certain calls made by the application. Rules can be created to intercept only the inbound traffic or outbound traffic, or both made to a certain address on a particular port. Rules can also be made to define pre-defined actions and search for certain keywords based on muti-lined, case sensitivity, single-lined, extended or anchored. New rules can be made by clicking on the Green Plus Icon on the top. Echo Mirage also gives us the ability to export the user defined rules or import new rules.
- Wireshark is a widely used open-source network protocol analyzer. It is designed to capture, analyze, and inspect network traffic in real-time. Wireshark allows users to examine packets of data flowing over a network, providing insights into the network protocols, communication patterns, and potential security issues. Wireshark is widely used by network administrators, security professionals, and developers for tasks such as network troubleshooting, protocol analysis, network performance optimization, and network security assessment. Its open-source nature and extensive community support make it a versatile tool in the field of network analysis and security. Key features of Wireshark include:
- Packet Capture: Wireshark captures network packets from a specified network interface or from a previously captured file. It supports various capture options, allowing users to filter and capture specific types of network traffic.
- Protocol Analysis: The captured packets are then dissected and displayed in a user-friendly interface. Wireshark supports a vast range of network protocols and provides detailed protocol analysis, enabling users to examine individual packets, protocol headers, and payload data.
- Filtering and Search: Wireshark offers powerful filtering capabilities, allowing users to focus on specific packets of interest. Filters can be based on criteria such as source/destination IP addresses, port numbers, protocol types, and other packet attributes. This helps in narrowing down the analysis to relevant traffic.
- Real-Time Monitoring: Wireshark provides real-time packet monitoring, allowing users to observe network activity as it happens. This feature is valuable for troubleshooting network issues, analyzing performance bottlenecks, or detecting abnormal network behavior.
- Decryption Support: Wireshark can decrypt encrypted network traffic when provided with the appropriate encryption keys or certificates. This enables analysis of encrypted protocols such as SSL/TLS.
Protocol Reconstruction: Wireshark can reconstruct and display higher-level protocols, such as HTTP, DNS, FTP, or VoIP sessions. This allows users to view the content and analyze the behavior of specific applications running on the network. - Export and Reporting: Wireshark supports exporting captured packets to various file formats for further analysis or sharing with others. It also provides options to generate detailed reports summarizing network statistics, protocol usage, and identified issues.
- Process Hacker is an open-source task manager and system monitoring utility for Windows operating systems. It provides advanced functionality beyond the default Windows Task Manager, allowing users to monitor and manage processes, services, network connections, and more. Process Hacker is popular among power users, system administrators, security analysts, and developers who require a comprehensive and customizable task manager utility for in-depth system monitoring and process management on Windows platforms. Key features of Process Hacker include:
- Process Management: Process Hacker allows users to view and manage running processes on their system. It provides detailed information about each process, including CPU and memory usage, parent-child relationships, process properties, and the ability to terminate or manipulate processes.
- Services Management: The utility enables users to monitor and control system services. It provides a comprehensive view of installed services, their status, startup type, and associated details. Users can start, stop, or modify service properties using Process Hacker.
- Network Connections: Process Hacker displays active network connections made by processes. Users can view the local and remote addresses, protocols, and associated process IDs. This feature helps identify network-related activities and potential security concerns.
- System Performance Monitoring: The utility provides real-time monitoring of system performance metrics such as CPU usage, memory utilization, disk activity, and network bandwidth. Users can analyze system performance trends and identify resource-intensive processes.
- Process Profiling: Process Hacker offers process profiling capabilities, allowing users to trace and monitor the execution of specific processes. It helps identify performance bottlenecks, analyze resource usage, and detect potential issues within applications.
- System-Wide Search: Users can search for specific processes, services, handles, or modules across the entire system. This feature facilitates quick identification and navigation to relevant components.
- Extended Functionality: Process Hacker includes additional features like process injection, memory editing, system monitoring, and advanced debugging capabilities, making it a versatile tool for system analysis and troubleshooting.
- WinHex is a powerful hexadecimal editor and disk editor/inspector developed by X-Ways Software Technology. It is primarily used for low-level data analysis, disk editing, and data recovery tasks on various storage media and file systems. WinHex is widely used by computer forensic professionals, data recovery specialists, system administrators, and security analysts who require advanced capabilities for disk-level analysis, data editing, and file system examination. Its versatility and comprehensive feature set make it a valuable tool in various data-related tasks. Key features of WinHex include:
- Hexadecimal Editing: WinHex allows users to view and edit files at the binary level, displaying the data in hexadecimal and ASCII formats. Users can directly modify individual bytes, characters, or data structures within files.
- Disk Editing and Data Recovery: WinHex provides disk-level editing capabilities, allowing users to inspect and modify disk sectors, partitions, and file systems. It is commonly used in forensic investigations, data recovery scenarios, and disk analysis tasks.
- File and Disk Analysis: The tool offers advanced file and disk analysis features, enabling users to examine the internal structures and metadata of various file formats. It supports parsing and displaying information from different file types, such as executables, archives, databases, and more.
- Data Carving: WinHex includes data carving functionality, which allows users to search for and extract specific file types or data patterns from raw disk or file system images. This feature is particularly useful in forensic investigations or when recovering deleted files.
- Data Encryption and Password Recovery: WinHex includes utilities for data encryption, decryption, and password recovery. It supports various encryption algorithms and provides options for recovering lost or forgotten passwords.
- Disk Cloning and Imaging: The tool enables users to create disk images or clone entire disks, preserving the data and structure for forensic or backup purposes. It supports various image file formats and compression options.
- File Comparison and Validation: WinHex offers file comparison features, allowing users to compare the contents of two files or disk sectors and identify differences. It also supports file integrity checking and hash calculation.
- Echo Mirage allows us to see and edit the data being exchanged be it encrypted or unencrypted session. In the event wherein a user’s system has been compromised by an exploit/payload, Echo Mirage can be used to hook into the compromised process, and the communication between the attacker’s machine and the victim’s machine can be intercepted. This can give insight to what kind of information the attacker is looking for on the victim’s machine. Few more features of Echo Mirage:
- Mobile Application penetration testing, also known as mobile app security testing, is a process of assessing the security posture of mobile applications. It involves identifying vulnerabilities, weaknesses, and potential security risks in the application, with the goal of improving the overall security and resilience of the mobile app. Mobile application penetration testing is crucial in ensuring the security of mobile apps, protecting sensitive user data, and mitigating potential risks. It helps identify vulnerabilities that could be exploited by attackers and provides recommendations for strengthening the app's security controls and defenses.
- NowSecure Workstation is a comprehensive mobile app security testing solution provided by NowSecure. It is a software package designed to enable organizations to perform automated and manual security testing of mobile applications. NowSecure Workstation includes a suite of tools and capabilities that help identify vulnerabilities, assess risks, and improve the security of mobile apps. NowSecure Workstation is designed to provide organizations with a comprehensive solution for mobile app security testing, allowing them to identify and address vulnerabilities before the apps are deployed. It helps ensure the security and integrity of mobile applications and protects sensitive data from potential threats. Key features and capabilities of NowSecure Workstation may include:
- Static Analysis: The workstation provides static analysis capabilities to analyze the source code of mobile applications. It scans the code for potential vulnerabilities, insecure coding practices, and other security issues.
- Dynamic Analysis: NowSecure Workstation allows for dynamic analysis, where mobile apps are tested in real-time on physical or virtual devices. It simulates real-world usage scenarios, monitors network communications, and identifies vulnerabilities that may only be detectable during runtime.
- Behavioral Analysis: The workstation employs behavioral analysis techniques to identify suspicious or malicious behaviors exhibited by mobile applications. It helps detect malware, unauthorized data access, and other security risks.
- Manual Testing Support: NowSecure Workstation provides an interface for manual security testing and assessment of mobile applications. Security analysts can explore the app's functionalities, interact with it, and manually identify vulnerabilities that automated tools may have missed.
- Reporting and Remediation: The workstation generates detailed reports that outline the identified vulnerabilities, their severity, and recommended remediation steps. These reports assist developers and security teams in understanding the security risks and prioritizing fixes.
- Integration and Collaboration: NowSecure Workstation can integrate with development environments, issue tracking systems, and other security tools to streamline the testing and remediation process. It facilitates collaboration between development and security teams.
- Burp Suite is a popular and widely used integrated platform for web application security testing. Developed by PortSwigger, Burp Suite provides a comprehensive set of tools that assist security professionals in performing various security assessments, such as penetration testing, vulnerability scanning, and web application security analysis. Burp Suite is highly customizable and extensible, allowing users to add their own plugins or extensions to enhance its functionality and tailor it to their specific needs. It is widely used by security professionals, penetration testers, and developers to identify and mitigate security vulnerabilities in web applications.
- Wireshark is a widely used open-source network protocol analyzer. It is designed to capture, analyze, and inspect network traffic in real-time. Wireshark allows users to examine packets of data flowing over a network, providing insights into the network protocols, communication patterns, and potential security issues. Wireshark is widely used by network administrators, security professionals, and developers for tasks such as network troubleshooting, protocol analysis, network performance optimization, and network security assessment. Its open-source nature and extensive community support make it a versatile tool in the field of network analysis and security.
- Dex2jar is a popular open-source tool used in the field of Android application security and reverse engineering. It is designed to convert Android APK (Android Application Package) files, which contain compiled code in the Dalvik Executable (DEX) format, into Java Archive (JAR) files that can be easily analyzed and decompiled. Dex2jar is widely used by security researchers, Android app developers, and professionals involved in Android application analysis, reverse engineering, and security auditing. It helps in identifying vulnerabilities, understanding application behavior, and improving the security of Android applications. However, it's important to note that Dex2jar should be used responsibly and ethically, respecting the intellectual property rights and privacy concerns associated with the analyzed applications. Key features of Dex2jar include:
- DEX to JAR Conversion: Dex2jar allows users to convert Android APK files into JAR files, which contain the original Java bytecode of the application. This conversion makes it easier to analyze and understand the code structure, logic, and functionality of the Android application.
- Decompilation: Once the APK file is converted to JAR format, Dex2jar can be used in conjunction with Java decompilers (such as JD-GUI or Fernflower) to decompile the bytecode into readable Java source code. This enables reverse engineers and security analysts to gain insights into the inner workings of the application.
- Debugging and Analysis: Dex2jar helps in the debugging and analysis of Android applications by providing a more accessible and human-readable representation of the code. This facilitates the identification of vulnerabilities, security flaws, or suspicious behavior within the application.
- Third-Party Library Extraction: Dex2jar can extract and decompile third-party libraries included in the APK, allowing developers and security professionals to understand the functionality and potential security implications of these libraries.
- Integration with Other Tools: Dex2jar can be integrated with other analysis and reverse engineering tools, such as IDA Pro or Burp Suite, to enhance the analysis capabilities and provide a more comprehensive view of the application's security posture.
- ApkTool is an open-source utility commonly used in Android application reverse engineering and modification. It enables users to decompile and analyze Android APK (Android Application Package) files, extract resources, and make modifications to the application's code, resources, and configuration files. ApkTool is widely used by security researchers, Android app developers, and enthusiasts involved in Android application analysis, customization, and modification. However, it's important to note that ApkTool should be used responsibly and in compliance with applicable laws and regulations to respect the intellectual property rights of the original application developers. Key features of ApkTool include:
- Decompilation: ApkTool allows users to decompile Android APK files into their corresponding source code and resources. This process involves extracting the Dalvik Executable (DEX) bytecode and converting it into readable Java source code, making it easier to understand and analyze the application's functionality.
- Resource Extraction: The tool enables the extraction of resources, such as images, audio files, layouts, and other assets, from the APK. This allows developers and security analysts to examine and modify the resources used by the application.
- Resource Modification: ApkTool provides the ability to modify extracted resources, such as XML files, layouts, and manifest files. This allows for customization, localization, or fixing of issues within the application.
Smali Code Editing: ApkTool allows users to view and edit the Smali code, which is the assembly-like bytecode representation of the Android application's code. Users can make modifications to the Smali code to implement desired changes or troubleshoot issues. - Rebuilding and Repackaging: Once modifications are made, ApkTool supports the process of rebuilding the modified resources and code back into a new APK file. This enables the creation of a modified version of the application for testing or customization purposes.
- Integration with Other Tools: ApkTool can be integrated with other analysis and reverse engineering tools to enhance the analysis capabilities and provide a more comprehensive view of the application's structure and behavior.
- JD-GUI is a popular standalone Java decompiler tool used for reverse engineering Java applications. It allows users to decompile compiled Java bytecode (in the form of JAR or CLASS files) into readable Java source code, providing insights into the original implementation, logic, and structure of the application. JD-GUI is widely used by developers, security researchers, and professionals involved in reverse engineering and code analysis. It assists in understanding third-party libraries, troubleshooting issues, or gaining insights into the implementation details of Java applications. However, it's important to note that the use of JD-GUI should comply with legal and ethical considerations, respecting intellectual property rights and the terms of any applicable licenses. Key features of JD-GUI include:
- Decompilation: JD-GUI can decompile Java bytecode files and display the decompiled source code in a user-friendly graphical interface. It reconstructs the Java code from the compiled bytecode, making it easier for developers and security analysts to understand the application's functionality and behavior.
- Graphical User Interface: JD-GUI provides a visual interface for browsing and analyzing decompiled Java code. It offers features like syntax highlighting, code folding, navigation through classes and methods, and displaying class inheritance hierarchies.
- Code Analysis: The tool allows users to navigate through the decompiled code, inspect class structures, and analyze the relationships between classes and methods. It provides a high-level overview of the application's architecture and allows users to examine individual code segments in detail.
- Exporting Decompiled Code: JD-GUI enables users to export the decompiled Java code as text files, making it possible to save and further analyze the decompiled source code using other tools or editors.
- Integration with Decompiler Plugins: JD-GUI supports the use of additional plugins that enhance its functionality. These plugins can provide additional features, such as decompiling obfuscated code or integrating with other tools for further analysis.
- NowSecure Workstation is a comprehensive mobile app security testing solution provided by NowSecure. It is a software package designed to enable organizations to perform automated and manual security testing of mobile applications. NowSecure Workstation includes a suite of tools and capabilities that help identify vulnerabilities, assess risks, and improve the security of mobile apps. NowSecure Workstation is designed to provide organizations with a comprehensive solution for mobile app security testing, allowing them to identify and address vulnerabilities before the apps are deployed. It helps ensure the security and integrity of mobile applications and protects sensitive data from potential threats. Key features and capabilities of NowSecure Workstation may include:
- Database security assessment refers to the process of evaluating the security measures, controls, and vulnerabilities within a database environment. It involves assessing the database infrastructure, configurations, user access controls, data encryption, auditing mechanisms, and other security-related aspects to identify potential weaknesses and risks. A comprehensive database security assessment helps organizations identify and address vulnerabilities and weaknesses within their database systems. It assists in mitigating risks, protecting sensitive data, ensuring compliance, and maintaining the overall security of the organization's data assets.
- Imperva Scuba empowers organizations with the security information it needs to reduce risk and prioritize actions. Preventing organization next data breach starts with taking care of their data security hygiene. It is available for Microsoft Windows, Apple MacOS, Linux (x32), and Linux (x64), Scuba offers over 2,300 assessment tests for Oracle, Microsoft SQL server, SAP Sybase, IBM DB2, PostgreSQL, Informix and MySQL. With this tool it can:
- Scan enterprise databases for vulnerabilities and misconfiguration
- Know the risks of databases
- Get recommendations on how to mitigate identified issues
- RazorSQL is a popular and comprehensive database management and SQL query tool. It provides a wide range of features and capabilities to facilitate database administration, development, and querying tasks across various database systems. RazorSQL is widely used by database administrators, developers, and analysts for their database management, querying, and development needs. RazorSQL is not specifically designed as a dedicated penetration testing tool, it can still assist in certain aspects of a penetration testing assessment. While RazorSQL can support certain aspects of penetration testing, it's important to note that it lacks specialized features found in dedicated penetration testing tools. For a comprehensive and thorough penetration test, it is recommended to use a combination of dedicated penetration testing tools that offer a broader range of functionalities specific to security testing. Here are some ways in which RazorSQL can be useful during penetration testing:
- SQL Injection Testing: RazorSQL's SQL editor allows penetration tester to craft and execute SQL queries against a target database. This can be useful for testing SQL injection vulnerabilities by attempting to exploit them and analyzing the results.
- Database Enumeration: RazorSQL's database browser feature enables penetration tester to browse through the tables, views, and other database objects. This can help in discovering sensitive data, identifying potential attack vectors, and understanding the database structure during a penetration test.
- Data Manipulation: RazorSQL allows for data editing and manipulation within databases. This can be useful for testing scenarios where unauthorized modifications to data could lead to security breaches or for analyzing the impact of data manipulation attacks.
- Query Analysis: By analyzing the SQL queries executed by the target application, penetration tester can gain insights into its underlying logic and identify potential vulnerabilities or security weaknesses.
- Imperva Scuba empowers organizations with the security information it needs to reduce risk and prioritize actions. Preventing organization next data breach starts with taking care of their data security hygiene. It is available for Microsoft Windows, Apple MacOS, Linux (x32), and Linux (x64), Scuba offers over 2,300 assessment tests for Oracle, Microsoft SQL server, SAP Sybase, IBM DB2, PostgreSQL, Informix and MySQL. With this tool it can:
[ Download Sample PenTest Report ]
References:
https://owasp.org
https://www.kali.org
https://mas.owasp.org
https://www.isecom.org/OSSTMM.3.pdf
https://www.offsec.com/metasploit-unleashed
http://www.pentest-standard.org/index.php/Main_Page
https://csrc.nist.gov/publications/detail/sp/800-115/final
https://sourceforge.net/projects/isstf/files/issaf%20document/issaf0.1
https://www.pcisecuritystandards.org/documents/Penetration-Testing-Guidance-v1_1.pdf
https://csrc.nist.gov/presentations/2012/security-testing-and-assessment-methodologies
https://www.nist.gov/news-events/news/2018/04/nist-releases-version-11-its-popular-cybersecurity-framework