Zero Trust Architecture (ZTA) is a security framework and approach that challenges the traditional perimeter-based security model. It is based on the principle of "never trust, always verify" and operates under the assumption that no user or device should be automatically trusted, whether they are inside or outside the organization's network perimeter.
In a Zero Trust Architecture, every user, device, and network resource is treated as potentially untrusted and requires continuous verification and authentication. The key concept is to authenticate and authorize access based on multiple factors, such as user identity, device health, location, and behavior, before granting access to resources.
Key principles Zero Trust (ZT)
- Explicit Verification: Ensure authentication and authorization by considering a comprehensive set of data points, such as user identity, location, device health, service or workload, data classification, and anomalies.
- Least-Privilege Access: Restrict user access through just-in-time and just-enough access (JIT/JEA), risk-based adaptive policies, and data protection measures to enhance security while maintaining productivity.
- Assume Breach: Mitigate the impact of security incidents by minimizing the potential scope and segmenting access. Employ end-to-end encryption, leverage analytics for visibility, facilitate threat detection, and enhance overall defense capabilities.
Instead of relying on the assumption of safety behind the corporate firewall, the Zero Trust model takes a different approach by assuming a breach and treating each request as if it originates from an untrusted network. This mindset of "never trust, always verify" guides the implementation of strong authentication, authorization, and encryption for every access request, regardless of its origin or the resource it intends to access. By applying microsegmentation and least-privilege access principles, the model aims to limit lateral movement within the network. Additionally, the utilization of comprehensive intelligence and analytics enables real-time detection and response to anomalies, enhancing overall security posture.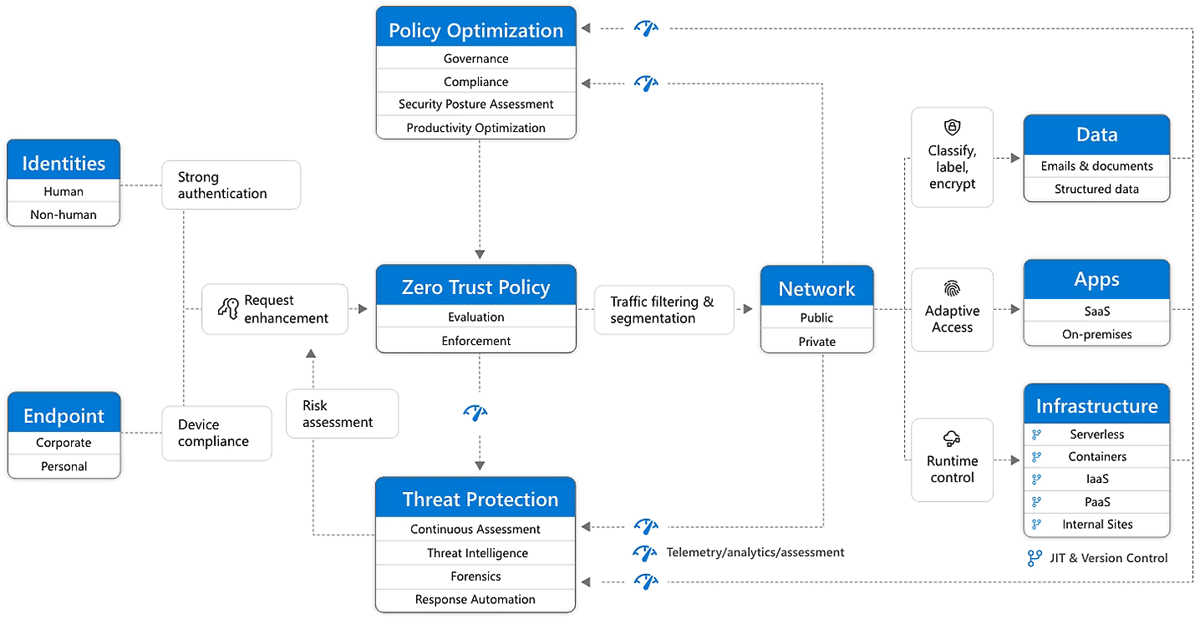
Key principles and components of Zero Trust Architecture (ZTA)
- Identity and Access Management (IAM): Strong user authentication and authorization mechanisms are essential. This includes multifactor authentication (MFA), identity federation, and role-based access controls to ensure that only authorized individuals have access to resources.
- Device Trust: Devices accessing the network must be assessed for security posture, compliance, and health status before being granted access. This can involve enforcing security policies, such as ensuring up-to-date software patches, running antivirus software, and having secure configurations.
- Network Segmentation: Network segmentation is crucial to create microperimeters and limit lateral movement within the network. By segmenting the network into smaller, isolated zones, organizations can contain potential threats and minimize the impact of a security breach.
- Least Privilege: Users and devices should only be granted the minimum level of access necessary to perform their tasks. This principle reduces the attack surface and limits the potential damage that can be caused by compromised accounts or devices.
- Continuous Monitoring and Analytics: Zero Trust Architecture requires continuous monitoring of user and device behavior, network traffic, and security events. This allows for real-time detection of anomalies, suspicious activities, or potential security breaches, enabling swift response and remediation.
- Automation and Orchestration: Zero Trust Architecture leverages automation and orchestration to streamline security processes, reduce human errors, and enforce consistent security policies across the organization. This includes automating security controls, threat detection, and incident response actions.
The goal of Zero Trust Architecture is to improve overall security posture by assuming that threats exist both inside and outside the network perimeter. By adopting this approach, organizations can enhance their security, protect sensitive data, and reduce the risk of unauthorized access and data breaches.
Zero Trust (ZT) and Zero Trust Architecture (ZTA)
Zero Trust (ZT) and Zero Trust Architecture (ZTA) are security concepts and approaches that challenge the traditional perimeter-based security model. They advocate for a more proactive and holistic approach to security by assuming that no user or device should be inherently trusted, even if they are inside the organization's network perimeter. The core principle of Zero Trust is to verify and authenticate every user, device, and network interaction, regardless of their location or context.
Zero Trust is based on the principle of "never trust, always verify." It assumes that potential threats exist both inside and outside the network, and access should only be granted on a need-to-know basis and with appropriate levels of authentication. Zero Trust aims to minimize the potential attack surface, reduce the risk of lateral movement within the network, and prevent unauthorized access to sensitive resources.
Zero Trust Architecture (ZTA) is the implementation of the Zero Trust concept in an organization's network and security infrastructure. It involves designing and deploying security controls and technologies that enforce the Zero Trust principles. This may include multifactor authentication (MFA), identity and access management (IAM) solutions, encryption, micro-segmentation, network segmentation, continuous monitoring, and other security measures.
ZTA focuses on establishing granular access controls, strong authentication mechanisms, and continuous monitoring of user behavior and network activities. It emphasizes the use of contextual information, risk assessments, and dynamic policies to make access decisions. By implementing ZTA, organizations can achieve a more robust and resilient security posture that aligns with the evolving threat landscape and the distributed nature of modern IT environments.
In summary, Zero Trust (ZT) is a security mindset and approach that challenges the concept of inherent trust in network environments. Zero Trust Architecture (ZTA) is the implementation of the Zero Trust principles through the deployment of appropriate security controls and technologies. Together, they aim to enhance security, minimize the attack surface, and protect critical assets in today's dynamic and interconnected digital landscape.
Zero Trust Maturity Model (ZTMM)
The CISA Zero Trust Maturity Model (ZTMM) serves as a comprehensive guide to continually enhance organization's security program. By adopting a Zero Trust approach, organization can optimize the effectiveness of security investments and effectively address cyber risks.
In order to effectively defend against cyber threats, organizations need to prioritize speed, agility, and resiliency. This involves staying one step ahead of adversaries, building strong response capabilities to recover quickly, and increasing the overall cost and effort for attackers. While there are different Zero Trust (ZT) standards available, such as those from NIST, NSA, and DoD, organizations often face the challenge of implementing Zero Trust incrementally to mature their overall security capabilities. This is where the ZTMM proves valuable, as it provides a roadmap for organizations to enhance their Zero Trust maturity.
By following the ZTMM, organizations can systematically develop their Zero Trust capabilities and gradually improve their security posture. This model offers guidance on the key steps and milestones required to achieve higher levels of Zero Trust maturity. It helps organizations assess their current state, identify gaps, and establish a strategic plan to implement Zero Trust principles in a phased and structured manner.
By leveraging the ZTMM, organizations can effectively navigate the complexities of implementing Zero Trust and make informed decisions regarding the adoption of appropriate security controls, technologies, and practices. This allows organizations to enhance their security defenses, protect critical assets, and mitigate risks in an evolving threat landscape.
Three Stages Zero Trust Maturity Model (ZTMM)
The Zero Trust Maturity Model is a framework that helps organizations assess and measure their progress in implementing a Zero Trust Architecture. It provides a roadmap for organizations to follow as they mature their security practices and move towards a Zero Trust approach.
The Zero Trust Maturity Model consists of three stages: Traditional, Advanced, and Optimal, which are used to assess the maturity level of an organization's Zero Trust architecture.
- Traditional Stage of Zero Trust Maturity Model: In the traditional stage, the organization relies on legacy systems and manual configurations. Attributes are manually assigned to assets, and incident response and mitigation deployment are also performed manually. There is a lack of cross-pillar coordination, limited centralized visibility, and identity control is not centralized. Least-privilege changes are made based on posture assessments, but they are not fully automated.
- Advanced Stage of Zero Trust Maturity Model: In the advanced stage, the organization achieves some level of cross-pillar coordination. There is centralized visibility into the network, devices, applications, and data. Identity control is centralized, allowing for better control and management of user access. Incident response processes are predefined to some extent, and there is a proactive approach to least-privilege changes based on posture assessments. Automation plays a role in improving efficiency and effectiveness.
- Optimal Stage of Zero Trust Maturity Model: In the optimal stage, the organization has fully embraced automation and advanced capabilities. Attributes are automatically assigned to assets and resources, enabling dynamic policies based on automated and observed triggers. Assets have self-enumerating dependencies, allowing for dynamic least privilege access. The organization aligns with open standards to ensure cross-pillar interoperability. Centralized visibility is achieved, including historian functionality for point-in-time recollection of system state, aiding in forensic analysis and incident response.
By progressing through these stages, organizations can gradually enhance their Zero Trust architecture, moving from manual processes and limited visibility to automated, dynamic, and highly efficient security practices.
The Zero Trust Maturity Model serves as a guide for organizations to assess their current security posture, identify gaps, and define a roadmap for enhancing their security practices. It emphasizes the importance of incremental progress and continuous improvement in adopting Zero Trust principles. It's worth noting that the specific details of the Zero Trust Maturity Model may vary depending on the framework or methodology used. Organizations can choose the model that aligns best with their goals and requirements to guide their Zero Trust journey.
The Five Pillars of Zero Trust Model
This section will discuss the implementation of the Five Pillars of the Zero Trust model using the Zero Trust Maturity Model (ZTMM). Each pillar represents a different aspect of Zero Trust Architecture (ZTA) and has various levels of maturity in terms of implementation.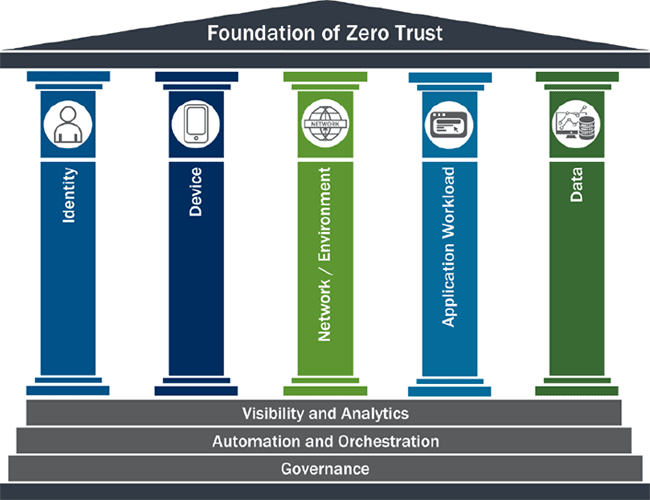
- Identity - The First Pillar of ZTA Model
- Traditional ZTA Maturity Level for Identity: At the traditional cybersecurity maturity level, identity is authenticated using passwords or multi-factor authentication (MFA). Risk assessments are limited, and user activities are segmented based on basic and static attributes. Identity audits are conducted manually, and credential policies are enforced using static technical measures.
- Advanced ZTA Maturity Level for Identity: In the advanced maturity level, organizations automate identity verification and use MFA extensively. Some cloud environments are monitored along with on-premises systems. Risk assessments are conducted using simple analytics and static rules. Automated access revocation is implemented based on policies, and shared accounts are eliminated.
- Optimal ZTA Maturity Level for Identity: At the optimal maturity level, continuous identity validation is achieved, going beyond the initial granting of access. Real-time user behavior analysis is performed using machine learning algorithms to determine risk and provide ongoing protection. User visibility is centralized, and high-fidelity attributes and user and entity behavior analytics (UEBA) are utilized. Dynamic user profiling, just-in-time and just-enough access controls, and full automation of policy enforcement are implemented.
- Traditional ZTA Maturity Level for Identity: At the traditional cybersecurity maturity level, identity is authenticated using passwords or multi-factor authentication (MFA). Risk assessments are limited, and user activities are segmented based on basic and static attributes. Identity audits are conducted manually, and credential policies are enforced using static technical measures.
- Device - The Second Pillar of ZTA Model
- Traditional ZTA Maturity Level for Device: In the traditional maturity level, there is limited visibility into device compliance. Device acquisition channels are manually defined and enforced, and device inventories are periodically reconciled against sanctioned lists. Device retirement requires thorough sanitation to remove residual access and data.
- Advanced ZTA Maturity Level for Device: In the advanced maturity level, automation and constant monitoring are employed. Assets are managed using automated methods, vulnerabilities are identified, and patching is performed. Device inventories are reconciled against sanctioned lists, and non-compliant components are isolated. Devices support modern security functions in hardware.
- Optimal ZTA Maturity Level for Device: At the optimal maturity level, device security posture is continuously monitored and validated. Real-time risk analytics about devices are used to control data access. Asset and vulnerability management are integrated across all environments, including cloud and remote workspaces. Endpoint detection and response (EDR) assessments are performed continuously. Device capacity and deployment utilize continuous integration and continuous deployment (CI/CD) principles with dynamic scaling. Data access is granted without resident plain-text copies, reducing supply chain risks.
- Traditional ZTA Maturity Level for Device: In the traditional maturity level, there is limited visibility into device compliance. Device acquisition channels are manually defined and enforced, and device inventories are periodically reconciled against sanctioned lists. Device retirement requires thorough sanitation to remove residual access and data.
- Network - The Third Pillar of ZTA Model
- Traditional ZTA Maturity Level for Network: In the traditional maturity level, network architecture relies on a large perimeter or macro-segmentation. Threat protection is primarily based on known threats and static traffic filtering, with minimal internal traffic encryption. Networks, devices, and services are manually identified and sanctioned, and unauthorized entities are discovered and remediated manually.
- Advanced ZTA Maturity Level for Network: In the advanced maturity level, network architecture includes ingress/egress micro-perimeters and some internal micro-segmentation. Proactive threat discovery is enabled using basic analytics, and all traffic to internal applications and some external traffic is encrypted. Analysis is integrated across multiple sensor types, and manual policy-driven alerts and triggers are used with automated workflows for network and environment changes.
- Optimal ZTA Maturity Level for Network: At the optimal maturity level, fully distributed ingress/egress micro-perimeters and deep internal micro-segmentation based on application workflows are implemented. Machine learning-based threat protection and filtering are integrated, considering context-based signals. All traffic to internal and external locations is encrypted. Analysis is conducted using automated alerts and triggers, and network environment configurations utilize infrastructure-as-code with pervasive automation. Continuous integration and continuous deployment (CI/CD) models are followed.
- Traditional ZTA Maturity Level for Network: In the traditional maturity level, network architecture relies on a large perimeter or macro-segmentation. Threat protection is primarily based on known threats and static traffic filtering, with minimal internal traffic encryption. Networks, devices, and services are manually identified and sanctioned, and unauthorized entities are discovered and remediated manually.
- Application Workload - The Fourth Pillar of ZTA Model
- Traditional ZTA Maturity Level for Application Workload: In the traditional maturity level, access to applications relies on local authorization and static attributes. Legacy policies are in place, and manual enforcement is performed for software development, software asset management, and security tests and evaluations (ST&E). Software dependencies are tracked manually.
- Advanced ZTA Maturity Level for Application Workload: In the advanced maturity level, centralized authentication, authorization, monitoring, and attribute-based access control are used for application access. Cloud and on-premises applications are accessible over the internet, with some applications available through a VPN. Application security testing is integrated into the development and deployment process, including dynamic testing methods.
- Optimal ZTA Maturity Level for Application Workload: At the optimal maturity level, access to applications is authorized dynamically based on real-time risk analytics. Threat protections are integrated into application workflows, and analytics provide protection based on application behavior. All applications are directly accessible over the internet. Application security testing is performed regularly, with continuous and dynamic monitoring of application health and security. Policies are updated dynamically and enforced.
- Traditional ZTA Maturity Level for Application Workload: In the traditional maturity level, access to applications relies on local authorization and static attributes. Legacy policies are in place, and manual enforcement is performed for software development, software asset management, and security tests and evaluations (ST&E). Software dependencies are tracked manually.
- Data - The Fifth Pillar of ZTA Model
- Traditional ZTA Maturity Level for Data: In the traditional maturity level, data categorization and inventorying are manual processes, leading to inconsistent categorization. Data access is governed by static access controls, and data is primarily stored in on-premises data stores, decrypted at rest. Distributed decision-making determines data categorization and access authorizations.
- Advanced ZTA Maturity Level for Data: In the advanced maturity level, data is manually inventoried with some automated tracking. Least privilege controls are used for data access, considering identity, device risk, and other attributes. Data is stored in encrypted form at rest, primarily in cloud or remote environments. Technical and administrative controls are employed for data protection.
- Optimal ZTA Maturity Level for Data: At the optimal maturity level, data is continuously inventoried using robust tagging and tracking mechanisms. Machine learning models are used for data categorization. Data access is dynamic, following just-in-time and just-enough principles based on ongoing risk assessments. All data at rest is encrypted. Access events are logged and analyzed, and external sensors and systems monitor encrypted data. Strict access controls are enforced for high-value data, and regular backups are performed. Data categorization and access authorizations are unified across all data sources.
- Traditional ZTA Maturity Level for Data: In the traditional maturity level, data categorization and inventorying are manual processes, leading to inconsistent categorization. Data access is governed by static access controls, and data is primarily stored in on-premises data stores, decrypted at rest. Distributed decision-making determines data categorization and access authorizations.
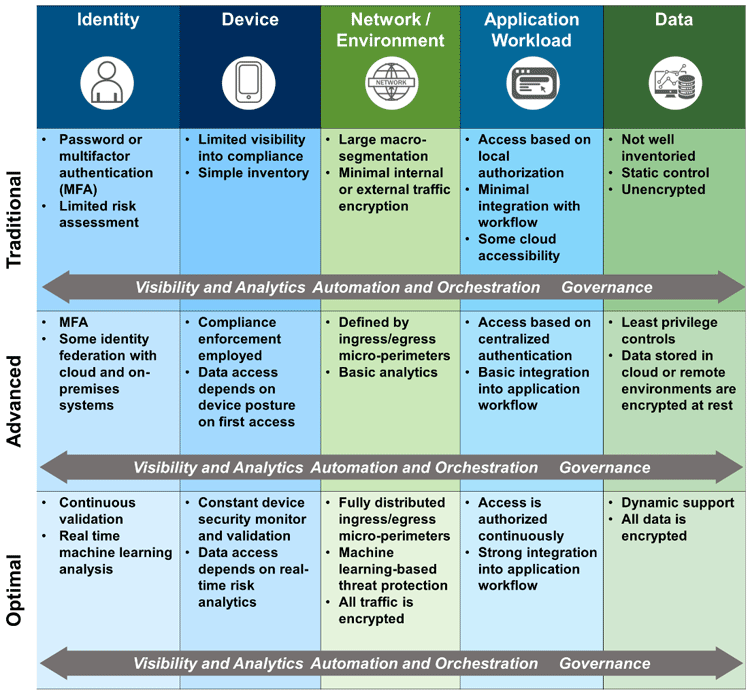
By implementing these Five Pillars of Zero Trust, organizations can establish a robust Zero Trust architecture that enhances security and reduces reliance on traditional perimeter-based defenses. It's important to note that organizations may progress through different maturity levels for each pillar based on their specific goals, requirements, and available resources.
Implementation Guidelines
- Assess and define trust boundaries: Begin by identifying the critical assets and sensitive data within the organization. Determine the trust boundaries around these assets, establishing what needs the highest level of protection.
- Tool suggestion:
- IriusRisk
- Microsoft Threat Modeling Tool
- OWASP Threat Dragon
- ThreatModeler
- IriusRisk
- Tool suggestion:
- Inventory and classify assets: Create an inventory of all assets, including servers, workstations, databases, and applications. Classify them based on their sensitivity and importance to the business. This inventory will help prioritize organization's security efforts.
- Tool suggestion:
- Qualys Asset Inventory
- Rapid7 InsightVM
- Tenable.io
- ServiceNow Asset Management
- Axonius
- SolarWinds IPAM
- Device42
- Ivanti Asset Manager
- BMC Discovery
- Snow Inventory
- Qualys Asset Inventory
- Tool suggestion:
- Implement strong access controls: Apply the principle of least privilege (PoLP) to ensure that users and systems have only the necessary permissions to perform their tasks. Implement multi-factor authentication (MFA) for all users, both internally and externally. Enforce strong password policies and regularly review and revoke unnecessary privileges.
- Tool suggestion:
- Okta
- Microsoft Azure Active Directory
- Ping Identity
- ForgeRock Identity Platform
- SailPoint IdentityIQ
- CyberArk Privileged Access Security
- BeyondTrust Privileged Access Management
- Centrify Privileged Access Service
- OneLogin
- RSA SecurID Access
- Okta
- Tool suggestion:
- Network segmentation: Implement network segmentation to divide network into smaller, isolated segments or zones. Each segment should have its own security controls and access policies based on the principle of least privilege. This prevents lateral movement by attackers and limits the impact of a potential breach.
- Tool suggestion:
- VMware NSX
- Cisco ACI
- Juniper Contrail
- Guardicore Centra
- Illumio
- Check Point Software-defined Protection
- F5 Networks Silverline
- Fortinet FortiGate
- Palo Alto Networks Prisma Access
- Citrix ADC
- VMware NSX
- Tool suggestion:
- Implement strong identity and access management (IAM): Utilize centralized IAM solutions to manage user identities, access rights, and authentication mechanisms. Implement technologies like identity providers, directory services, and privilege management systems to enforce consistent and granular access controls across the organization.
- Tool suggestion:
- Okta Identity Cloud
- Microsoft Azure Active Directory
- Ping Identity
- One Identity Manager
- SailPoint IdentityIQ
- ForgeRock Identity Platform
- IBM Security Identity Governance and Intelligence
- RSA Identity Governance and Lifecycle
- CyberArk Identity Security
- Oracle Identity and Access Management
- Okta Identity Cloud
- Tool suggestion:
- Continuous monitoring and logging: Deploy security monitoring tools that provide real-time visibility into network traffic, user activity, and system logs. Implement Security Information and Event Management (SIEM) solutions to collect, correlate, and analyze security events across the organization's environment. Monitor for anomalous behavior, indicators of compromise (IoCs), and policy violations.
- Tool suggestion:
- Splunk Enterprise Security
- IBM QRadar
- Elastic Security
- LogRhythm
- Rapid7 InsightIDR
- SolarWinds Security Event Manager
- ArcSight
- McAfee Enterprise Security Manager
- Graylog
- Sumo Logic
- Splunk Enterprise Security
- Tool suggestion:
- Implement micro-segmentation and application-level controls: Use technologies like software-defined networking (SDN) and virtual firewalls to create micro-segments within organization's network. Apply access controls and policies at the application level, focusing on individual workloads or services. This approach provides granular control and limits the lateral movement of threats.
- Tool suggestion:
- Guardicore Centra
- VMware NSX
- Illumio
- Check Point Harmony Segmentation
- Cisco Tetration
- Fortinet FortiGate
- Palo Alto Networks Prisma Cloud
- Cloudvisory
- vArmour DSS Distributed Security System
- AlgoSec
- Guardicore Centra
- Tool suggestion:
- Implement strong encryption and data protection: Encrypt data both in transit and at rest using industry-standard encryption algorithms. Utilize strong encryption protocols (such as TLS) for network communications, and implement encryption mechanisms for data stored in databases, file systems, and backups. Implement data loss prevention (DLP) solutions to prevent sensitive data exfiltration.
- Tool suggestion:
- Thales Data Protection Suite
- Symantec Data Loss Prevention (DLP)
- Vormetric Data Security Manager
- Microsoft BitLocker
- McAfee Total Protection
- IBM Guardium Data Protection
- Trend Micro Data Loss Prevention
- Protegrity Data Protection Platform
- Forcepoint Data Loss Prevention
- PKWARE Data Security Platform
- Thales Data Protection Suite
- Tool suggestion:
- Continuous vulnerability management: Regularly scan organization's systems and applications for vulnerabilities using automated tools. Prioritize vulnerabilities based on their severity and promptly patch or remediate them. Implement a robust patch management process and monitor for new vulnerabilities and security updates.
- Tool suggestion:
- Tenable.io
- Qualys Vulnerability Management
- Rapid7 InsightVM
- Nexpose
- Rapid7 Metasploit
- BeyondTrust Retina
- OpenVAS
- Nessus Professional
- Tripwire IP360
- McAfee Vulnerability Manager
- Tenable.io
- Tool suggestion:
- User and system behavioral analytics: Utilize behavioral analytics tools to establish baseline user and system behavior. Identify deviations from normal behavior patterns that may indicate a security incident. Implement anomaly detection, user behavior analytics (UBA), and endpoint detection and response (EDR) solutions to detect and respond to threats effectively.
- Tool suggestion:
- Splunk User Behavior Analytics
- Exabeam Security Management Platform
- Microsoft Azure Sentinel
- Rapid7 InsightIDR
- Securonix Security Analytics
- LogRhythm NextGen SIEM
- Varonis Data Security Platform
- Darktrace Enterprise Immune System
- Vectra AI Network Detection and Response
- Cynet 360 Autonomous Breach Protection
- Splunk User Behavior Analytics
- Tool suggestion:
- Secure remote access: Implement secure remote access solutions, such as virtual private networks (VPNs) or zero trust network access (ZTNA) technologies. Ensure that remote access is only granted based on the principle of least privilege, with strong authentication and encryption mechanisms in place.
- Tool suggestion:
- Palo Alto Networks GlobalProtect
- Cisco AnyConnect Secure Mobility Client
- Zscaler Private Access
- Citrix Gateway
- Pulse Secure
- Check Point Remote Access VPN
- Fortinet FortiClient
- VMware Workspace ONE
- OpenVPN
- Microsoft Always On VPN
- Palo Alto Networks GlobalProtect
- Tool suggestion:
- Incident response and recovery: Develop an incident response plan that outlines the steps to be taken in the event of a security incident. Establish communication channels, roles, and responsibilities for incident response team members. Regularly test and update the plan to address emerging threats. Implement backup and disaster recovery mechanisms to ensure business continuity.
- Tool suggestion:
- IBM Resilient
- Splunk Phantom
- CrowdStrike Falcon Incident Response
- FireEye Mandiant Incident Response
- Carbon Black CB Response
- McAfee MVISION Endpoint Detection and Response (EDR)
- Rapid7 InsightIDR
- Secureworks Incident Response Services
- Cisco Incident Response Services
- Symantec Incident Response Services
- IBM Resilient
- Tool suggestion:
- Employee training and awareness: Conduct regular security awareness training programs for employees to educate them about zero trust principles, potential threats, and best practices. Foster a security-conscious culture within the organization, emphasizing the importance of security in day-to-day operations.
- Tool suggestion:
- KnowBe4 Security Awareness Training
- Proofpoint Security Awareness Training
- PhishMe Simulator (now known as Cofense)
- Infosec IQ
- SANS Security Awareness
- Inspired eLearning Security Awareness Training
- MediaPro Security Awareness Training
- Sophos Phish Threat
- Mimecast Awareness Training
- Webroot Security Awareness Training
- KnowBe4 Security Awareness Training
- Tool suggestion:
- Third-party risk management: Assess the security posture of third-party vendors and partners that have access to organization's systems or handle sensitive data. Implement vendor risk management processes to ensure that they adhere to the same zero trust principles and security standards.
- Tool suggestion:
- SecurityScorecard
- BitSight Security Ratings
- RiskRecon (now part of Mastercard)
- CyberGRX
- Prevalent Third-Party Risk Management
- RSA Archer Third-Party Risk Management
- ProcessUnity Third-Party Risk Management
- OneTrust Vendorpedia
- UpGuard Vendor Risk Management
- MetricStream Third-Party Risk Management
- SecurityScorecard
- Tool suggestion:
- Regular assessments and audits: Perform periodic security assessments and audits to evaluate the effectiveness of Zero Trust Architecture. Engage independent security professionals to conduct penetration tests and vulnerability assessments to identify any weaknesses or gaps in organization's defenses.
- Tool suggestion:
- Rapid7 InsightVM
- Tenable.io
- Qualys Vulnerability Management
- Nexpose
- OpenVAS
- Nessus Professional
- IBM Security QRadar Vulnerability Manager
- McAfee Vulnerability Manager
- F-Secure Radar
- Acunetix Vulnerability Scanner
- Rapid7 InsightVM
- Tool suggestion:
Remember, Zero Trust Architecture is an ongoing process that requires continuous monitoring, adaptation, and improvement. Regularly review and update the implementation based on new technologies, emerging threats, and lessons learned from security incidents.
"Please note that the suggested tools represent a mix of industry-leading solutions and widely recognized as leaders in their respective domains and provide comprehensive features and functionalities to support a robust Zero Trust Architecture. However, it's important to note that the "best" tool for an organization may vary depending on specific requirements, infrastructure, budget, and compatibility with organization's existing infrastructure. It's recommended to thoroughly evaluate and test these tools in the organization's environment to determine the best fit to achieve security objectives and goals."
References:
https://csrc.nist.gov/publications/detail/sp/800-207/final
https://www.microsoft.com/en-us/security/business/zero-trust
https://www.whitehouse.gov/wp-content/uploads/2022/01/M-22-09.pdf
https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-207.pdf
https://www.cisa.gov/sites/default/files/2023-04/zero_trust_maturity_model_v2_508.pdf
https://services.google.com/fh/files/misc/ncsc_zero_trust_principles_on_google_cloud_v1.pdf
https://www.cisa.gov/sites/default/files/publications/Cloud%20Security%20Technical%20Reference%20Architecture.pdf
https://www.cisa.gov/sites/default/files/2023-01/Zero_Trust_Principles_Enterprise_Mobility_For_Public_Comment_508C.pdf