Software Composition Analysis (SCA) is a security practice that focuses on identifying and managing the open-source and third-party components used within software applications. It involves analyzing the composition of software to detect and manage potential security vulnerabilities, license compliance issues, and other risks associated with these components.
What is SCA security?
Software Composition Analysis (SCA) security is a practice that focuses on managing the security risks associated with using open-source and third-party components in software applications. It is crucial to have visibility into how these components are programmed and used to prevent security vulnerabilities, compliance issues, and code quality impacts.
SCA tools automate this process and provide insights to identify and mitigate issues. However, it's essential to proactively seek visibility into the third-party components used in the code. Without this visibility, it would be challenging to address the issues that SCA tools are designed to mitigate.
It's worth noting that SCA tools serve a different purpose than Static Application Security Testing (SAST) tools. SAST tools scan application's codebase for potential vulnerabilities based on predefined rules, such as buffer overflows, cross-site scripting (XSS), and SQL injections. On the other hand, SCA focuses on identifying the open-source codebase, enabling developers to manage their exposure to vulnerabilities and ensure license compliance.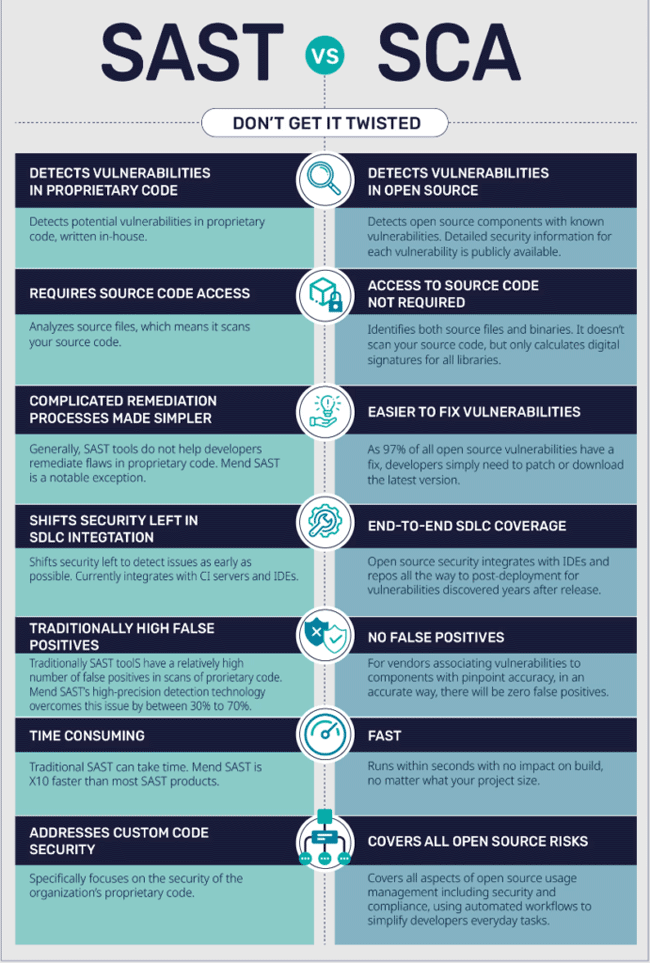
By incorporating SCA security practices and utilizing specialized SCA tools, organizations can proactively manage the security risks associated with open-source and third-party software components, mitigating security vulnerabilities, ensure license compliance, and maintain a strong security posture within software applications.
Types of SCA Software and Their Benefits
To effectively manage and analyze third-party and open-source components, several types of Software Composition Analysis (SCA) tools are available. Here are five prominent types and their respective benefits:
- Package Managers: These tools assist in the installation and management of open-source packages, offering information on dependencies to avoid version conflicts. They streamline the process of incorporating and maintaining third-party components in projects.
- Binary Analysis Tools: Used for scanning compiled code, these tools identify the open-source components utilized in the codebase. They provide insights into dependencies, security risks, and licensing issues associated with those components, aiding in vulnerability mitigation and compliance management.
- Vulnerability Scanners: These tools specifically focus on scanning open-source packages and libraries for known vulnerabilities. By identifying vulnerabilities, they enable prioritization, allowing an organization to address high-risk vulnerabilities first, thus bolstering the security of applications.
- Composition Analysis Tools: These tools offer a comprehensive view of open-source components by analyzing dependencies, license issues, and the overall quality and health of the software. They provide valuable insights to manage the composition of software, ensuring a robust and reliable codebase.
- Continuous Monitoring Tools: Designed to monitor applications over time, these tools keep track of changes or updates to open-source components. They alert developers to any relevant updates, ensuring that applications remain up-to-date with the latest patches and security fixes, thereby reducing the risk of vulnerabilities.
The main objectives of Software Composition Analysis
- Component Identification: SCA tools examine software applications to identify and create an inventory of all the open-source and third-party components used. This includes libraries, frameworks, modules, and other dependencies.
- Vulnerability Detection: SCA tools compare the identified components against a database of known vulnerabilities. By analyzing version numbers and other metadata, they identify any security vulnerabilities or weaknesses present in the components.
- License Compliance: SCA tools assess the licenses associated with the components used within the software. They determine whether the licenses are compatible, identify any license violations, and provide insights into the legal obligations and restrictions associated with each component.
- Risk Management: SCA helps organizations assess the overall risk profile of their software applications based on the identified vulnerabilities and license issues. It enables prioritization of remediation efforts based on the severity of vulnerabilities and the potential impact on the application's security.
- Remediation Guidance: SCA tools provide recommendations and guidance on mitigating the identified vulnerabilities and license compliance issues. This includes information on available patches, updates, or alternative component options to resolve the identified risks.
- Continuous Monitoring: SCA is an ongoing process that includes regular scanning and monitoring of software applications throughout the software development lifecycle. It helps ensure that new vulnerabilities or license issues are promptly identified and addressed as part of the software maintenance and update process.
Software Composition Analysis is essential for organizations to understand and manage the security and compliance risks associated with using open-source and third-party components within their software applications. By implementing SCA practices and utilizing specialized tools, organizations can enhance the security of their software, reduce the risk of vulnerabilities, and ensure compliance with licensing requirements.
Key features to look for in an SCA tool
When selecting a Software Composition Analysis (SCA) tool, several key features can enhance the speed, reliability, and security of software development process:
- Accelerated Development Speed: SCA tools eliminate the need for manual tracking and management of open-source components. By automating these processes, developers can allocate more time to writing code, testing, and delivering software, resulting in faster development cycles and increased productivity.
- Enhanced Application Reliability: SCA tools enable the use of secure and reliable open-source components. By proactively identifying potential security vulnerabilities and licensing issues, these tools help mitigate risks and ensure that applications are built on a solid foundation. This fosters greater confidence in the reliability and stability of the software being developed.
- Strengthened Application Security: SCA tools play a crucial role in bolstering application security. By detecting and addressing security vulnerabilities and dependencies on outdated components, these tools help protect applications from potential attacks. They contribute to a proactive security approach, reducing the likelihood of security breaches and enhancing overall application resilience.
Here are some of the key features to consider when choosing an SCA tool:
- Containerized Environment Support: Look for an SCA tool that can scan open-source components within containerized environments. As organizations increasingly adopt containerization, the tool should identify vulnerabilities in components running inside containers, ensuring the security and reliability of containerized environment.
- Native Support for Container Registries: Ensure that the SCA tool natively supports the specific container registry organization's team uses. This enables seamless scanning of container images for potential vulnerabilities or issues without manual configuration, saving time and reducing errors.
- Comprehensive Library Coverage: A good SCA tool should offer broad coverage, detecting vulnerabilities, licensing issues, and quality concerns across a wide range of open-source libraries and components commonly used in software development.
- Real-Time Monitoring: Real-time monitoring capabilities are crucial for dynamic organizations. The SCA tool should detect potential vulnerabilities or issues as soon as they arise, allowing prompt mitigation and preventing them from evolving into major problems.
- Easy Integration: Choose an SCA tool that seamlessly integrates into existing development workflow and infrastructure. It should not disrupt or delay the Software Development Life Cycle (SDLC) and should work well with organization's tools and processes.
- Customizable Policies: The ability to customize policies based on organization's specific needs is important. The SCA tool should allow an organization to define security and quality standards tailored to organization's requirements, ensuring compliance with the organization's unique policies.
- Reporting and Analytics: Look for an SCA tool that provides detailed reports and analytics. This helps track progress, monitor trends, and identify areas for improvement. Clear and insightful reporting enhances decision-making and facilitates communication within the organization.
- Automation: The SCA tool should offer automation capabilities, including automated scanning and analysis. This saves time, improves efficiency, and reduces the risk of human error associated with manual processes.
By considering these key features when selecting an SCA tool, an organization can enhance the speed the development process, ensure the reliability of the organization's applications, and strengthen the security posture of software through effective management of open-source components and dependencies.
Software Composition Analysis Tools
- Mend (formerly WhiteSource) is a software composition analysis (SCA) and open source security platform that helps organizations manage and secure their open-source components and dependencies. It provides automated tools and solutions to track, identify, and remediate security vulnerabilities and license compliance issues in open-source software. WhiteSource is an SCA and open-source security platform that helps organizations manage and secure their open-source components. With its dependency detection, vulnerability management, license compliance, risk prioritization, continuous monitoring, remediation guidance, integration capabilities, and reporting features, WhiteSource assists organizations in ensuring the security and compliance of their software applications. Key features and capabilities of WhiteSource include:
- Dependency Detection: WhiteSource scans software projects to identify open-source components and dependencies used within the codebase. It provides an accurate inventory of open-source libraries, frameworks, and modules.
- Vulnerability Management: The platform compares the identified components against a comprehensive vulnerability database, providing organizations with information about known security vulnerabilities and their severity levels. It assists in prioritizing and addressing vulnerabilities based on risk.
- License Compliance: WhiteSource assesses the licenses associated with the open-source components in use and ensures compliance with licensing obligations. It identifies any license violations and provides insights into the restrictions and obligations associated with each component's license.
- Risk Prioritization: WhiteSource offers risk prioritization capabilities by assigning severity scores to vulnerabilities based on their potential impact. It helps organizations focus on high-risk vulnerabilities that pose the most significant security threats.
- Continuous Monitoring: WhiteSource enables ongoing monitoring of open-source components throughout the software development lifecycle. It provides alerts and notifications about newly discovered vulnerabilities, allowing organizations to promptly address emerging security risks.
- Remediation Guidance: The platform provides actionable remediation guidance by offering information on available patches, updates, and fixes for identified vulnerabilities. It assists in managing and resolving security issues effectively.
- Integration and Automation: WhiteSource integrates with various development tools, such as IDEs, build systems, and CI/CD pipelines. It supports automation and provides APIs for seamless integration into existing development workflows.
- Reporting and Analytics: WhiteSource generates comprehensive reports and analytics on open-source usage, vulnerability status, and license compliance. It provides visibility into the overall security posture of software projects.
- Black Duck is a software composition analysis (SCA) tool and open-source security platform that helps organizations manage and secure their open-source software components and dependencies. It provides automated scanning, identification, and analysis of open-source code to detect and address security vulnerabilities, license compliance issues, and other risks associated with open-source usage. Black Duck is an SCA and open-source security platform that helps organizations manage and secure their open-source components. With its dependency detection, vulnerability detection, license compliance, risk management, governance capabilities, continuous monitoring, integration options, and reporting features, Black Duck assists organizations in ensuring the security and compliance of their software applications. Key features and capabilities of Black Duck include:
- Dependency Detection: Black Duck scans software projects to identify open-source components and dependencies used within the codebase. It creates an inventory of open-source libraries, frameworks, and modules.
- Vulnerability Detection: The platform compares the identified components against a comprehensive vulnerability database, including the National Vulnerability Database (NVD), to identify known security vulnerabilities. It provides details on vulnerabilities, severity levels, and remediation guidance.
- License Compliance: Black Duck assesses the licenses associated with the open-source components and ensures compliance with licensing obligations. It identifies license violations and helps organizations understand the licensing requirements and restrictions.
- Security Risk Management: Black Duck helps organizations assess and manage the overall security risk of their software applications based on the identified vulnerabilities. It provides risk scores, prioritizes vulnerabilities, and assists in addressing critical security issues.
- Open Source Governance: Black Duck offers governance capabilities for managing open-source usage within organizations. It provides policy enforcement, approval workflows, and visibility into open-source usage across projects and teams.
- Continuous Monitoring: Black Duck supports continuous monitoring of open-source components throughout the software development lifecycle. It provides alerts and notifications about newly discovered vulnerabilities and helps organizations stay up-to-date with emerging security risks.
- Integration and Automation: Black Duck integrates with development tools, build systems, and CI/CD pipelines to seamlessly integrate security practices into the software development process. It provides APIs and automation capabilities for efficient integration.
- Reporting and Analytics: Black Duck generates reports and analytics on open-source usage, vulnerability status, and license compliance. It provides visibility into the security posture of software projects and facilitates compliance reporting.
- Checkmarx SCA is a software composition analysis (SCA) tool and a solution offered by Checkmarx, a provider of software security solutions. Checkmarx SCA focuses on identifying and managing open-source and third-party components used within software applications to help organizations address security vulnerabilities and ensure license compliance. Checkmarx SCA is a software composition analysis solution offered by Checkmarx. With its component identification, vulnerability detection, license compliance, risk prioritization, continuous monitoring, remediation guidance, integration capabilities, and reporting features, Checkmarx SCA helps organizations manage and secure their open-source and third-party components, reduce security vulnerabilities, and ensure compliance with licensing requirements. Key features and capabilities of Checkmarx SCA include:
- Component Identification: Checkmarx SCA scans software projects to identify open-source and third-party components used within the codebase. It creates an inventory of these components, including libraries, frameworks, and modules.
- Vulnerability Detection: The solution compares the identified components against a comprehensive vulnerability database to detect known security vulnerabilities. It provides details on the vulnerabilities, including severity levels, descriptions, and remediation recommendations.
- License Compliance: Checkmarx SCA assesses the licenses associated with the identified components and ensures compliance with licensing requirements. It helps organizations understand the licensing obligations and restrictions of the components they use.
- Risk Prioritization: The solution offers risk prioritization capabilities, allowing organizations to prioritize remediation efforts based on the severity of identified vulnerabilities and their potential impact on the software application's security.
- Continuous Monitoring: Checkmarx SCA supports continuous monitoring of open-source components throughout the software development lifecycle. It provides alerts and notifications about newly discovered vulnerabilities to help organizations stay informed and take timely actions.
- Remediation Guidance: The solution provides actionable remediation guidance by offering information on available patches, updates, or alternative component options to address identified vulnerabilities. It assists organizations in effectively remediating security issues.
- Integration and Automation: Checkmarx SCA integrates with development tools, build systems, and CI/CD pipelines to seamlessly incorporate security practices into the software development process. It supports automation and provides APIs for easy integration into existing workflows.
- Reporting and Analytics: Checkmarx SCA generates comprehensive reports and analytics on open-source usage, vulnerability status, and license compliance. It provides visibility into the security posture of software projects and assists in compliance reporting.
- Timesys Vigiles is a vulnerability management and monitoring solution designed for embedded and IoT (Internet of Things) devices. It helps organizations identify and address security vulnerabilities in their embedded systems by providing continuous monitoring, vulnerability detection, and remediation guidance. Timesys Vigiles is a vulnerability management and monitoring solution designed for embedded and IoT devices. With its continuous monitoring, vulnerability detection, risk assessment, remediation guidance, compliance support, integration capabilities, and software supply chain security features, Vigiles assists organizations in proactively managing and securing their embedded systems, reducing the risk of security vulnerabilities and maintaining a strong security posture for their devices. Key features and capabilities of Timesys Vigiles include:
- Continuous Monitoring: Vigiles offers ongoing monitoring of embedded systems, tracking security vulnerabilities and providing timely alerts when new vulnerabilities are discovered. It ensures that organizations stay informed about potential risks to their devices.
- Vulnerability Detection: The solution scans embedded systems to detect security vulnerabilities in the software components, libraries, and firmware used within the devices. It leverages a comprehensive vulnerability database to identify known vulnerabilities.
- Risk Assessment and Prioritization: Vigiles provides risk assessment and prioritization of vulnerabilities based on severity levels and potential impact. It helps organizations prioritize remediation efforts based on the criticality of the vulnerabilities.
- Customizable Policies and Compliance: The solution allows organizations to define custom policies and compliance requirements for their embedded systems. It supports adherence to industry standards and regulatory frameworks, enabling organizations to meet security and compliance guidelines.
- Remediation Guidance: Vigiles offers detailed remediation guidance, providing recommendations for fixing identified vulnerabilities. It assists organizations in understanding the steps required to mitigate security risks and provides access to patches or updates when available.
- Vulnerability Tracking and Reporting: Vigiles tracks the status of vulnerabilities and provides comprehensive reporting capabilities. It generates reports on vulnerability assessments, risk profiles, and remediation progress, enabling organizations to maintain visibility and demonstrate compliance.
- Integration and Automation: Vigiles can be integrated into the software development lifecycle and build processes of embedded systems. It supports automation and offers APIs for seamless integration with existing development and security workflows.
- Secure Software Supply Chain: Vigiles helps organizations ensure the security of their software supply chain for embedded systems. It assists in assessing the security posture of third-party components and libraries used in the development of devices.
Reference:
https://www.gartner.com/reviews/market/software-composition-analysis-sca