Automated security testing in a CI/CD (Continuous Integration/Continuous Deployment) pipeline, embraced by the DevSecOps approach, integrates various security testing practices into the software development process. It combines several automated security testing techniques to identify and address potential vulnerabilities and weaknesses in the application code before it is deployed to production.
Security plays a critical role in the CI/CD pipeline, which automates the build, test, and deployment of code. This process ensures that code changes are quickly and reliably delivered to production environments. To maintain robust security throughout the pipeline, it is essential to incorporate automated security testing. This involves integrating security scanning tools into the CI/CD pipeline to run automated security scans against the code.
By automating security testing in the CI/CD pipeline, organizations can proactively identify and address security vulnerabilities at an early stage of the software development process. Integrating various security tools allows for comprehensive scanning, including static code analysis, vulnerability scanning, and security policy enforcement. These tools provide automated and continuous security checks, ensuring that code changes meet security requirements before being deployed into production.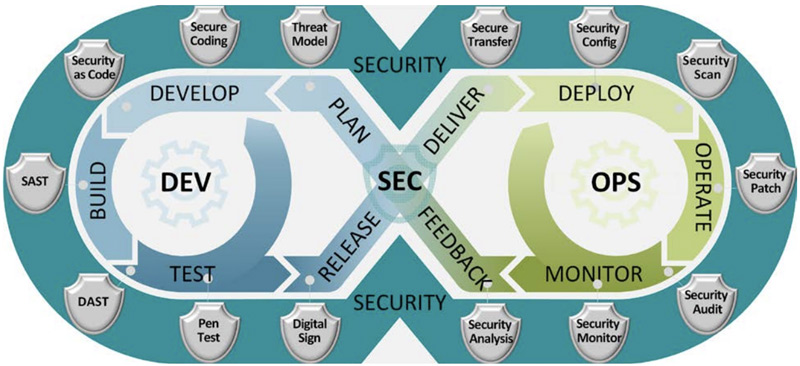
Automated security testing in the CI/CD pipeline enables organizations to enforce security best practices, reduce manual effort, and maintain a consistent security posture across all stages of software delivery. It helps prevent security vulnerabilities from being introduced and allows for timely remediation of any identified issues. By integrating security tools into the CI/CD pipeline, companies can achieve a balance between rapid software delivery and robust security measures, enhancing the overall security and reliability of their applications.
Automating Manual Testing in CI/CD Pipeline
Automating manual testing in the CI/CD pipeline is crucial to streamline the testing process, improve efficiency, and ensure consistent and reliable software releases. Here are steps to automate manual testing effectively:
- Set up a Test Environment: Create a test environment that closely mirrors the production environment. This ensures that the tests are conducted in an environment that accurately represents the target deployment, allowing for accurate results.
- Identify Areas for Testing: Perform risk analysis to identify critical areas in the code that require testing. This analysis helps prioritize tests based on potential risks and ensures that important test cases are not overlooked. It involves identifying code violations, stability issues, and performance concerns.
- Prepare Test Cases and Data: Define and prepare test cases that cover the identified areas for testing. Test cases should be designed to validate functionality, performance, security, and other relevant aspects of the software. Additionally, set up test data that is representative of real-world scenarios to ensure comprehensive testing.
- Integrate Testing Tools: Integrate a suitable testing tool into CI/CD pipeline. This can be done by incorporating the testing tool in the build and test stage of the pipeline. Choose a modern tool that offers integration capabilities and supports custom test capabilities. Platforms like Harness provide organizations with the ability to counter security threats and vulnerabilities effectively.
By automating manual testing in the CI/CD pipeline, organizations can reduce manual effort, ensure consistency in testing, and speed up the release process. It enables frequent and reliable software deployments while maintaining the desired level of quality and mitigating risks. Automation also frees up resources to focus on more complex testing tasks, leading to improved productivity and faster time-to-market for software products.
Key components of automated security testing in the CI/CD pipeline with DevSecOps
- Static Code Analysis: Static code analysis tools like Coverity, CodeQL, Veracode, and Fortify are used in the CI stage to scan the source code and detect coding flaws, security vulnerabilities, and compliance violations. This helps identify issues such as buffer overflows, SQL injection, and insecure coding practices.
- Dynamic Application Security Testing: In the automated build and packaging stage, dynamic application security testing tools like WebInspect, AppSpider, and AppScan are employed to simulate real-world attacks on a running instance of the application. This allows for the identification of vulnerabilities that may only manifest at runtime, such as cross-site scripting (XSS) or insecure API usage.
- Interactive Security Testing: Interactive security testing tools like Seeker can be integrated into the CI/CD pipeline to provide interactive and context-aware security testing during the development and deployment stages. Seeker analyzes the application's runtime behavior, detects vulnerabilities, and provides feedback to developers in real-time.
- Software Composition Analysis: Software composition analysis tools like Mend (formerly WhiteSource), Black Duck, Checkmarx SCA, and Timesys Vigiles are utilized to scan third-party libraries and components used in the application. This helps identify known vulnerabilities and open-source license compliance issues, allowing developers to mitigate potential risks through timely updates or alternative library choices.
- Code Quality Analysis: Code quality analysis tools like SonarQube analyze code for adherence to coding standards, best practices, and maintainability. While not solely focused on security, they contribute to overall code quality and can identify potential code smells or anti-patterns that may introduce vulnerabilities.
- Container Security Analysis: In the context of containerized applications, container security analysis tools like Anchore, Aqua Security, Palo Alto Prisma Cloud, Qualys Container Security, Snyk, StackRox, and Sysdig enable scanning and analysis of container images for vulnerabilities and misconfigurations. This ensures that containers are secure and comply with security best practices before deployment.
- Penetration Testing: Penetration testing tools like Burp Suite, Metasploit, and Sec-SecBurpPT can be incorporated into the pipeline to complement the automated security testing efforts. They allow for comprehensive testing of application security by simulating real-world attacks and identifying vulnerabilities that may have been missed by other automated tools.
By incorporating these automated security testing practices into the CI/CD pipeline with DevSecOps, organizations can proactively address security risks, reduce the likelihood of introducing vulnerabilities, and accelerate the delivery of secure software. This approach promotes collaboration between development, security, and operations teams, enabling continuous improvement in application security throughout the software development lifecycle.
The key benefits of implementing automated security testing in a CI/CD pipeline with a DevSecOps
- Early Vulnerability Detection: By integrating security testing into the CI/CD pipeline, vulnerabilities are identified early in the software development process. This allows for prompt remediation before the vulnerabilities become more complex and costly to fix, reducing the overall risk exposure.
- Continuous Security Feedback: Automated security testing provides continuous feedback to developers regarding potential vulnerabilities and weaknesses in the codebase. This enables them to make immediate adjustments and address security issues without disrupting the development flow.
- Accelerated Time-to-Market: Automated security testing in the CI/CD pipeline helps streamline the security review process and ensures that security checks are performed consistently and efficiently. This allows for faster software delivery and reduces time-to-market, enhancing business agility.
- Improved Code Quality: Automated security testing tools often include code quality checks, ensuring that code adheres to coding standards, best practices, and secure coding guidelines. This results in improved overall code quality and maintainability.
- Enhanced Collaboration: Integrating security testing into the CI/CD pipeline fosters collaboration between development, security, and operations teams. Security becomes everyone's responsibility, and teams work together to address vulnerabilities and implement security measures, promoting a culture of shared ownership and accountability.
- Cost Savings: Early detection and remediation of security vulnerabilities through automated testing help reduce the cost associated with addressing security issues at later stages. It eliminates the need for manual security testing and reduces the potential impact of security breaches or non-compliance.
- Scalability and Consistency: Automated security testing ensures consistent security checks across all code changes and deployments, irrespective of team size or workload. It allows for scalability as the codebase grows, ensuring that security remains a top priority.
- Compliance and Regulatory Alignment: Automated security testing helps organizations meet compliance requirements and align with industry regulations by proactively identifying and addressing security vulnerabilities. It supports the organization's overall risk management and governance efforts.
- Continuous Improvement: Automated security testing provides valuable insights into the security posture of the application over time. The feedback obtained from testing results and metrics can be used to drive continuous improvement in security practices, development processes, and the overall security culture.
By embracing automated security testing in the CI/CD pipeline with a DevSecOps approach, organizations can integrate security seamlessly into their software development lifecycle, reduce the time and effort required for security assessments, and deliver secure software with increased speed, reliability, and confidence.
DevSecOps Security Tools
- Static Code Analysis / Static Application Security Testing (SAST):
- Coverity is a widely used static code analysis tool developed by Synopsys. It is designed to identify and help eliminate software defects, security vulnerabilities, and quality issues in code during the development process. Coverity is widely adopted by software development teams to enhance code quality, improve security, and reduce the risk of software defects and vulnerabilities. It assists in identifying and addressing issues early in the development process, leading to more reliable and secure software applications
- CodeQL is a powerful semantic code analysis engine and query language developed by GitHub. It enables developers and security professionals to analyze codebases for security vulnerabilities and software defects. CodeQL performs static code analysis by examining the structure, data flow, and control flow of code to identify potential issues. CodeQL is widely used in both open-source and enterprise software development to enhance code security and maintain code quality. It helps developers identify and re
- Veracode, is a leading application security testing platform that provides a wide range of security testing solutions to identify and mitigate software vulnerabilities. It offers both static and dynamic analysis capabilities to assess the security of applications throughout the development lifecycle. Veracode is trusted by organizations worldwide to enhance the security of their applications. Its comprehensive security testing capabilities, along with its emphasis on developer-centric practices, enable organizations to deliver secure software while minimizing risk and addressing compliance requirements.
- Fortify is an application security testing (AST) tool developed by Micro Focus. It offers a range of static and dynamic analysis techniques to identify and address security vulnerabilities in software applications. Fortify is widely used by organizations to enhance the security of their applications and mitigate potential risks. Fortify helps organizations identify and address security vulnerabilities early in the development process, enabling the delivery of more secure software. It supports a proactive approach to application security by integrating with the development workflow and providing actionable insights to developers and security teams.
- Dynamic Application Security Testing:
- WebInspect is a web application security testing tool developed by Micro Focus. It is designed to assess the security of web applications by identifying vulnerabilities and potential weaknesses in their code and configuration. WebInspect is used by security professionals, penetration testers, and developers to evaluate the security posture of web applications. It helps identify vulnerabilities and weaknesses that could be exploited by attackers, enabling organizations to proactively address these issues and enhance the overall security of their web applications. WebInspect utilizes a combination of automated scanning and manual testing techniques to comprehensively evaluate web applications for security flaws.
- AppSpider is a web application security testing tool developed by Rapid7. It is designed to assess the security of web applications by identifying vulnerabilities and potential risks within their code and configurations. AppSpider is used by security professionals, penetration testers, and developers to proactively assess and improve the security of web applications. By identifying vulnerabilities and risks, organizations can address these issues and strengthen their web application's security posture. AppSpider employs a combination of automated scanning and manual testing techniques to comprehensively evaluate web applications for security flaws.
- AppScan, also known as IBM Security AppScan, is a web application security testing tool developed by IBM. It is designed to identify and assess vulnerabilities in web applications to help organizations improve their security posture. AppScan is widely used by security professionals, penetration testers, and developers to assess and improve the security of web applications. By identifying vulnerabilities and providing actionable recommendations, AppScan helps organizations enhance their application security and protect against potential attacks. AppScan offers a range of features and capabilities to facilitate comprehensive security testing of web applications
- Interactive Security Testing:
- Seeker is an interactive application security testing (IAST) tool designed to enhance the security of web applications during the development process. It is specifically focused on identifying and helping remediate security vulnerabilities related to authentication and authorization.Seeker operates as a security testing proxy that sits between the user's browser and the application being tested. It analyzes the application's behavior in real-time, monitoring and capturing various user actions and requests. Seeker provides immediate feedback to developers by identifying potential security weaknesses and suggesting remediation steps directly within the development environment. Seeker is a valuable tool for developers and security teams aiming to strengthen the security of their web applications by proactively addressing authentication and authorization vulnerabilities. It enables a more efficient and collaborative approach to secure software development, ultimately reducing the risk of unauthorized access and data breaches.
- Software Composition Analysis:
- Mend (formerly WhiteSource) is a software composition analysis (SCA) and open source security platform that helps organizations manage and secure their open-source components and dependencies. It provides automated tools and solutions to track, identify, and remediate security vulnerabilities and license compliance issues in open-source software. WhiteSource is an SCA and open-source security platform that helps organizations manage and secure their open-source components. With its dependency detection, vulnerability management, license compliance, risk prioritization, continuous monitoring, remediation guidance, integration capabilities, and reporting features, WhiteSource assists organizations in ensuring the security and compliance of their software applications
- Black Duck is a software composition analysis (SCA) tool and open-source security platform that helps organizations manage and secure their open-source software components and dependencies. It provides automated scanning, identification, and analysis of open-source code to detect and address security vulnerabilities, license compliance issues, and other risks associated with open-source usage. Black Duck is an SCA and open-source security platform that helps organizations manage and secure their open-source components. With its dependency detection, vulnerability detection, license compliance, risk management, governance capabilities, continuous monitoring, integration options, and reporting features, Black Duck assists organizations in ensuring the security and compliance of their software applications.
- Checkmarx SCA is a software composition analysis (SCA) tool and a solution offered by Checkmarx, a provider of software security solutions. Checkmarx SCA focuses on identifying and managing open-source and third-party components used within software applications to help organizations address security vulnerabilities and ensure license compliance. Checkmarx SCA is a software composition analysis solution offered by Checkmarx. With its component identification, vulnerability detection, license compliance, risk prioritization, continuous monitoring, remediation guidance, integration capabilities, and reporting features, Checkmarx SCA helps organizations manage and secure their open-source and third-party components, reduce security vulnerabilities, and ensure compliance with licensing requirements.
- Timesys Vigiles is a vulnerability management and monitoring solution designed for embedded and IoT (Internet of Things) devices. It helps organizations identify and address security vulnerabilities in their embedded systems by providing continuous monitoring, vulnerability detection, and remediation guidance. Timesys Vigiles is a vulnerability management and monitoring solution designed for embedded and IoT devices. With its continuous monitoring, vulnerability detection, risk assessment, remediation guidance, compliance support, integration capabilities, and software supply chain security features, Vigiles assists organizations in proactively managing and securing their embedded systems, reducing the risk of security vulnerabilities and maintaining a strong security posture for their devices.
- Code Quality Analysis:
- SonarQube is an open-source platform used for continuous code quality management. It provides automated code review and analysis tools to assess and monitor the quality of software codebases. SonarQube empowers development teams to proactively manage code quality, improve maintainability, and reduce technical debt. It supports the adoption of coding best practices and provides actionable insights to enhance software quality and security throughout the development lifecycle.
- SonarQube is an open-source platform used for continuous code quality management. It provides automated code review and analysis tools to assess and monitor the quality of software codebases. SonarQube empowers development teams to proactively manage code quality, improve maintainability, and reduce technical debt. It supports the adoption of coding best practices and provides actionable insights to enhance software quality and security throughout the development lifecycle.
- Container Security Analysis:
- Anchore is an open-source container image analysis and security tool that focuses on providing visibility and control over container images. It helps organizations ensure the security and compliance of their container images throughout the software development lifecycle. Anchore offers both an open-source version, known as Anchore Engine, and a commercial product called Anchore Enterprise that includes additional features and enterprise-grade support. By using Anchore, organizations can proactively identify and address security vulnerabilities, enforce image security and compliance policies, and ensure that container images deployed in their environments are secure and trustworthy.
- Aqua Security is a leading container security platform that provides comprehensive security solutions for containerized environments. It offers a range of tools and services designed to help organizations protect their containerized applications and infrastructure from potential security risks and threats. Aqua Security supports various container orchestration platforms, including Kubernetes, Docker, and Amazon ECS, and integrates with DevOps toolchains to enable seamless security integration into the CI/CD pipeline. Overall, Aqua Security helps organizations establish a strong security foundation for their containerized environments, ensuring that containerized applications and infrastructure are protected against potential threats, vulnerabilities, and compliance risks.
- JFrog Xray is a software vulnerability and license compliance scanning tool offered by JFrog, a leading provider of DevOps and software development tools. Xray is designed to provide comprehensive visibility and analysis of software artifacts, including dependencies, components, and containers, throughout the entire software development lifecycle. JFrog Xray is a software vulnerability and license compliance scanning tool that helps organizations identify and address security vulnerabilities and license risks in their software artifacts. With its vulnerability scanning, license compliance analysis, impact analysis, continuous monitoring, integration capabilities, custom policies, and reporting features, Xray assists organizations in maintaining the security, compliance, and quality of their software throughout the entire software development lifecycle.
- Palo Alto Prisma Cloud is a comprehensive cloud security platform that provides organizations with visibility, compliance, and protection across their cloud infrastructure and applications. It is designed to address the security challenges associated with cloud environments, including public, private, and hybrid clouds. Palo Alto Networks Prisma Cloud is a comprehensive cloud security platform that provides organizations with visibility, compliance, and protection across their cloud infrastructure and applications. With its CSPM, CWP, CNS, CSPM for SaaS, CNAS, IAM security, compliance, and integration capabilities, Prisma Cloud helps organizations secure their cloud environments and mitigate risks associated with cloud adoption.
- Qualys Container Security is a cloud-based security solution designed to provide comprehensive visibility and protection for containerized environments. It helps organizations assess, monitor, and secure their container deployments by identifying vulnerabilities, ensuring compliance, and implementing security best practices. Qualys Container Security is a cloud-based security solution that enables organizations to assess, monitor, and secure their containerized environments. With its vulnerability management, image assurance, runtime monitoring, compliance assessments, configuration assessment, integration capabilities, risk scoring, and continuous monitoring, Qualys Container Security helps organizations proactively identify and address security vulnerabilities, ensure compliance, and maintain a strong security posture within their container deployments.
- Snyk is a developer-first security platform that focuses on identifying and addressing vulnerabilities and security risks in open source libraries, containers, and infrastructure as code (IaC). It helps organizations improve the security of their applications and code dependencies throughout the software development lifecycle. Snyk supports multiple programming languages, package managers, and cloud platforms, making it suitable for a wide range of application environments. It aims to empower developers to take ownership of security and integrate security practices seamlessly into their development workflows. Overall, Snyk enables organizations to proactively manage their application and infrastructure security, reduce risk from vulnerable dependencies, and build secure and reliable software
- StackRox is a container and Kubernetes security platform designed to protect cloud-native applications and infrastructure. It provides comprehensive security capabilities to identify, assess, and mitigate risks within containerized environments. StackRox helps organizations secure their container deployments throughout the entire software development lifecycle, from build to runtime. StackRox is a container and Kubernetes security platform that helps organizations protect their cloud-native applications and infrastructure. With its container image scanning, configuration management, runtime threat detection, compliance capabilities, network segmentation, and integration options, StackRox assists in securing containerized environments and addressing potential security risks throughout the software development lifecycle.
- Sysdig is a monitoring and security platform designed for cloud-native environments. It provides deep visibility into containerized applications, microservices, and infrastructure in order to improve performance, troubleshoot issues, and enhance security. Sysdig is a powerful platform that combines monitoring and security features to help organizations monitor, troubleshoot, and secure their cloud-native applications and infrastructure. With its real-time visibility, container monitoring, security capabilities, and integration options, Sysdig enables users to optimize performance, detect and prevent issues, and ensure the reliability and security of their applications.
- Penetration Testing:
- Burp Suite is a popular and widely used integrated platform for web application security testing. Developed by PortSwigger, Burp Suite provides a comprehensive set of tools that assist security professionals in performing various security assessments, such as penetration testing, vulnerability scanning, and web application security analysis. Burp Suite is highly customizable and extensible, allowing users to add their own plugins or extensions to enhance its functionality and tailor it to their specific needs. It is widely used by security professionals, penetration testers, and developers to identify and mitigate security vulnerabilities in web applications.
- Metasploit is a powerful and widely-used penetration testing framework that provides tools and resources for security professionals to perform comprehensive security assessments and exploit vulnerabilities in systems, networks, and applications. It is an open-source project maintained by Rapid7, a leading cybersecurity company. Metasploit is widely used by penetration testers, ethical hackers, and security researchers to identify vulnerabilities, assess security risks, and validate the effectiveness of security controls. It is a versatile framework that combines both automated and manual testing techniques to simulate real-world attacks and assist in securing systems and networks. Metasploit is built into Kali Linux, which is a popular Linux distribution widely used for penetration testing and ethical hacking. Kali Linux is specifically designed for security testing and includes a wide range of pre-installed tools, with Metasploit being one of the key components. When installing Kali Linux, penetration tester will have access to the Metasploit Framework by default. It is accessible through the command line interface (CLI) and provides a powerful set of tools for conducting penetration testing assessments, exploit development, vulnerability scanning, and post-exploitation activities.
- Sec-Sci AutoPT is an innovative and comprehensive penetration testing automation framework designed by ACR to streamline the process of identifying and mitigating security vulnerabilities in applications and systems. It leverages a combination of powerful tools, such as BurpSuite Pro, Docker, Cucumber, Cypress, Selenium, and Python, to automate the entire penetration testing workflow. Key Features and Functionality:
- Automated Scanning: The framework automatically sets the project to scan, initiating the automated scanning process using BurpSuite Pro. It allows for quick and accurate vulnerability assessments of web applications.
- Continuous Integration: Sec-Sci AutoPT is integrated into the build pipeline through a Continuous Integration (CI) server. It efficiently fetches code from the repository and triggers the pen testing process as needed.
- Versatile Testing Environment: The framework ensures consistent and isolated testing environments by utilizing Docker containerization. This enables efficient deployment and management of different testing setups.
- Customizable Automation: The integration of Cucumber, Cypress, Selenium, and Robot Framework with Python scripting provides a customizable and extendable automation capability. It supports both API service calls functionality testing and UI functionality testing.
- Security Assessment and Reporting: The automated pen testing platform executes the QA acceptance testing, running the appropriate testing tools (e.g., Docker, Cucumber, Cypress, Selenium, Robot Framework or Python) based on the project type. It allows for a thorough vulnerability scan process.
- Efficient Vulnerability Management: The framework allocates sufficient time for the vulnerability scan process to complete, ensuring comprehensive coverage of the target. Upon completion, it automatically closes Burp and archives old vulnerability reports for historical reference.
- Clear and Informative Reporting: Sec-Sci AutoPT generates comprehensive vulnerability reports. It also sends email notifications to relevant stakeholders, providing concise summaries of the security assessment results.
- Automated Scanning: The framework automatically sets the project to scan, initiating the automated scanning process using BurpSuite Pro. It allows for quick and accurate vulnerability assessments of web applications.
References:
https://wp.nyu.edu/dispatch/pentesting-for-your-ci-cd-pipeline
https://sysdig.com/learn-cloud-native/container-security/cicd-pipeline
https://www.harness.io/blog/integrating-automated-security-testing-ci-cd-pipeline
https://www.codingninjas.com/studio/library/risk-analysis-in-software-development
https://snyk.io/learn/what-is-ci-cd-pipeline-and-tools-explained/continuous-security/testing