Risk assessment in software development is the process of identifying, analyzing, and evaluating potential risks and uncertainties associated with a software project. It aims to proactively identify and address risks that could impact the success of the project, allowing project teams to make informed decisions and take appropriate actions to mitigate those risks. Risk assessment helps ensure that potential issues are identified early, minimizing their impact on project timelines, budgets, and quality.
Key aspects of risk assessment in software development
- Risk Identification: The first step in risk assessment is identifying potential risks specific to the software development project. This includes considering risks related to technology, requirements, resources, stakeholders, timelines, external dependencies, and regulatory compliance. Stakeholders, including project managers, developers, testers, and business representatives, can contribute to identifying risks based on their expertise and experience.
- Risk Analysis: Once risks are identified, they are analyzed to understand their likelihood of occurrence, potential impact, and the interdependencies between risks. This analysis helps assess the severity of each risk and prioritize them based on their significance. Techniques such as probability-impact matrix, risk categorization, and risk scoring can be used to assess and quantify risks.
- Risk Evaluation: Risks are evaluated to determine their acceptability and the need for further actions. This involves comparing the identified risks against predetermined risk thresholds or criteria. Risks that exceed the acceptable thresholds are considered high-priority and require immediate attention, while lower-priority risks may be monitored or managed with less intensive measures.
- Risk Mitigation Planning: Risk mitigation strategies and action plans are developed to address the high-priority risks. Mitigation strategies may involve risk avoidance (eliminating the risk by taking a different approach), risk reduction (implementing controls to minimize the likelihood or impact of risks), risk transfer (shifting the risk to another party, such as through insurance), or risk acceptance (acknowledging the risk without active mitigation). The plans outline specific activities, responsibilities, timelines, and resources required for risk mitigation.
- Risk Monitoring and Control: Risk monitoring is an ongoing process throughout the software development lifecycle. It involves tracking identified risks, their status, and the effectiveness of mitigation measures. Regular progress reviews and status updates help ensure that risks are being actively managed, and appropriate adjustments are made as needed. Risk control measures, such as implementing preventive controls, conducting periodic reviews, and updating risk mitigation plans, are applied to minimize the impact of risks.
- Risk Communication: Effective communication of risks is crucial in software development. Stakeholders need to be informed about identified risks, their potential impact, and the mitigation strategies in place. Clear and timely communication fosters understanding, alignment, and collaboration among team members and stakeholders, enabling them to collectively address risks and make informed decisions.
Risk assessment is an iterative process that should be conducted at various stages of the software development lifecycle. As the project progresses, new risks may emerge, and existing risks may evolve, requiring ongoing assessment and adjustment of mitigation strategies. By actively conducting risk assessment, software development teams can anticipate challenges, minimize surprises, and take proactive measures to ensure project success.
How to conduct a risk assessment?
Conducting a risk assessment in software development involves specific considerations tailored to the software development lifecycle. Here are the steps to conduct a risk assessment in software development:
- Define the Scope: Determine the scope of the risk assessment, including the specific software development project, system, or application under consideration. Identify the stakeholders involved, such as project managers, developers, testers, and business representatives.
- Identify Risks: Identify potential risks associated with the software development project. Consider risks related to technology, requirements, resources, timelines, stakeholders, security, privacy, and regulatory compliance. Engage stakeholders and use techniques like brainstorming, checklists, and lessons learned to identify risks specific to software development.
- Assess Likelihood and Impact: Evaluate the likelihood or probability of each identified risk occurring and assess its potential impact on the project. Consider factors such as complexity, dependencies, skill levels, historical data, and external factors. Assess both technical and non-technical risks, including risks related to software functionality, performance, security vulnerabilities, and project management.
- Estimating Likelihood: This step is to derive an overall likelihood rating that indicates the probability that a potential risk may occur within the construct of the associated risk environment, the following governing factors must be considered:
• Threat Agent Factors
• Vulnerability Factors
Each factor has a set of options, and each option has a likelihood rating from 0 to 9 associated with it. These numbers will be used later to estimate the overall likelihood.
- Threat Agent Factors: Threat agent factors refer to characteristics or attributes associated with potential threats or attackers that can exploit vulnerabilities. These factors help assess the likelihood and capability of threats to exploit vulnerabilities in a system. Examples of threat agent factors include the knowledge and skill level of the attacker, their access to resources or tools, their motivation or intent, and their level of persistence or determination.
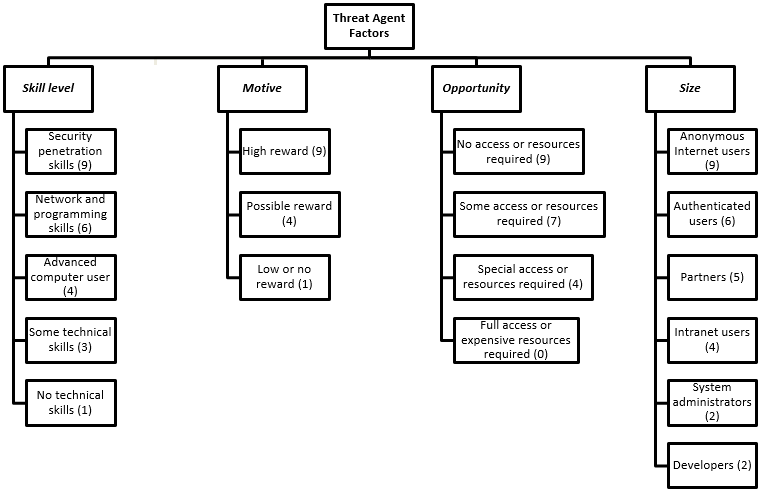 Skill Level: How technically skilled is this group of threat agents?
Skill Level: How technically skilled is this group of threat agents?
Motive: How motivated is this group of threat agents to find and exploit this vulnerability?
Opportunity: What resources and opportunities are required for this group of threat agents to find and exploit this vulnerability?
Size: How large is this group of threat agents?
Overall Threat Vector = ( Skill level + Motive + Opportunity + Size ) / 4 - Vulnerability Factors: Vulnerability factors pertain to the weaknesses or flaws within a system or environment that can be exploited by threat agents. These factors help evaluate the susceptibility of a system to be compromised or harmed. Vulnerability factors may include software bugs, misconfigurations, inadequate security controls, design flaws, weak authentication mechanisms, or insufficient data encryption. Assessing vulnerability factors helps identify areas where mitigation measures or controls should be implemented to reduce risks.

Ease of Discovery: How easy is it for this group of threat agents to discover this vulnerability?
Ease of Exploit: How easy is it for this group of threat agents to actually exploit this vulnerability?
Awareness: How well known is this vulnerability to this group of threat agents?
Intrusion Detection: How likely is an exploit to be detected?
Overall Vulnerability Factors = ( Ease of discovery + Ease of exploit + Awareness + Intrusion detection ) / 4
- Threat Agent Factors: Threat agent factors refer to characteristics or attributes associated with potential threats or attackers that can exploit vulnerabilities. These factors help assess the likelihood and capability of threats to exploit vulnerabilities in a system. Examples of threat agent factors include the knowledge and skill level of the attacker, their access to resources or tools, their motivation or intent, and their level of persistence or determination.
- Estimating Impact: The next major step in measuring level of risk is to determine the adverse impact resulting from a successful threat exercise of vulnerability. There are two kinds of impacts:
• Technical impact
• Business impact
The first is the "technical impact" on the application, the data it uses, and the functions it provides. The other is the "business impact" on the business and company operating the application.
Again, each factor has a set of options, and each option has an impact rating from 0 to 9 associated with it. The Security Consultant used these numbers to estimate the overall impact.
- Technical Impact: Technical impact refers to the consequences or effects that a risk event can have on the technical aspects of a system or environment. It focuses on the potential damage or disruption to the technological infrastructure, hardware, software, networks, or data. Technical impact can include data loss, system downtime, unauthorized access, corruption or alteration of data, compromised functionality, or the introduction of malware. Understanding the technical impact helps prioritize risks and determine appropriate mitigation strategies.
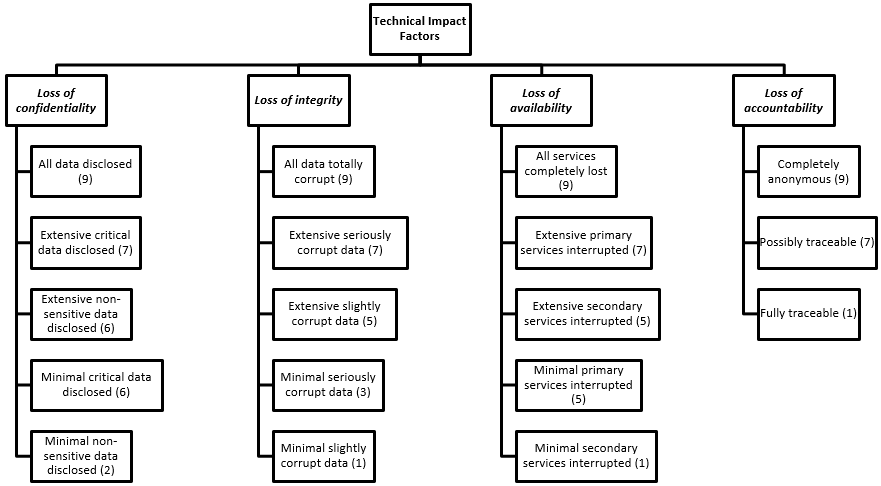
Loss of Confidentiality: How much data could be disclosed and how sensitive is it?
Loss of Integrity: How much data could be corrupted and how damaged is it?
Loss of Availability: How much service could be lost and how vital is it?
Loss of Accountability: Are the threat agents’ actions traceable to an individual?
Overall Technical Impact = ( Loss of confidentiality + Loss of integrity + Loss of availability + Loss of accountability ) / 4 - Business Impact: Business impact refers to the potential consequences or effects that a risk event can have on the overall business operations, objectives, or reputation. It involves considering the broader impact beyond the technical aspects, including financial losses, legal or regulatory non-compliance, reputational damage, customer trust erosion, loss of competitive advantage, operational disruptions, or negative impacts on brand value. Assessing business impact helps stakeholders understand the potential ramifications and make informed decisions regarding risk mitigation and resource allocation.
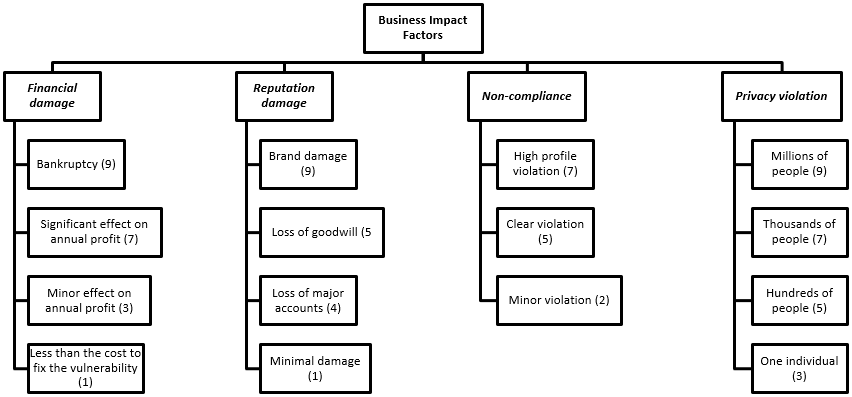
Financial damage: How much financial damage will result from an exploit?
Reputation damage: Would an exploit result in reputation damage that would harm the business?
Non-compliance: How much exposure does non-compliance introduce?
Privacy violation: How much personally identifiable information could be disclosed?
Overall Business Impact = ( Financial damage + Reputation damage + Non-compliance + Privacy violation ) / 4
- Technical Impact: Technical impact refers to the consequences or effects that a risk event can have on the technical aspects of a system or environment. It focuses on the potential damage or disruption to the technological infrastructure, hardware, software, networks, or data. Technical impact can include data loss, system downtime, unauthorized access, corruption or alteration of data, compromised functionality, or the introduction of malware. Understanding the technical impact helps prioritize risks and determine appropriate mitigation strategies.
- Determining Risk Severity: During this phase, the risk's likelihood estimate and impact estimate are combined to determine the overall severity of the risk. The likelihood and impact are each categorized as low, medium, or high on the 0 to 9 scale, dividing it into three segments:
Likelihood and Impact Levels High 6 to 9 Medium 3 to 5 Low 0 to <3
- Estimating Likelihood: This step is to derive an overall likelihood rating that indicates the probability that a potential risk may occur within the construct of the associated risk environment, the following governing factors must be considered:
- Analyze Root Causes: Understand the root causes and underlying factors contributing to each identified risk. Determine why the risks exist and explore the factors that make them more likely to occur. Analyze the impact of each risk on project objectives, timelines, quality, and stakeholder satisfaction.
- Quantify and Prioritize Risks: Quantify the identified risks based on their likelihood and impact assessment. Prioritize risks based on their significance and prioritize high-priority risks that require immediate attention. This helps allocate resources and prioritize risk mitigation efforts effectively.
- Develop Mitigation Strategies: Develop risk mitigation strategies and action plans for high-priority risks. Determine specific steps, measures, or controls that can be implemented to reduce the likelihood or impact of each risk. Assign responsibilities, set timelines, and allocate resources for implementing the mitigation strategies. Consider risk avoidance, risk transfer, risk reduction, and risk acceptance strategies.
- Monitor and Review: Continuously monitor and review the identified risks throughout the software development lifecycle. Regularly assess the effectiveness of implemented controls and mitigation measures. Update the risk assessment as new risks emerge, existing risks evolve, or project conditions change. Conduct periodic reviews and adjust the risk assessment and mitigation strategies as necessary.
- Communicate and Document: Communicate the findings of the risk assessment to relevant stakeholders. Provide clear documentation of the identified risks, their assessments, prioritization, and the proposed mitigation strategies. Ensure that stakeholders understand the risks and mitigation measures, fostering collaboration and shared responsibility.
- Integrate Risk Management: Integrate risk management into the software development process by incorporating risk analysis, mitigation, and monitoring activities as part of regular project activities. Ensure that risk management activities align with the project's overall planning, execution, and quality assurance processes.
- Learn and Improve: Capture lessons learned from the risk assessment process and apply them to future projects. Continuously improve the risk assessment methodology based on feedback and experiences. Foster a culture of risk awareness and proactive risk management within the software development team.
By conducting a comprehensive risk assessment in software development, teams can identify and address potential risks proactively, minimize project disruptions, and enhance the overall success of the software development endeavor.
Please note that risk assessment is an ongoing process, and it should be periodically revisited to account for changes in the environment, projects, or organizational context. Collaborating with stakeholders and utilizing appropriate risk assessment frameworks or standards can provide additional guidance and enhance the effectiveness of the process.
Determining Overall Risk Severity
Once the likelihood and impact estimates are obtained, merge them to determine the final severity rating for the risk. If reliable business impact information is available, it should take precedence over technical impact information. However, in the absence of business-specific data, the technical impact becomes the primary factor to consider.
Overall Likelihood = (Overall Threat Vector + Overall Vulnerability Factors) / 2
If Overall Vulnerability Factors is greater than 7.9
Overall Likelihood = (Overall Threat Vector + (Overall Vulnerability Factors + 1.8)) / 2
| Overall Risk Severity | ||||
|---|---|---|---|---|
| Impact | HIGH | Medium | High | Critical |
| MEDIUM | Low | Medium | High | |
| LOW | Informational | Low | Medium | |
| x | LOW | MEDIUM | HIGH | |
| x | Likelihood | |||
The following table defines the meaning of risk severity level
Vulnerability Risk Calculation = Overall Business Impact + (Overall Technical Impact * Overall Likelihood)
If Overall Technical Impact is greater that 7.9
Vulnerability Risk Calculation = Overall Business Impact + ((Overall Technical Impact + 1.8) * Overall Likelihood)
| Risk Value | Thematic Meaning |
|---|---|
| 130 and above |
Critical - These are risks that pose a severe and immediate threat to the organization if left unaddressed. They have the potential to cause significant harm, including enabling further attacks, compromising system integrity, compromising data confidentiality, or facilitating an attacker's penetration into the organization. Critical risks require urgent attention and mitigation to minimize the potential impact on the organization's operations, assets, and reputation. |
| 80 to <130 | High - These risks represent a substantial liability to the organization if not adequately addressed. While they may not pose an immediate threat like critical risks, they still have the potential to be exploited by attackers to further their attacks. If left unmitigated, high-risk items can increase the organization's overall risk exposure significantly. Each high-risk item should be evaluated and prioritized based on its potential impact and the likelihood of exploitation. |
| 40 to <80 |
Medium - These risks indicate a moderate increase in the organization's risk exposure. They may not individually present a significant threat, but in combination or when leveraged by attackers, they can lead to more substantial consequences. Although not as critical as high-risk items, medium-risk items should not be ignored, as they can contribute to the overall risk landscape and require appropriate measures to minimize their impact. |
| 0 to <40 | Low - These risks represent a relatively small increase in risk compared to the baseline. They are considered lower priority but still warrant attention and consideration. While their immediate impact may be minimal, organizations should be aware that low-risk items can escalate and become critical under specific circumstances. It is essential for the organization to understand the potential consequences and monitor these risks to prevent them from escalating into more significant threats. |
By categorizing risks as critical, high, medium, or low, organizations can prioritize their risk mitigation efforts and allocate resources effectively to address the most severe risks first. This classification helps in identifying and understanding the potential impact and urgency associated with each risk, facilitating a targeted approach to risk management and mitigation.
Risk Assessment Sample Results
Risk assessment sample results provide an overview of the identified risks, their likelihood, impact, and overall severity. The results help stakeholders understand the potential risks associated with a specific project, system, or process. Here's how risk assessment sample results are typically presented:
|
VULNERABILITY INFORMATION |
VULNERABILITY FACTORS |
TECHNICAL IMPACT |
RISK FACTOR |
||||
|---|---|---|---|---|---|---|---|
|
VULNERABILITY NAME |
AFFECTED ASSETS |
ROOT CAUSE |
OVERALL VULNERABILITY FACTORS |
OVERALL TECHNICAL IMPACT |
OVERALL LIKELIHOOD |
VULNERABILITY RISK CALCULATION |
RISK RATING |
|
Default Username and Password |
hr.company.com |
Development Flaw |
8.25 |
9 |
11.93 |
202.19 |
Critical |
|
SQL Injection |
marketing.company.com |
Development Flaw |
8.75 |
8.25 |
12.36 |
192.77 |
Critical |
|
Server Service Could Allow Remote Code Execution |
10.10.20.2 |
Patch Management |
7.5 |
8.50 |
7.38 |
116.04 |
High |
|
WordPress Username Enumeration |
finance.company.com |
Development Flaw |
9 |
7 |
11.73 |
85.28 |
High |
|
Weak Password |
techsupport.company.com |
Configuration Flaw |
9 |
7 |
11.73 |
85.28 |
High |
|
ProjectSend Arbitrary File Upload |
admin.company.com |
Patch Management |
7.5 |
8 |
7.38 |
109.40 |
High |
|
Malicious Image File Upload |
hr.company.com |
Development Flaw |
7 |
8 |
7.13 |
105.80 |
High |
|
Malware |
172.19.20.5 |
Patch Management |
5.25 |
8.5 |
6.25 |
98.83 |
High |
|
Unsecured Web-Based File Manager |
finance03.company.com |
Configuration Flaw |
6.25 |
8 |
6.75 |
100.40 |
High |
|
Unsecured FTP |
172.16.16.3 |
Configuration Flaw |
9 |
4.25 |
11.73 |
53.03 |
Medium |
|
Port Scan |
All Devices |
Configuration Flaw |
9 |
2.25 |
11.73 |
29.58 |
Low |
[ Download Vulnerability Register Risk Scoring | Vulnerability & Risk Register Companion Tool ]
References:
https://www.iso.org/standard/80585.html
https://csrc.nist.gov/publications/detail/sp/800-39/final
https://csrc.nist.gov/publications/detail/sp/800-30/rev-1/final
https://csrc.nist.gov/publications/detail/sp/800-37/rev-2/final
https://owasp.org/www-project-risk-assessment-framework
https://owasp.org/www-community/OWASP_Risk_Rating_Methodology