Threat modeling is a systematic approach to identify security requirements, assess, and pinpoint potential security threats and vulnerabilities, quantify threat and vulnerability criticality, and prioritize remediation methods, and mitigate potential threats and vulnerabilities in the system or application. It is a proactive technique used during the design phase of software development or when assessing the security of an existing system. Threat modeling engineering technique can be applied to a wide range of things, including software, applications, systems, networks, distributed systems, Internet of Things (IoT) devices, and business processes.
Threat modeling involves decomposing the system and identifying key risk-related components including assets, threat agents, attack vectors, and security controls. Threat modeling is not a method for code reviewing or penetration testing but, since it outputs risks, it can help drive a range of risk based activities. Threat modeling ultimately aims at identifying risks and flaws affecting a system. However, through a thorough analysis of the software architecture, business context, and other artifacts such as functional specifications and user documentation, the threat modeling process discovers many important aspects of the system, security-related or not, and synthesizes an understanding of the system that often does not yet exist within the organization. Threat modeling identifies risks that can be used as input to other activities such as security requirements identification, security test planning, security code reviewing and penetration testing.
Example of Threat Model Stack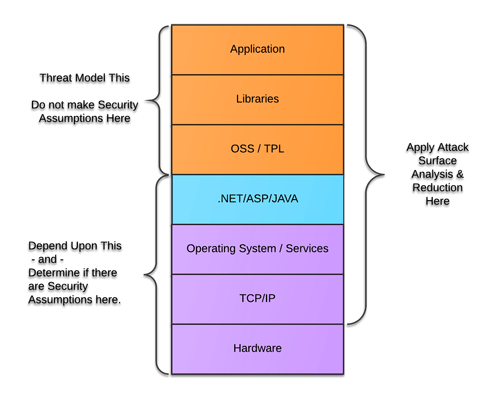 |
Example of Threat Model Diagram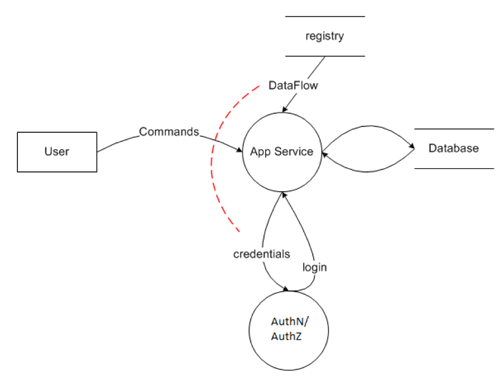 |
Threat Modeling Approach
Threat modeling is a core element of the Secure Software Development Lifecycle (SSDLC). It’s an engineering technique that can use to help identify threats, attacks, vulnerabilities, and countermeasures that could affect the application. The use of threat modeling can shape the application's design, meet the company's security objectives, and reduce risk. 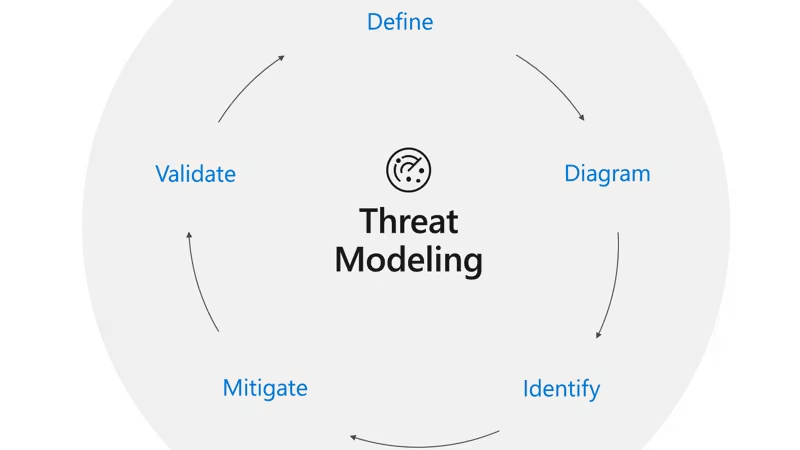
The five major threat modeling steps
- Defining security requirements.
- Creating an application diagram.
- Identifying threats.
- Mitigating threats.
- Validating that threats have been mitigated.
This guidance presents the patterns & practices approach in creating threat model for the application. Threat modeling is recommended to be part of the routine development lifecycle, enabling progressively to refine the threat model and further reduce risk.
Threat Assessment Criteria
For standardized Threat Modeling, the STRIDE approach is the reference and benchmark for scenarios of the assessment. An attack surface analysis was performed to identify the various entry points from which an attacker can potentially exploit the system. Based on the Threat Modeling analysis below is the list of high level criteria performed using dynamic approach during the assessment.
Terms used in Threat modeling
- Asset: An asset is a resource of value. It varies by perspective. To your business, an asset might be the availability of information, or the information itself, such as customer data. It might be intangible, such as your company's reputation. To an attacker, an asset could be the ability to misuse your application for unauthorized access to data or privileged operations.
- Threat: A threat is an undesired event. A potential occurrence, often best described as an effect that might damage or compromise an asset or objective. It may or may not be malicious in nature.
- Vulnerability: A vulnerability is a weakness in some aspect or feature of a system that makes an exploit possible. Vulnerabilities can exist at the network, host, or application levels and include operational practices.
- Attack (or exploit): An attack is an action taken that utilizes one or more vulnerabilities to realize a threat. This could be someone following through on a threat or exploiting a vulnerability.
- Countermeasure: Countermeasures address vulnerabilities to reduce the probability of attacks or the impacts of threats. They do not directly address threats; instead, they address the factors that define the threats. Countermeasures range from improving application design, or improving your code, to improving an operational practice.
Ranking of Threats
Threats can be ranked from the perspective of risk factors. By determining the risk factor posed by the various identified threats, it is possible to create a prioritized list of threats to support a risk mitigation strategy, such as prioritizing the threats to be mitigated first. Different risk factors can be used to rank threats as High, Medium, or Low risk. In general, threat risk models use different factors to model risks such as those shown below: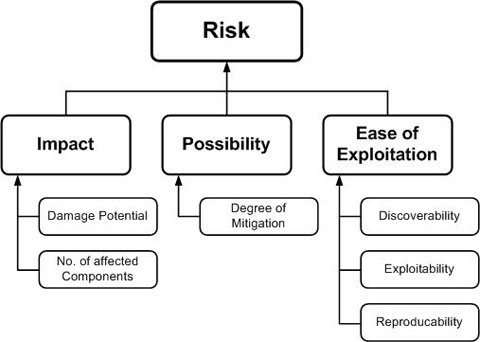
Ranking Risk Factors
A finding contains analysis and documentation of the threat identified within the assessed application. This analysis includes:
- Identifying the application’s security objectives, and surveying the application’s architecture and design documentation
- Decomposing the application and identifying threats
- Classifying known threats and assigning the appropriate risk rating
- Formulate actionable recommendations that improve the security posture of the application
Threats are grouped according to risk rating. Information for each of the threats includes the following:
- Name: The name of the threat.
- Description: Comprehensive explanation of the threat that was identified, including a high-level summary of the threat.
- Threat Traceability Matrix: A simplified threat model that describes how a threat agent can attack the application, the business impact and attack mitigation strategies.
The Threat Traceability Matrix
- Threat agent: an entity that can act against an asset and cause harm.
- Attack surface: the collection of points that the threat agent directly interacts with the system.
- Attack: the category, based on the STRIDE threat model, of the kinds of exploits the threat agent can use to attack the system.
- Assets: data, functionality, or a property of the system that a threat agent wants to access.
- Impact: the impact severity associated with a successful attack.
- Mitigation: recommended controls to implement that mitigate the threat.
DREAD Score
DREAD is a classification scheme for quantifying, comparing and prioritizing the amount of risk presented by each evaluated threat. DREAD risk assessment model, risk factorization allows the assignment of values to the different influencing factors of a threat. This provides a subjective process to rank threats. To determine the ranking of a threat, the threat analyst answers questions for each factor of risk, for example:
| Risk Category | Meaning | Dread Average Ranking |
|---|---|---|
| Damage Potential | How big would the damage be if the attack succeeded? | If a threat exploit occurs, evaluate the damage caused 1= Nothing 5= Individual user data compromised 10=Complete system or data destruction/just a web browser is enough |
| Reproducibility | How easy is it to reproduce an attack? | How easy is it to reproduce the threat exploit? 1 = Very hard or impossible even for administrators/DBAs 5 = One or two steps required, may need an authorized user 10= Possible by an unauthorized user |
| Exploitability | How much time, effort, and expertise is needed to exploit the threat? | What is needed to exploit this threat? 1 = Advanced programming & networking knowledge 5 = Malware exists on the Net, or any tolls available 10 = Just a web browser is enough |
| Affected Users | If a threat were exploited, what percentage of users would be affected? | How many users are affected? 1 = None 5 = Some users, but not all 10 = All users |
| Discoverability | How easy is it for an attacker to discover this threat? | How easy is it to discover the threat? 1 = Very hard or impossible; needs source code or admin access 5 = Can figure it out by guessing or monitoring network traces 10 = Information is visible in the web browser or address bar or in the form or as a hidden variable |
A point system of numbers 1-10, representing low to high severity, is used to calculate a DREAD score that can help compare one threat to another. Each category above is given a score between 1-10, then following formula is used to calculate the risk of a threat:
DREAD SCORE = ( Damage + Reproducibility + Exploitability + Affected Users + Discoverability ) / 5
The threat is then assigned a risk rating using the DREAD score and table below:
| Risk Rating | DREAD Score | Risk Description |
|---|---|---|
| High | 8-10 | High risk findings and threats should be considered for review and resolution within a short time frame. These threats can lead to a malicious actor gaining non-privileged access (standard user) to a system, or the vulnerability can be leveraged to gain elevated level of access. |
| Medium | 4-7 | Medium risk findings and threats should be considered once the critical and severe risks have been addressed. These threats may leak sensitive data that a malicious actor can use to assist in the exploitation of other threats. Moderate findings do not pose a substantial threat to business operations. |
| Low | 1-3 | Low risk findings and threats are informational and do not pose significant risk to the environment. |
When to threat model
There are several occasions when a threat modeling exercise should be performed:
- During the design phase of an application.
- During the design phase for new features.
- On existing applications for the purpose of proposing and implementing improved security controls.
Threat modeling offers several benefits for organizations
- Proactive Risk Mitigation: Threat modeling allows organizations to identify and address potential security risks early in the development lifecycle. By considering threats and vulnerabilities during the design phase, proactive measures can be implemented to mitigate risks effectively. This helps prevent security incidents and reduces the likelihood of costly remediation efforts later.
- Cost Savings: By identifying and mitigating potential risks early on, threat modeling can help organizations avoid the financial impact associated with security breaches, such as data loss, legal liabilities, and reputation damage. Investing in proactive security measures through threat modeling can save significant costs in the long run.
- Improved Security Posture: Threat modeling enables organizations to build a more secure architecture and design for their systems and applications. By identifying and addressing potential vulnerabilities, organizations can establish a stronger security foundation and reduce the attack surface available to potential adversaries.
- Enhanced Compliance: Threat modeling assists organizations in aligning their systems with security and privacy regulations, industry standards, and best practices. It enables organizations to identify and address gaps in compliance early, ensuring that appropriate security controls are in place to meet legal and regulatory requirements.
- Better Decision-Making: Threat modeling provides organizations with valuable insights into the potential risks and impacts of different security threats. This information allows for informed decision-making when prioritizing security efforts, allocating resources, and implementing security controls. It helps organizations focus their security efforts on the most critical and high-impact areas.
- Collaboration and Communication: Threat modeling encourages collaboration among different stakeholders, including developers, security professionals, architects, and business representatives. By involving various perspectives, threat modeling facilitates better communication and understanding of security risks and requirements. It promotes a shared understanding of security goals and facilitates effective collaboration across teams.
- Scalability and Adaptability: Threat modeling can be applied to systems of various sizes and complexity, from individual applications to large-scale enterprise architectures. It is a flexible approach that can be adapted to different development methodologies, technology stacks, and industries. This scalability and adaptability make threat modeling a valuable tool for organizations of all types.
Overall, threat modeling helps organizations proactively identify and mitigate security risks, leading to improved security, reduced vulnerabilities, and enhanced overall resilience. It supports informed decision-making, collaboration, and compliance with regulatory requirements. By embracing threat modeling, organizations can significantly strengthen their security posture and protect their critical assets and data.
Requirements
- Clearly defined functional workflows that encompass roles and permissions within the system, outlining how different user roles interact with the system and what actions they can perform.
- Well-documented business use cases that capture the intended scenarios and interactions within the system, including relevant personas and their characteristics, goals, and responsibilities.
- Detailed documentation of the authentication and authorization mechanisms employed by the system, specifying how user identities are verified, access privileges are granted, and sensitive operations are protected.
- Identification and classification of the different classes of data handled or processed by the system, considering their sensitivity, criticality, and potential impact if exposed or compromised.
- Utilization of UML diagrams to visually represent the system's architecture, including its components, relationships, and interfaces. These diagrams provide a clear overview of the system's structure, aiding in identifying potential vulnerabilities and attack vectors.
- Creation of interaction diagrams or sequence diagrams to depict the dynamic behavior of the system, illustrating the sequence of events, data flows, and interactions between system components, external entities, and users. These diagrams help in understanding potential security risks arising from the interactions..
By ensuring these requirements are met, organizations can effectively conduct threat modeling, identify potential security threats, assess associated risks, and develop appropriate countermeasures to enhance the overall security of the system
Managing Risks
Once risks have been identified and ranked using threat modeling, they can be managed through the following approaches:
- Ignore: This involves choosing to take no action on a risk, leaving it unhandled. However, ignoring risks is not advisable as it can expose the organization to legal and regulatory consequences for not exercising due diligence in protecting the system and customer data.
- Avoid (Eliminate): This approach involves adopting a different strategy to eliminate the risk, such as discontinuing the use of software or functionality. This may be suitable in cases where newer products replace legacy software or when the functionality is non-critical. It is important to note that risks should never be completely ignored and should be carefully considered.
- Mitigate (Remediate): This approach focuses on taking steps to reduce the risk level. This can include implementing security controls, reshaping requirements, and managing user expectations to secure a feature. Mitigation aims to reduce the likelihood and minimize the potential impact of the risk. Decision-makers should consider all aspects of the risk, including compliance and regulatory implications, and not rely solely on technical solutions for mitigation.
- Accept: Sometimes, the most cost-effective approach is to accept the risk. This may occur when the cost of implementing security controls outweighs the potential impact of the risk. In such cases, the business acknowledges and manages the risk, or the risk is mitigated to a level that management deems acceptable. It is important to document acceptance decisions and, preferably, have contingency plans to address any residual risk that could cause unacceptable impacts later.
- Transfer: This approach involves transferring the liability associated with a risk to another party. This can be done through disclaimers agreed upon by customers or by purchasing insurance to cover potential liability resulting from the exploitation of a software's risk. However, it should be understood that even though liability may be transferred, customers may still hold the organization accountable for any breaches, as brand damage can outweigh the protection provided by liability transfer.
It is essential to be aware of common pitfalls, such as conflating "Ignore" with "Accept" or considering "Avoid" as part of "Mitigate." Additionally, when transferring a risk, it is crucial to recognize that the risk itself remains, and customers may still hold the organization responsible for any breaches. Understanding each risk and its potential impact is paramount in effective risk management.
Recommendations
- Engage the Application Security Engineering Team Early: Involve the Application Security Engineering team as early as possible in the development process. Their expertise can help identify potential threats and vulnerabilities from the outset.
- Plan and Assign a Security Architect: Ensure that the threat modeling activity is planned at an early stage to allow for timely assignment of a security architect. Their involvement is crucial in guiding the threat modeling process effectively.
- Integrate with Architecture Design: Ideally, initiate the threat modeling activity during the Architecture Design phase. This early integration helps identify threats and security issues at the design stage, enabling prompt mitigation measures.
- Prioritize Completion Before Security Architecture Review: Aim to complete the threat modeling activity before the Security Architecture Review. This ensures that potential threats and vulnerabilities are identified and addressed early, providing valuable insights for the review process.
- Leverage Threat Modeling Documentation Tools: Utilize specialized threat modeling documentation tools to enhance the efficiency and effectiveness of the process. These tools can streamline threat identification, documentation, analysis, and reporting, facilitating collaboration among stakeholders.
By following these recommendations, organizations can ensure the timely involvement of security experts, integrate threat modeling into the development lifecycle, and leverage appropriate tools to maximize the benefits of the threat modeling process.
Time & Effort Needed
- The duration of the threat modeling task varies based on the complexity of the product and the scope of the effort.
- Typically, completing this task can take around 3-5 days, although the timeframe may vary depending on the specific product and circumstances.
- It's important to consider that the availability of necessary requirements and security architects involved in the threat modeling effort can impact the overall timeline.
- It's worth noting that threat modeling is an iterative process, requiring multiple passes to achieve completion and refinement.
Threat Modeling Tools
- Microsoft Threat Modeling Tool is one of the oldest and most tested threat modeling tools in the market. It is an open-source tool that follows the spoofing, tampering, repudiation, information disclosure, denial of service, and elevation of privilege (STRIDE) methodology. The Microsoft Threat Modeling Tool is a software tool developed by Microsoft to support the process of threat modeling for software applications and systems. Threat modeling is a structured approach used to identify, assess, and mitigate potential security threats and risks throughout the development lifecycle of a software application. The Microsoft Threat Modeling Tool is a valuable resource for organizations aiming to proactively identify and address security risks early in the software development lifecycle. By leveraging this tool, security professionals and development teams can enhance the security posture of their applications and systems by systematically considering and mitigating potential threats. Key features and capabilities of the Microsoft Threat Modeling Tool include:
- Visual Modeling: The tool provides a visual interface that allows security architects, developers, and stakeholders to create a graphical representation of the application's architecture, data flows, components, and trust boundaries. This visual model helps in understanding the system's design and identifying potential security vulnerabilities.
- Threat Identification: The tool assists in identifying and analyzing potential threats and attack vectors specific to the application being modeled. It helps in systematically evaluating different security risks and considering potential mitigations for each identified threat.
- Automated Analysis: The Microsoft Threat Modeling Tool supports automated analysis to identify common security issues and best practices violations within the threat model. It can generate reports highlighting areas of concern and suggesting remediation actions.
- Integration with Development Lifecycle: The tool integrates with popular development environments and processes, such as Microsoft Visual Studio, enabling seamless integration of threat modeling into the overall development workflow. It supports collaboration among developers, security teams, and other stakeholders during the threat modeling process.
- Customization and Extensibility: The tool allows customization of the threat modeling process and the creation of custom threat types, mitigations, and templates to fit specific application domains or organizational requirements.
- IriusRisk is a threat modeling platform that helps organizations integrate threat modeling into their software development processes. It provides a collaborative and streamlined approach to identify, assess, and mitigate security risks throughout the software development lifecycle. IriusRisk provides a collaborative and scalable approach to integrate threat modeling into the development process, enabling organizations to build secure and resilient software applications. By leveraging its features, organizations can enhance their understanding of potential threats and proactively implement security controls to mitigate risks. IriusRisk is a platform that automates the threat modeling process, enabling developers to design and build secure software and it has both a community edition and a standard edition. Key features and capabilities of IriusRisk include:
- Threat Modeling Framework: IriusRisk offers a structured framework for conducting threat modeling, allowing organizations to systematically analyze and document potential threats and risks specific to their applications and systems. It provides a visual representation of the system architecture, data flows, and trust boundaries.
- Risk Assessment and Mitigation: The platform enables organizations to assess the severity and likelihood of identified threats and prioritize mitigation efforts. It provides recommendations and suggestions for implementing appropriate security controls and countermeasures to mitigate the identified risks.
- Integration with Development Tools: IriusRisk integrates with popular development tools, such as Jira and Azure DevOps, enabling seamless integration of threat modeling activities into the software development workflow. This allows for better collaboration between security teams, developers, and other stakeholders.
- Compliance and Regulatory Support: IriusRisk supports compliance with industry standards and regulatory requirements by providing templates, guidelines, and controls mapping to various frameworks such as OWASP, PCI DSS, GDPR, and more. It helps organizations align their threat modeling practices with specific compliance mandates.
- Reporting and Visualization: The platform generates comprehensive reports and visualizations that communicate the identified threats, risks, and mitigation strategies to stakeholders. This facilitates decision-making and helps organizations prioritize security investments and resources effectively.
- Continuous Threat Modeling: IriusRisk promotes the concept of continuous threat modeling, allowing organizations to continuously assess and update threat models as the application evolves. This ensures that security considerations are consistently addressed throughout the application's lifecycle.
References:
https://owasp.org/www-community/Threat_Modeling
https://owasp.org/www-community/Threat_Modeling_Process
https://www.microsoft.com/en-us/securityengineering/sdl/threatmodeling
https://docs.microsoft.com/en-us/biztalk/core/sample-tma-http-and-soap-adapters