Author: Arnel C. Reyes
Published: 04 April 2025
Last Updated: 05 April 2025
RamiGPT is a proof of concept AI-powered offensive security agent engineered to gain root-level access on vulnerable systems with surgical precision and speed. Combining the automation and scripting prowess of PwnTools with the intelligent reasoning of OpenAI models, RamiGPT is built to analyze, exploit, and escalate privileges autonomously. In practice, RamiGPT has demonstrated its effectiveness by successfully rooting multiple VulnHub machines in under a minute, making it a formidable tool for red teamers and ethical hackers aiming to simulate advanced adversaries.
Background
The rise of artificial intelligence in cybersecurity has largely focused on defense -- threat detection, anomaly analysis, and response automation. However, the offensive side of cybersecurity is evolving just as rapidly. Traditional penetration testing often requires a blend of scripting, domain knowledge, and manual effort to assess modern digital infrastructures. With the complexity of systems increasing and threat landscapes expanding, the need for scalable, intelligent offensive tools became evident.
Traditional privilege escalation requires deep knowledge of operating systems, enumeration skills, and often significant manual trial-and-error. However, as systems grow more complex, the need for AI-driven tools that can rapidly adapt and make smart decisions becomes essential. RamiGPT was born out of this necessity -- to combine machine reasoning with hands-on exploit capabilities in a way that mimics a skilled human attacker.
At its core, RamiGPT uses PwnTools for binary interaction, shell manipulation, and payload delivery, while its OpenAI-based reasoning engine handles dynamic decision-making, interpreting system feedback, and choosing the most effective escalation vector. Whether it’s exploiting SUID binaries, weak cron jobs, misconfigured services, or kernel-level vulnerabilities, RamiGPT evaluates the scenario in real-time and executes the most promising path to root.
Its performance on VulnHub platforms -- where machines simulate real-world misconfigurations and exploits -- has proven that AI can shorten the privilege escalation lifecycle dramatically, often outperforming human operators in speed and consistency.
Unlike static scripts or basic automation, RamiGPT can engage in a dynamic interaction loop: observe results, reason about outcomes, and adjust strategies in real time. It can also interact via natural language, making it accessible to both seasoned security professionals and learners.
Using RamiGPT with OpenAI: Getting Started by Obtaining API Key
To unlock RamiGPT’s full capabilities, a valid OpenAI API key is needed. Follow these steps to obtain and configure it:
- Create an OpenAI Account
Go to https://platform.openai.com/signup and sign up for an account.
- Access the API Dashboard
Once logged in, navigate to the OpenAI API dashboard to view and manage API keys.
- Generate Your API Key
Click Create new secret key to generate API key. Be sure to copy and store it securely -- OpenAI will not show it again.
Running on Docker
- Prerequisites
Ensure the following are installed: - Clone the RamiGPT repository
$ git clone https://github.com/M507/RamiGPT.git
$ cd RamiGPT - Configuring the API Key for the Environment Variable
Copy the .env.example file in the root directory of the RamiGPT projectand name it .env.
$ cp .env.example .env - Add API Key: Open the .env file and add the following line:
$ nano .env
OPENAI_API_KEY=OpenAI-API-Key - Open docker-compose.yml and change the command to fix errors:
$ nano docker-compose.yml
command: >
sh -c "export TERM=xterm && chmod +x ./generate_certs.sh && ./generate_certs.sh &&
pip install --upgrade pip && pip install -r requirements.txt &&
flask run --host=0.0.0.0 --port=5000 --cert=cert.pem --key=key.pem" - Launch the Docker container
$ docker compose up -d - Access the RamiGPT application at:
https://127.0.0.1:5000 or https://{local.ip.address}:5000
Running Locally
- Prerequisites
Ensure the following are installed:
- Python 3.x and pip
- OpenAI Key
- Python 3.x and pip
- Setup
Clone the repository:
$ git clone https://github.com/M507/RamiGPT.git
$ cd RamiGPT - Prepare the environment:
$ chmod +x ./generate_certs.sh
$ ./generate_certs.sh
$ pip3 install -r requirements.txt - Run the app
$ python3 app.py - Access the RamiGPT application at:
https://127.0.0.1:5000 or https://{local.ip.address}:5000
Vulnerable Test Machine
- Download the Escalate Linux 1 from VulnHub:
https://www.vulnhub.com/entry/escalate_linux-1,323/ - Install VirtualBox or VMWare Workstation
- Import Escalate Linux 1 into VirtualBox or VMWare Workstation
- Configure Network Settings using Bridge Adapter
- Run the Vulnerable Test Machine
- Discover the IP Address of the Vulnerable Test Machine using the following command:
For Linux:$ netdiscover
For Windows:$ arp -a
Penetration Testing Using RamiGPT
- Access the RamiGPT application at:
https://127.0.0.1:5000 or https://{local.ip.address}:5000
Supply the details of the Vulnerable Test Machine then click "Connect" button.
- Once connected, run ifconfig and id commands to verify target machine as well as current user privilege.
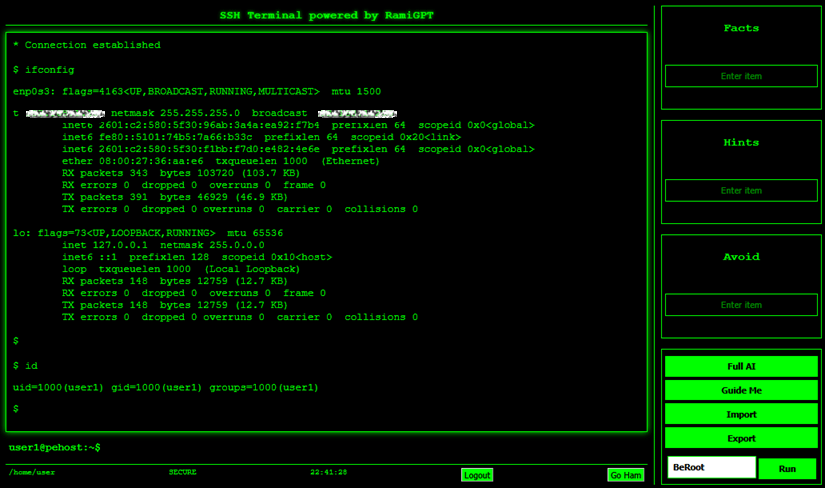
- Click the "Full AI" button to initiate Penetration Testing with AI.
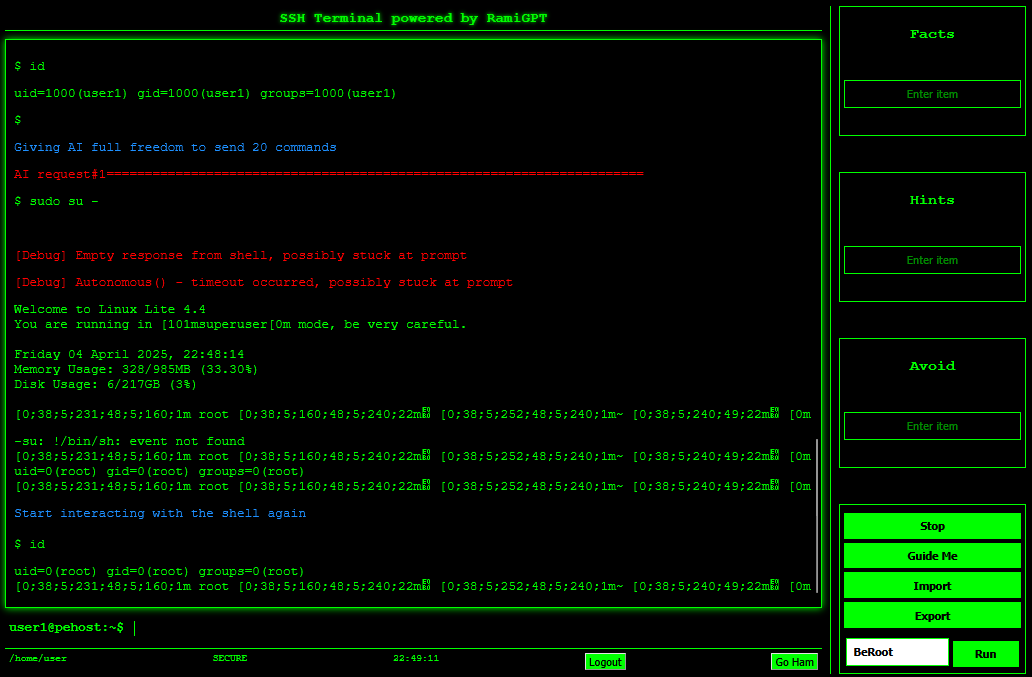
Note: Run id command again to check current user privilege if it gained root access.
Conclusion
AI-powered offensive security agents like RamiGPT are redefining the boundaries of ethical hacking and red teaming. By merging the reasoning capabilities of language models with the precision of penetration testing tools, they provide a scalable, intelligent, and adaptive layer to offensive security. While such tools raise important questions about dual-use and responsible AI, they also offer tremendous potential in training environments, bug bounty programs, and proactive defense initiatives.
RamiGPT exemplifies the next generation of AI-enhanced red teaming tools, blending deep exploitation frameworks with language model intelligence to autonomously reach root. Its success on VulnHub showcases its real-world relevance and potential for broader applications—from training environments to advanced adversary emulation.
While such a powerful agent brings up ethical and security concerns, its use in controlled environments highlights how AI can be a force multiplier in cybersecurity research and testing. With tools like RamiGPT, offensive security isn’t just faster—it’s smarter, more adaptive, and increasingly autonomous. As cybersecurity continues to evolve, so will the role of AI in simulating attackers’ minds—ultimately strengthening defenses through smarter, faster, and more comprehensive offensive assessments. RamiGPT is not just a tool—it's the inception of a new generation of intelligent adversaries built to make systems more secure.
Disclaimer: This documentation is intended for educational purposes only. The content provided herein is meant to inform and educate individuals about security practices, techniques, and tools. Security-Science does not support, endorse, or encourage any illegal or unethical activities, including but not limited to unauthorized access to computer systems, networks, or data. Users are advised to apply the knowledge gained responsibly and ensure compliance with all applicable laws and regulations. Security-Science shall not be held liable for any misuse of the information provided.