Author: Arnel C. Reyes
Published: 02 March 2025
Last Updated: 04 March 2025
A Holistic Cloud Security Defense-In-Depth (DiD) Strategy is a multi-layered approach designed to protect cloud environments by mitigating threats at multiple levels: data, applications, endpoints, and networks. As organizations increasingly migrate to the cloud, they encounter security challenges such as unauthorized access, data breaches, and misconfigurations. Unlike traditional IT security, cloud security demands a dynamic and adaptive strategy that incorporates the shared responsibility model, Zero Trust principles, automated threat detection and risks mitigation.
Background
A Defense-In-Depth approach ensures security is embedded across four key layers: data, applications, endpoints, and networks. Data security protects sensitive information through encryption (at rest, in transit, and in use), access controls like Role-Based Access Control (RBAC), Data Loss Prevention (DLP), and secure backup and recovery solutions. Application security ensures software integrity by implementing secure coding practices, API security, Web Application security, runtime protection, vulnerability scanning through Software Composition Analysis (SCA), Static Application Security Testing (SAST), Dynamic Application Security Testing (DAST), Threat Modeling, and Application Security Architecture review. Endpoint security safeguards cloud workloads with Endpoint Detection and Response (EDR), Zero Trust device management, automated patching, and cloud-native malware protection. Network security enforces isolation and segmentation using microsegmentation, Virtual Private Cloud (VPC) security, Zero Trust Network Access (ZTNA), and Distributed Denial of Service (DDoS) protection to prevent cyberattacks.
A Holistic Cloud Security Defense In-Depth Strategy further strengthens security through essential risk management and threat detection mechanisms. Vulnerability Management ensures continuous identification and remediation of security flaws, reducing the attack surface. Risk Management prioritizes potential threats, enabling proactive mitigation. Auditing, Logging, and Monitoring provide real-time visibility into cloud activities, while Security Information & Event Management (SIEM) correlates security events for proactive threat detection and incident response. Compliance & Standards enforce regulatory and industry best practices to align security with legal and business requirements. In the event of a security breach, Digital Forensics investigates attack vectors to strengthen future defenses. Vulnerability Assessment helps identify weaknesses, and Penetration Testing simulates real-world attacks to validate security controls. All this combined forms a comprehensive, multi-layered defense strategy that strengthens cloud security resilience, mitigates evolving cyber threats, and ensures strict adherence to regulatory requirements and industry security standards.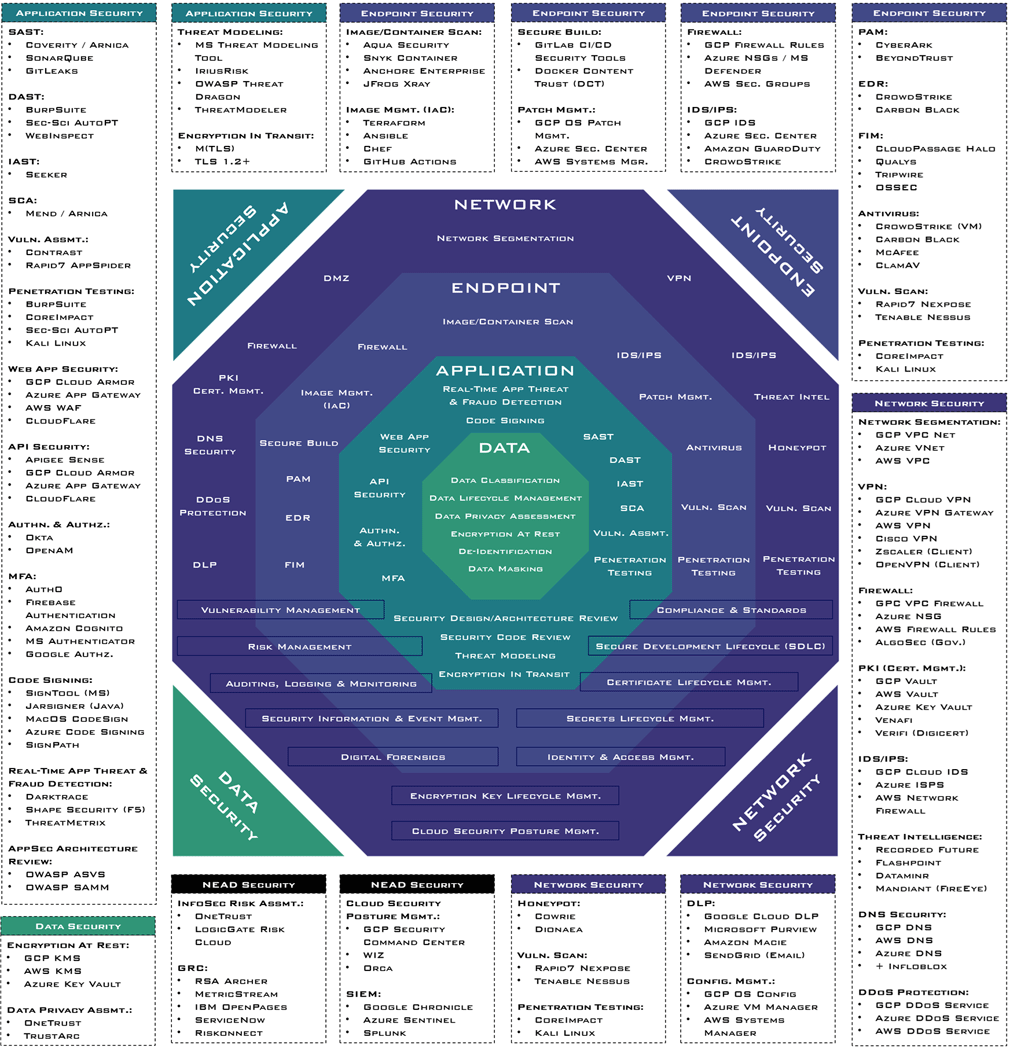
Network security is a fundamental aspect of a Holistic Cloud Security Defense-In-Depth Strategy, ensuring the integrity, confidentiality, and availability of cloud communications and infrastructure. Network segmentation isolates critical systems to limit lateral movement in case of a breach, while Demilitarized Zones (DMZs) create controlled boundaries between internal networks and external traffic to enhance security. Honeypots act as decoys to detect and analyze malicious activity without exposing actual assets. Distributed Denial-of-Service (DDoS) protection mitigates volumetric attacks that can disrupt cloud services. Firewalls enforce traffic filtering rules, and Intrusion Detection and Prevention Systems (IDS/IPS) monitor and block suspicious activities. Virtual Private Networks (VPNs) encrypt remote connections, ensuring secure access to cloud resources. Threat intelligence leverages real-time insights into emerging cyber threats to enhance proactive defense strategies. Public Key Infrastructure (PKI) and certificate management secure communications through encryption and authentication mechanisms. DNS security prevents domain hijacking, phishing, and malware distribution by monitoring and filtering malicious DNS requests. Data Loss Prevention (DLP) ensures sensitive data is not leaked or exfiltrated. Vulnerability scanning identifies weaknesses in network infrastructure, while penetration testing simulates real-world attacks to assess and strengthen defenses. By integrating these security measures, organizations fortify their cloud networks against cyber threats, ensuring secure and resilient connectivity.
Network Segmentation:
- GCP VPC Net
- Description: Google Cloud Virtual Private Cloud (VPC) allows you to create a private network within Google Cloud to isolate and secure resources.
- Features: Custom IP range, firewall rules, internal DNS, VPN support.
- Benefits: Enhances security by isolating resources and controlling access, with flexible network configurations.
- URL: https://cloud.google.com/vpc - Azure VNet
- Description: Azure Virtual Network (VNet) is a networking service that enables secure communication between Azure resources.
- Features: Network segmentation, security controls, hybrid connectivity, private IPs.
- Benefits: Provides enhanced security and flexible network topologies to isolate sensitive workloads.
- URL: https://azure.microsoft.com/en-us/services/virtual-network/ - AWS VPC
- Description: AWS Virtual Private Cloud (VPC) allows users to define their private network within AWS.
- Features: Customizable subnets, routing tables, security groups, VPN.
- Benefits: Ensures network isolation and secure communication between AWS resources.
- URL: https://aws.amazon.com/vpc/
VPN (Virtual Private Network):
- GCP Cloud VPN
- Description: A fully managed VPN solution that securely connects your on-premises network to Google Cloud.
- Features: High availability, IPsec tunnel, Cloud Router integration.
- Benefits: Ensures secure communication between on-premises and cloud resources.
- URL: https://cloud.google.com/network-connectivity/docs/vpn - Azure VPN Gateway
- Description: A VPN service that connects on-premises networks to Azure securely using encrypted tunnels.
- Features: Site-to-site, point-to-site VPN, route-based VPN, secure traffic.
- Benefits: Enhances network security by providing a secure link to Azure resources.
- URL: https://azure.microsoft.com/en-us/services/vpn-gateway/ - AWS VPN
- Description: AWS VPN provides secure site-to-site or client VPN connections to AWS.
- Features: IPsec tunnels, automatic failover, integration with AWS Transit Gateway.
- Benefits: Securely extends on-premises networks to AWS cloud environments.
- URL: https://aws.amazon.com/vpn/ - Cisco VPN
- Description: Cisco's VPN solutions offer secure remote access and site-to-site connectivity.
- Features: VPN Client, AnyConnect, IPsec, SSL VPN.
- Benefits: Provides secure remote access to enterprise resources over untrusted networks.
- URL: https://www.cisco.com/c/en/us/products/security/vpn.html - Zscaler
- Description: Zscaler offers a cloud-based VPN service for secure access to applications and resources.
- Features: Zero trust security, global cloud architecture, real-time threat detection.
- Benefits: Secure, scalable remote access for users regardless of location.
- URL: https://www.zscaler.com/ - OpenVPN
- Description: OpenVPN provides open-source VPN solutions for secure connectivity.
- Features: Strong encryption, cross-platform support, flexible configuration.
- Benefits: Cost-effective, highly customizable VPN for secure remote access.
- URL: https://openvpn.net/
Firewall:
- GCP VPC Firewall
- Description: A firewall solution within Google Cloud to control incoming and outgoing traffic to/from your VPC.
- Features: Stateful inspection, customizable rules, integration with VPC.
- Benefits: Protects cloud resources from unauthorized access and attacks.
- URL: https://cloud.google.com/vpc/docs/firewalls - Azure NSG
- Description: Azure Network Security Groups (NSG) filter traffic to and from Azure resources within a VNet.
- Features: Rule-based traffic filtering, integration with VNets, logging.
- Benefits: Offers fine-grained control over traffic flow within Azure environments.
- URL: https://azure.microsoft.com/en-us/services/network-security/ - AWS Firewall Rules
- Description: AWS security groups and network ACLs control inbound and outbound traffic in and out of AWS resources.
- Features: Customizable security rules, integrated with VPCs, logging.
- Benefits: Helps protect AWS resources from unauthorized access and attacks.
- URL: https://aws.amazon.com/vpc/ - AlgoSec (Governance)
- Description: AlgoSec provides security management solutions that help organizations secure their firewalls and networks.
- Features: Policy management, firewall security auditing, segmentation optimization.
- Benefits: Simplifies security management and ensures compliance with internal and external regulations.
- URL: https://www.algosec.com/
PKI (Public Key Infrastructure) & Certificate Management:
- GCP Vault
- Description: Google Cloud Vault is a secrets management service for storing and controlling access to API keys, passwords, certificates, and other sensitive information.
- Features: Encryption at rest, fine-grained access control, versioning.
- Benefits: Securely stores secrets, ensures compliance, and reduces risk.
- URL: https://cloud.google.com/vault - AWS Vault
- Description: AWS Secrets Manager and AWS KMS are tools to manage secrets and keys securely in AWS.
- Features: Automated secrets rotation, versioning, key management, fine-grained access control.
- Benefits: Protects sensitive information with automatic encryption and key management.
- URL: https://aws.amazon.com/secrets-manager/ - Azure Key Vault
- Description: Azure Key Vault helps safeguard keys, secrets, and certificates used by cloud applications and services.
- Features: Secure key management, access control, audit logging.
- Benefits: Protects cryptographic keys and secrets in a centralized, secure location.
- URL: https://azure.microsoft.com/en-us/services/key-vault/ - Venafi
- Description: Venafi provides enterprise-scale public key infrastructure (PKI) management and protection solutions.
- Features: Certificate lifecycle management, key management, encryption policy enforcement.
- Benefits: Ensures security and compliance by managing certificates and keys across the organization.
- URL: https://www.venafi.com/ - Verifi (Digicert)
- Description: A certificate authority offering PKI solutions for encrypting and authenticating data.
- Features: SSL/TLS certificates, automated certificate management, encryption, authentication.
- Benefits: Secures communications and verifies identity using trusted certificates.
- URL: https://www.digicert.com/
IDS/IPS:
- GCP Cloud IDS
- Description: Google Cloud's Intrusion Detection System (IDS) helps detect malicious network traffic in real-time.
- Features: Traffic analysis, anomaly detection, integration with other security services.
- Benefits: Protects cloud workloads by detecting and responding to network-based threats.
- URL: https://cloud.google.com/security - Azure ISPS
- Description: Azure Intrusion Detection and Prevention System (IDPS) offers protection against unauthorized access and attacks within Azure environments.
- Features: Real-time monitoring, attack detection, automated responses.
- Benefits: Enhances security by detecting threats early and preventing unauthorized network activity.
- URL: https://azure.microsoft.com/en-us/services/security-center/ - AWS Network Firewall
- Description: AWS Network Firewall provides a flexible, managed service for network traffic inspection and filtering in AWS environments.
- Features: Stateful inspection, intrusion prevention, customizable rules.
- Benefits: Protects VPCs from potential threats and enables granular control over network traffic.
- URL: https://aws.amazon.com/network-firewall/
Threat Intelligence:
- Recorded Future
- Description: A leading threat intelligence platform that provides real-time information on cyber threats and risks by analyzing vast amounts of data from multiple sources.
- Features: Predictive analytics, machine learning-driven insights, real-time alerts, customizable threat feeds.
- Benefits: Enhances decision-making, improves incident response, proactively identifies threats, and reduces security risks.
- URL: https://www.recordedfuture.com - Flashpoint
- Description: A threat intelligence platform focusing on high-fidelity data and contextual intelligence from criminal and hacker activities.
- Features: Threat intelligence feeds, advanced monitoring, cybercrime insights, actionable intelligence.
- Benefits: Provides real-time, actionable data to defend against emerging threats, supports risk mitigation and incident response.
- URL: https://www.flashpoint-intel.com - Dataminr
- Description: A real-time event detection and analytics tool that identifies critical events in the cybersecurity landscape by analyzing public data.
- Features: Real-time alerts, AI-driven detection, public data monitoring.
- Benefits: Helps organizations stay ahead of threats, provides rapid situational awareness, and supports proactive defense.
- URL: https://www.dataminr.com - Mandiant (FireEye)
- Description: A globally recognized cybersecurity company offering threat intelligence and incident response services.
- Features: Threat intelligence, incident response, cyberattack attribution, proactive threat detection.
- Benefits: Provides expert analysis and response to complex cyber threats, enhancing defense strategies.
- URL: https://www.mandiant.com
DNS Security:
- GCP DNS
- Description: Google Cloud DNS is a scalable and highly available Domain Name System service for Google Cloud users.
- Features: Global Anycast network, automatic scaling, DNSSEC support.
- Benefits: Fast, secure, and reliable DNS service with robust security features and high availability.
- URL: https://cloud.google.com/dns - AWS DNS
- Description: Amazon Route 53 is a scalable DNS web service for managing domain names and directing traffic to cloud resources.
- Features: Health checking, DNS routing policies, support for DNSSEC.
- Benefits: Scalable, low-latency, secure DNS service designed for high-availability applications.
- URL: https://aws.amazon.com/route53 - Azure DNS
- Description: Microsoft Azure DNS is a hosting service for DNS domains, providing high-performance and reliable DNS services.
- Features: Integration with Azure services, high availability, custom DNS records.
- Benefits: Ensures reliable DNS resolution, integrates well with Azure infrastructure, and provides enhanced security features.
- URL: https://azure.microsoft.com/en-us/services/dns - Infoblox
- Description: Infoblox offers secure DNS, DHCP, and IP address management (DDI) solutions to protect against DNS-based attacks.
- Features: DNS security, automated IP address management, DDI protection.
- Benefits: Protects against DNS tunneling, malware, and DDoS attacks, improving overall network security.
- URL: https://www.infoblox.com
DDoS Protection:
- GCP DDoS Service
- Description: Google Cloud provides DDoS protection as part of its network infrastructure to protect against large-scale attacks.
- Features: Automated protection, traffic filtering, real-time monitoring.
- Benefits: Seamlessly defends against DDoS attacks, ensuring high availability of cloud resources.
- URL: https://cloud.google.com/security - Azure DDoS Service
- Description: Azure DDoS Protection offers defense against DDoS attacks, ensuring applications stay available during attacks.
- Features: Real-time attack mitigation, traffic monitoring, automatic attack detection.
- Benefits: Protects critical applications from DDoS threats, minimizes downtime, and ensures business continuity.
- URL: https://azure.microsoft.com/en-us/services/ddos-protection - AWS DDoS Service
- Description: AWS Shield provides DDoS protection to secure AWS applications from external threats.
- Features: Managed DDoS protection, traffic anomaly detection, mitigation support.
- Benefits: Reduces the risk of DDoS attacks disrupting cloud applications, with automated and manual protection options.
- URL: https://aws.amazon.com/shield
DLP (Data Loss Prevention):
- Google Cloud DLP
- Description: Google Cloud DLP is a service that helps organizations detect and prevent data leaks across their cloud infrastructure.
- Features: Content inspection, data classification, data masking, and risk analysis.
- Benefits: Helps maintain data privacy and compliance by protecting sensitive information.
- URL: https://cloud.google.com/dlp - Microsoft Purview
- Description: Microsoft Purview offers unified data governance and compliance management for cloud and on-premises data.
- Features: Data cataloging, classification, access control, auditing, and compliance reporting.
- Benefits: Ensures data security and compliance, protecting sensitive information and mitigating risks.
- URL: https://www.microsoft.com/en-us/microsoft-365/compliance/purview - Amazon Macie
- Description: Amazon Macie is a machine learning-powered data security service that automatically detects and protects sensitive data like personally identifiable information (PII).
- Features: PII detection, data access monitoring, anomaly detection.
- Benefits: Helps safeguard sensitive data and ensure compliance with data privacy regulations.
- URL: https://aws.amazon.com/macie - SendGrid (Email)
- Description: SendGrid provides email-based data protection, helping secure email communications and prevent data leakage.
- Features: Email encryption, content filtering, authentication.
- Benefits: Protects sensitive information sent via email, ensuring secure communication and compliance.
- URL: https://sendgrid.com
Configuration Management:
- GCP OS Config
- Description: Google Cloud OS Config enables automation and management of operating system patches and configurations across virtual machines.
- Features: Patch management, configuration enforcement, automation, integration with Google Cloud.
- Benefits: Ensures systems are securely configured and up to date, reducing security vulnerabilities.
- URL: https://cloud.google.com/compute/docs/os-config - Azure VM Manager
- Description: Azure VM Manager is a tool for managing and configuring virtual machines in the Azure environment.
- Features: Centralized management, VM scaling, OS updates, configuration enforcement.
- Benefits: Simplifies VM management, ensuring consistent security and configuration across environments.
- URL: https://azure.microsoft.com/en-us/services/virtual-machine-scale-sets - AWS Systems Manager
- Description: AWS Systems Manager offers a unified interface for managing and automating cloud resources and systems.
- Features: Automation, patching, configuration management, security monitoring.
- Benefits: Streamlines management and ensures consistency and security across cloud resources.
- URL: https://aws.amazon.com/systems-manager
Honeypot:
- Cowrie
- Description: Cowrie is a low-interaction SSH and Telnet honeypot designed to log attacks and monitor unauthorized access attempts.
- Features: SSH and Telnet emulation, detailed logging, attack simulation.
- Benefits: Helps in detecting malicious activity, improving security monitoring, and gathering threat intelligence.
- URL: https://github.com/cowrie/cowrie - Dionaea
- Description: Dionaea is a honeypot designed to capture and analyze malware by simulating vulnerable services.
- Features: Malware capture, interaction with exploit attempts, detailed logging.
- Benefits: Gathers valuable data on new exploits and malware, improving security threat intelligence.
- URL: https://github.com/DinoTools/dionaea
Vulnerability Scan:
- Rapid7 Nexpose
- Description: Nexpose is a vulnerability management solution that identifies, assesses, and prioritizes vulnerabilities in real-time.
- Features: Real-time scanning, vulnerability prioritization, reporting, risk assessment.
- Benefits: Helps reduce risks and security breaches by identifying and addressing vulnerabilities early.
- URL: https://www.rapid7.com/products/nexpose - Tenable Nessus
- Description: Nessus is a popular vulnerability scanning tool used to identify vulnerabilities, misconfigurations, and malware.
- Features: Scans for vulnerabilities, configuration issues, and malware, with comprehensive reporting.
- Benefits: Helps prevent security breaches by proactively identifying vulnerabilities.
- URL: https://www.tenable.com/products/nessus
Penetration Testing:
- CoreImpact
- Description: A comprehensive penetration testing tool that automates vulnerability assessments and simulates attacks to assess an organization’s security posture.
- Features: Automated exploit testing, integration with other security tools, detailed reporting.
- Benefits: Identifies security gaps and vulnerabilities by simulating real-world attacks in a controlled environment.
- URL: https://www.coresecurity.com/core-impact - Kali Linux
- Description: A Linux distribution packed with security tools for penetration testing, vulnerability analysis, and ethical hacking.
- Features: Over 600 tools for penetration testing, security auditing, and forensics.
- Benefits: Provides a robust environment for testing security flaws and vulnerabilities.
- URL: https://www.kali.org/
Endpoint security is a critical component of a Holistic Cloud Security Defense-In-Depth Strategy, ensuring that cloud workloads, virtual machines, and containers remain secure against evolving threats. Image and container scanning identifies vulnerabilities and misconfigurations in containerized applications before deployment. Firewalls enforce network traffic control, while Intrusion Detection and Prevention Systems (IDS/IPS) monitor and block malicious activities in real time. Patch management ensures that endpoints receive timely security updates, reducing the risk of exploits. Antivirus solutions protect against malware, ransomware, and other endpoint threats. Infrastructure-as-Code (IaC) image management enforces security policies in pre-built templates to ensure consistent and hardened deployments. Secure build practices integrate security into DevOps pipelines, preventing misconfigurations and vulnerabilities in cloud environments. Privileged Access Management (PAM) restricts and monitors high-level access to critical systems, reducing insider threats. Endpoint Detection and Response (EDR) provides continuous monitoring and automated threat response to detect and mitigate endpoint-based attacks. File Integrity Monitoring (FIM) tracks changes to critical files and alerts on unauthorized modifications. Vulnerability scanning identifies security weaknesses in endpoints, while penetration testing simulates real-world attacks to assess endpoint defenses. By integrating these security controls, organizations enhance endpoint protection, prevent unauthorized access, and maintain a resilient security posture in cloud environments.
Image/Container Scan:
- Aqua Security
- Description: A security platform for containerized applications, designed to scan and protect container images.
- Features: Real-time scanning, vulnerability management, policy enforcement.
- Benefits: Protects containerized environments from security vulnerabilities and misconfigurations.
- URL: https://www.aquasec.com/ - Snyk Container
- Description: A solution for securing container images by scanning for vulnerabilities in real-time.
- Features: Integration with CI/CD pipelines, supports Docker and Kubernetes, automatic vulnerability fixes.
- Benefits: Helps DevOps teams build secure containerized applications faster and more efficiently.
- URL: https://snyk.io/ - Anchore Enterprise
- Description: A container security platform that automates the process of scanning container images for vulnerabilities.
- Features: Image scanning, policy management, vulnerability analysis, integration with CI/CD.
- Benefits: Increases container security by automating vulnerability detection and compliance checks.
- URL: https://anchore.com/ - JFrog Xray
- Description: A comprehensive security and compliance scanning solution for containers, artifacts, and dependencies.
- Features: Deep recursive scanning, integration with CI/CD, vulnerability and license compliance monitoring.
- Benefits: Helps teams secure artifacts throughout the entire software development lifecycle.
- URL: https://www.jfrog.com/xray/
Image Management (Infrastructure as Code):
- Terraform
- Description: An open-source IaC tool for managing and provisioning infrastructure using code.
- Features: Multi-cloud support, modular configurations, automated infrastructure deployment.
- Benefits: Improves infrastructure management and scalability through automation.
- URL: https://www.terraform.io/ - Ansible
- Description: An automation tool for configuration management, application deployment, and task automation.
- Features: Simple automation, agentless, extensible.
- Benefits: Streamlines operations, reduces manual work, enhances security by automating IaC deployments.
- URL: https://www.ansible.com/ - Chef
- Description: A powerful automation platform that manages infrastructure as code, enabling deployment and compliance.
- Features: Customizable cookbooks, compliance automation, integration with cloud providers.
- Benefits: Reduces configuration drift and secures infrastructure across environments.
- URL: https://www.chef.io/ - GitHub Actions
- Description: A CI/CD tool for automating workflows and integrating with the GitHub ecosystem.
- Features: Automation of testing, deployment, container builds, and IaC.
- Benefits: Automates and secures workflows directly within GitHub, improving developer productivity.
- URL: https://github.com/features/actions
Secure Build:
- GitLab CI/CD Security Tools
- Description: Built-in security features within GitLab CI/CD to integrate security into the software development pipeline.
- Features: SAST, DAST, dependency scanning, container scanning.
- Benefits: Automates security checks in development, ensures early vulnerability detection.
- URL: https://about.gitlab.com/ - Docker Content Trust (DCT)
- Description: A Docker feature that enables signing and verification of images to ensure their authenticity.
- Features: Image signing, verification, policy enforcement.
- Benefits: Secures the integrity of images by preventing unauthorized changes and tampering.
- URL: https://docs.docker.com/engine/security/trust/
Patch Management:
- GCP OS Patch Management
- Description: A fully managed service by Google Cloud for patching OS vulnerabilities across your environment.
- Features: Automated patching, integration with Google Cloud OS, compliance tracking.
- Benefits: Reduces downtime and risk by keeping systems updated with the latest patches.
- URL: https://cloud.google.com/compute/docs/os-patch-management - Azure Security Center
- Description: A unified security management system for monitoring and securing Azure resources.
- Features: Security recommendations, automated patching, compliance management.
- Benefits: Protects against threats with continuous monitoring and security alerts.
- URL: https://azure.microsoft.com/en-us/services/security-center/ - AWS Systems Manager
- Description: A service that enables automatic patching and management of resources across AWS infrastructure.
- Features: Automation, patch baseline management, compliance tracking.
- Benefits: Simplifies patch management for AWS resources, ensures compliance, and reduces vulnerabilities.
- URL: https://aws.amazon.com/systems-manager/
Firewall:
- GCP Firewall Rules
- Description: A managed firewall service for securing GCP-based resources and controlling network traffic.
- Features: Customizable rules, support for ingress/egress traffic filtering, logging.
- Benefits: Secures cloud networks and controls traffic to/from resources.
- URL: https://cloud.google.com/vpc/docs/firewalls - Azure NSGs (Network Security Groups)
- Description: A tool that allows you to filter traffic to and from Azure resources based on rules.
- Features: Inbound and outbound filtering, easy rule configuration, integration with other Azure services.
- Benefits: Enhances network security by controlling traffic flow and access.
- URL: https://docs.microsoft.com/en-us/azure/virtual-network/network-security-groups - MS Defender
- Description: A comprehensive security solution for managing network protection, including firewalls.
- Features: Multi-layered protection, real-time threat monitoring, integrated firewall controls.
- Benefits: Provides centralized security management for Microsoft environments.
- URL: https://www.microsoft.com/en-us/security/business/defender - AWS Security Groups
- Description: A firewall that controls inbound and outbound traffic for AWS resources.
- Features: Stateless traffic filtering, customizable rules, multiple levels of access control.
- Benefits: Simplifies network access management for AWS resources and enhances security.
- URL: https://aws.amazon.com/security-groups/
Intrusion Detection and Prevention Systems (IDS/IPS:
- GCP IDS (Intrusion Detection System)
- Description: Google's cloud-based solution for detecting and responding to network security threats.
- Features: Traffic monitoring, anomaly detection, integration with other Google Cloud security services.
- Benefits: Provides continuous network monitoring and real-time threat alerts, improving response times to security incidents.
- URL: https://cloud.google.com/security/ - Azure Security Center
- Description: A unified security platform by Microsoft for detecting and mitigating threats across Azure environments.
- Features: Threat detection, security alerts, real-time monitoring.
- Benefits: Streamlines threat identification and mitigation within Azure, reduces the potential impact of cyber-attacks.
- URL: https://azure.microsoft.com/en-us/services/security-center/ - Amazon GuardDuty
- Description: An intelligent threat detection service that monitors AWS accounts and workloads for malicious activity.
- Features: Continuous monitoring, machine learning-based anomaly detection, integration with AWS services.
- Benefits: Protects AWS environments by detecting and alerting on potential security threats in real-time.
- URL: https://aws.amazon.com/guardduty/ - CrowdStrike
- Description: A cloud-delivered endpoint protection solution that provides real-time threat intelligence and detection.
- Features: Endpoint detection and response (EDR), managed threat hunting, behavioral analysis.
- Benefits: Helps businesses detect, prevent, and respond to security breaches quickly and effectively.
- URL: https://www.crowdstrike.com/
Privileged Access Management (PAM):
- CyberArk
- Description: A leader in privileged access security, providing comprehensive solutions for securing and monitoring privileged accounts.
- Features: Privileged session management, credential vaulting, monitoring and auditing of privileged access.
- Benefits: Reduces the risk of insider threats and external breaches by controlling and monitoring privileged access.
- URL: https://www.cyberark.com/ - BeyondTrust
- Description: A unified platform for securing privileged accounts, remote access, and endpoint protection.
- Features: Password vaulting, session recording, real-time monitoring, and alerting.
- Benefits: Secures and manages privileged access, reduces attack surface, and improves compliance.
- URL: https://www.beyondtrust.com/
Endpoint Detection and Response (EDR):
- CrowdStrike
- Description: An advanced endpoint detection and response solution that provides visibility and response capabilities for enterprise endpoints.
- Features: Real-time monitoring, incident response, threat intelligence.
- Benefits: Improves endpoint security by detecting and responding to threats faster and more efficiently.
- URL: https://www.crowdstrike.com/ - Carbon Black
- Description: An endpoint security solution that leverages behavioral analytics to detect and stop cyber threats.
- Features: Real-time monitoring, incident response, threat hunting, cloud-delivered.
- Benefits: Provides proactive protection against both known and unknown threats across enterprise endpoints.
- URL: https://www.vmware.com/products/carbon-black.html
File Integrity Monitoring (FIM):
- CloudPassage Halo
- Description: A security platform that offers continuous monitoring of server configurations and file integrity in real-time.
- Features: Automated compliance reporting, FIM, vulnerability scanning, policy enforcement.
- Benefits: Enhances security posture by continuously monitoring system changes and ensuring compliance.
- URL: https://www.cloudpassage.com/ - Qualys
- Description: A cloud-based solution that includes file integrity monitoring as part of its comprehensive security and compliance tools.
- Features: Continuous monitoring, real-time alerts, asset discovery, vulnerability management.
- Benefits: Provides deep visibility into file changes and configurations, helping ensure compliance and security.
- URL: https://www.qualys.com/ - Tripwire
- Description: A solution for file integrity monitoring, system monitoring, and change auditing across enterprise IT environments.
- Features: Real-time FIM, audit logs, compliance reporting.
- Benefits: Helps ensure system integrity and compliance by monitoring for unauthorized changes.
- URL: https://www.tripwire.com/ - OSSEC
- Description: An open-source Host-based Intrusion Detection System (HIDS) that provides file integrity checking, rootkit detection, and log analysis.
- Features: File integrity monitoring, rootkit detection, real-time alerts, log analysis.
- Benefits: Provides robust protection and monitoring for critical systems and file integrity.
- URL: https://www.ossec.net/
Antivirus:
- CrowdStrike (VM)
- Description: An endpoint protection solution that prevents, detects, and responds to advanced threats using a combination of cloud-based and on-premises tools.
- Features: Real-time threat intelligence, advanced malware detection, EDR capabilities.
- Benefits: Provides advanced malware protection and threat detection in a fully integrated platform.
- URL: https://www.crowdstrike.com/ - Carbon Black
- Description: An endpoint protection solution from VMware that focuses on preventing, detecting, and responding to security incidents in real time.
- Features: Behavioral analytics, continuous monitoring, real-time response capabilities.
- Benefits: Stops malware and advanced persistent threats while enhancing overall endpoint security.
- URL: https://www.vmware.com/products/carbon-black.html - McAfee
- Description: A leading antivirus solution that offers comprehensive protection against malware, ransomware, and other security threats.
- Features: Real-time threat protection, firewall, web security, advanced malware detection.
- Benefits: Provides comprehensive protection for endpoints against a wide range of threats.
- URL: https://www.mcafee.com/ - ClamAV
- Description: An open-source antivirus engine used for detecting malicious software.
- Features: Virus scanning, integration with other systems, real-time alerts.
- Benefits: Cost-effective antivirus solution for scanning and identifying malicious software.
- URL: https://www.clamav.net/
Vulnerability Scanning:
- Rapid7 Nexpose
- Description: A vulnerability management solution that provides real-time vulnerability scanning and reporting.
- Features: Automated vulnerability scans, remediation suggestions, risk-based assessments.
- Benefits: Reduces risks by identifying and addressing vulnerabilities across systems and applications.
- URL: https://www.rapid7.com/products/nexpose/ - Tenable Nessus
- Description: A vulnerability scanner that provides insights into potential security risks and vulnerabilities across your network.
- Features: Network scanning, plugin support, risk assessment, reporting.
- Benefits: Identifies vulnerabilities early and helps mitigate risks before exploitation occurs.
- URL: https://www.tenable.com/products/nessus
Penetration Testing:
- CoreImpact
- Description: A comprehensive penetration testing tool that automates vulnerability assessments and simulates attacks to assess an organization’s security posture.
- Features: Automated exploit testing, integration with other security tools, detailed reporting.
- Benefits: Identifies security gaps and vulnerabilities by simulating real-world attacks in a controlled environment.
- URL: https://www.coresecurity.com/core-impact - Kali Linux
- Description: A Linux distribution packed with security tools for penetration testing, vulnerability analysis, and ethical hacking.
- Features: Over 600 tools for penetration testing, security auditing, and forensics.
- Benefits: Provides a robust environment for testing security flaws and vulnerabilities.
- URL: https://www.kali.org/
Application security is a crucial pillar of a Holistic Cloud Security Defense-In-Depth Strategy, protecting applications from cyber threats, fraud, and vulnerabilities throughout their lifecycle. Secure coding practices, and runtime protections to prevent attacks like SQL injection and cross-site scripting (XSS) among others in OWASP Top 10. A combination of Static Application Security Testing (SAST), Dynamic Application Security Testing (DAST), and Interactive Application Security Testing (IAST) is used to detect vulnerabilities in source code, runtime behavior, and real-time execution. Software Composition Analysis (SCA) helps identify security risks in open-source dependencies, while vulnerability assessments and penetration testing provide continuous evaluation of security posture by simulating real-world attacks. Real-time application threat and fraud detection uses AI-driven monitoring and behavioral analytics to identify malicious activities and anomalies. Web application security leverages Web Application Firewalls (WAF). API security enforces strong authentication, rate limiting, and encryption to safeguard data exchanges. Authentication and authorization (Authn. & Authz.) ensure users and services are properly identified and granted least-privilege access, often reinforced by multi-factor authentication (MFA) for additional security. Security design and architecture reviews assess application blueprints for potential risks, while security code reviews and threat modeling proactively identify and mitigate weaknesses in the development phase. Encryption in transit protects data flows between applications, users, and APIs using protocols like TLS. Code signing ensures software integrity by verifying authenticity and preventing tampering. By integrating these security measures, organizations strengthen application defenses, prevent unauthorized access, and ensure resilience against evolving cyber threats in cloud environments.
Static Application Security Testing (SAST):
- Coverity
- Description: A static code analysis tool that detects security vulnerabilities and coding defects early in development.
- Features: Deep static analysis, CI/CD integration, multi-language support, compliance tracking.
- Benefits: Improves code quality, reduces security risks, automates vulnerability detection.
- URL: https://www.synopsys.com/software-integrity/security-testing/static-analysis.html - Arnica
- Description: A modern security platform designed for automated SAST with real-time risk analysis.
- Features: AI-driven static analysis, developer-friendly security insights, CI/CD integration.
- Benefits: Reduces false positives, enhances DevSecOps workflows, accelerates secure coding.
- URL: https://www.arnica.io/ - SonarQube
- Description: An open-source static code analysis tool that identifies vulnerabilities, bugs, and code smells in applications.
- Features: Supports multiple languages, integrates with DevOps pipelines, automated security reviews, compliance tracking.
- Benefits: Enhances code quality, automates security checks, ensures compliance with coding standards.
- URL: https://www.sonarqube.org/ - GitLeaks
- Description: A lightweight SAST tool for detecting hardcoded secrets and credentials in repositories.
- Features: Scans Git repositories, detects API keys, tokens, and passwords.
- Benefits: Prevents data breaches, secures source code repositories, integrates with DevSecOps pipelines.
- URL: https://github.com/gitleaks/gitleaks
Dynamic Application Security Testing (DAST):
- Burp Suite
- Description: A powerful web security testing tool used for dynamic vulnerability scanning and penetration testing.
- Features: Automated and manual testing, web vulnerability scanning, API security testing, extensible with plugins.
- Benefits: Identifies security flaws in running applications, supports ethical hacking and security research.
- URL: https://portswigger.net/burp - Sec-Sci AutoPT
- Description: An automated penetration testing tool designed for large-scale web and network security assessments.
- Features: AI-driven scanning, exploit simulation, automated report generation.
- Benefits: Reduces manual effort in penetration testing, provides real-time security insights.
- URL: https://www.security-science.com/sec-sci-autopt - WebInspect
- Description: A DAST tool by Micro Focus that scans web applications for security vulnerabilities.
- Features: Automated security testing, compliance assessment, API security scanning.
- Benefits: Detects OWASP Top 10 vulnerabilities, integrates with DevSecOps workflows.
- URL: https://www.microfocus.com/en-us/cyberres/application-security/webinspect - Rapid7 AppSpider
- Description: A DAST-based vulnerability scanner for web applications and APIs.
- Features: Automated scanning, OWASP Top 10 coverage, integration with DevSecOps pipelines.
- Benefits: Identifies security flaws before deployment, streamlines compliance audits.
- URL: https://www.rapid7.com/products/appspider/
Interactive Application Security Testing (IAST):
- Seeker
- Description: A real-time security analysis tool that monitors application behavior during runtime.
- Features: Runtime code analysis, API vulnerability detection, CI/CD integration.
- Benefits: Identifies real-world vulnerabilities with minimal false positives.
- URL: https://www.synopsys.com/software-integrity/security-testing/interactive-analysis.html
Software Composition Analysis (SCA):
- Mend
- Description: An SCA tool for identifying security risks in open-source dependencies.
- Features: Automated vulnerability tracking, license compliance checks, real-time security alerts.
- Benefits: Prevents supply chain attacks, ensures compliance.
- URL: https://www.mend.io/ - Arnica
- See above.
Vulnerability Assessment:
- Contrast Security
- Description: A security platform that provides runtime application self-protection (RASP) and continuous vulnerability assessment.
- Features: Real-time application monitoring, API security testing, risk-based prioritization.
- Benefits: Reduces false positives, integrates into DevSecOps workflows.
- URL: https://www.contrastsecurity.com/ - Rapid7 AppSpider
- See above.
Penetration Testing:
- Burp Suite
- See above. - Core Impact
- Description: An advanced penetration testing framework for simulating real-world cyberattacks.
- Features: Automated and manual testing, exploit library, network and web security assessments.
- Benefits: Simulates multi-stage attacks, reduces penetration testing complexity.
- URL: https://www.coresecurity.com/products/core-impact - Sec-Sci AutoPT
- See above. - Kali Linux
- Description: A Linux distribution packed with penetration testing and security auditing tools.
- Features: Over 600 security tools, customizable environment, frequent updates.
- Benefits: Industry-standard for ethical hacking, supports multiple penetration testing methodologies.
- URL: https://www.kali.org/
Web Application Security:
- GCP Cloud Armor
- Description: A web application firewall (WAF) from Google Cloud that provides security for web apps.
- Features: Protection against DDoS, bot attacks, and other web application threats, integration with Google Cloud services.
- Benefits: Scalable protection with real-time threat analysis and easy integration into Google Cloud.
- URL: https://cloud.google.com/security/cloud-armor - Azure App Gateway
- Description: A web traffic load balancer and WAF from Microsoft Azure for securing web applications.
- Features: SSL termination, URL-based routing, web application firewall, DDoS protection.
- Benefits: Provides scalable web traffic management and security for web applications on Azure.
- URL: https://azure.microsoft.com/en-us/services/application-gateway/ - AWS WAF
- Description: A web application firewall from AWS for protecting applications from common web exploits.
- Features: Customizable rules, protection from SQL injection, XSS attacks, and DDoS mitigation.
- Benefits: Simple and scalable protection for web applications hosted on AWS.
- URL: https://aws.amazon.com/waf/ - CloudFlare
- Description: A cloud-based WAF that offers protection for websites and web applications.
- Features: DDoS protection, SSL support, bot management, performance optimization, and traffic filtering.
- Benefits: Improves security and performance for websites and web apps.
- URL: https://www.cloudflare.com
API Security:
- Apigee Sense
- Description: An API security solution from Google Cloud for detecting and mitigating API threats.
- Features: Machine learning-powered threat detection, API traffic monitoring, and anomaly detection.
- Benefits: Real-time threat detection and prevention for APIs, improving API security.
- URL: https://cloud.google.com/apigee/sense - GCP Cloud Armor
- Description: Also used for API security, protecting against DDoS and other threats targeting APIs.
- Features: IP-based filtering, application firewall, and WAF for APIs.
- Benefits: Scalable and integrated API protection for Google Cloud-hosted applications.
- URL: https://cloud.google.com/security/cloud-armor - Azure App Gateway
- Description: Offers API security through its web application firewall, providing comprehensive traffic management.
- Features: URL-based routing, WAF protection for APIs, and SSL termination.
- Benefits: Efficient security management for APIs and web apps on Azure.
- URL: https://azure.microsoft.com/en-us/services/application-gateway/ - CloudFlare
- Description: Provides API protection through its WAF and traffic filtering tools.
- Features: Bot detection, DDoS mitigation, and SSL support for APIs.
- Benefits: Ensures API security, preventing abuse and improving API availability.
- URL: https://www.cloudflare.com
Authentication & Authorization:
- Okta
- Description: A cloud-based identity and access management solution for securing authentication and authorization.
- Features: Single sign-on (SSO), multi-factor authentication, and user lifecycle management.
- Benefits: Simplifies access management with strong security and integration capabilities.
- URL: https://www.okta.com - OpenAM
- Description: An open-source access management platform providing authentication and authorization services.
- Features: Single sign-on, identity federation, access control policies, and multi-factor authentication.
- Benefits: Flexible, scalable solution for managing access across multiple applications.
- URL: https://www.forgerock.com/platform/access-management
Multi-Factor Authentication (MFA):
- Auth0
- Description: A flexible authentication and authorization platform with robust MFA options.
- Features: Multi-factor authentication, single sign-on, and customizable security policies.
- Benefits: Enhances security with strong authentication and seamless user experience.
- URL: https://auth0.com - Firebase Authentication
- Description: Google’s authentication service providing easy-to-integrate MFA and identity management.
- Features: Email/password authentication, social login, and multi-factor authentication.
- Benefits: Simple and scalable solution for authentication and MFA for mobile and web apps.
- URL: https://firebase.google.com/products/auth - Amazon Cognito
- Description: A service from AWS that provides authentication, authorization, and user management with MFA support.
- Features: User pools, federated identities, multi-factor authentication, and integration with AWS services.
- Benefits: Easy-to-implement solution for securing user access and implementing MFA.
- URL: https://aws.amazon.com/cognito/ - Microsoft Authenticator
- Description: A Microsoft app for multi-factor authentication and passwordless login.
- Features: Push notifications for MFA, secure sign-ins, and integration with Microsoft accounts.
- Benefits: Simple, secure MFA solution, especially for users within the Microsoft ecosystem.
- URL: https://www.microsoft.com/en-us/security/mobile-authenticator - Google Authenticator
- Description: A mobile app for generating time-based one-time passwords (TOTP) for MFA.
- Features: Supports TOTP for secure login, can be used with Google and third-party services.
- Benefits: Easy-to-use, secure MFA solution that enhances login security.
- URL: https://www.google.com/Authenticator
Code Signing:
- SignTool (Microsoft)
- Description: A Microsoft tool for signing code, ensuring its integrity and authenticity.
- Features: Sign executables, DLLs, and other code, and verify signatures.
- Benefits: Ensures code authenticity and protects against tampering.
- URL: https://learn.microsoft.com/en-us/dotnet/framework/tools/signtool - Jarsigner (Java)
- Description: A tool for signing Java Archive (JAR) files.
- Features: Sign and verify JAR files, including applets and packages.
- Benefits: Provides authenticity and integrity for Java applications.
- URL: https://docs.oracle.com/javase/8/docs/technotes/tools/unix/jarsigner.html - MacOS CodeSign (Apple)
- Description: Apple’s tool for signing macOS apps and software.
- Features: Code signing, provisioning profiles, and securing apps for distribution.
- Benefits: Ensures app security and integrity for macOS software.
- URL: https://developer.apple.com/documentation/security/codesigning - Azure Code Signing
- Description: A Microsoft solution for signing code, providing authenticity and ensuring integrity.
- Features: Automated code signing, secure certificate management.
- Benefits: Simplifies code signing for applications in the Azure ecosystem.
- URL: https://learn.microsoft.com/en-us/azure/security/fundamentals/code-signing - SignPath
- Description: A digital signing platform that enables secure code signing and document signing.
- Features: Secure signing workflow, cloud-based platform, auditing.
- Benefits: Simplifies code and document signing processes with security and compliance.
- URL: https://www.signpath.io
Real-Time App Threat & Fraud Detection:
- Darktrace
- Description: AI-driven cybersecurity platform for detecting and responding to threats in real time.
- Features: Machine learning for threat detection, anomaly detection, and automated response.
- Benefits: Real-time detection and adaptive response to protect apps and networks.
- URL: https://www.darktrace.com - Shape Security (F5)
- Description: A fraud prevention solution using AI to detect and mitigate threats in real-time.
- Features: Bot detection, fraud prevention, and account takeover protection.
- Benefits: Protects against fraud and account compromise with AI-powered security.
- URL: https://www.f5.com/products/shape-security - ThreatMetrix
- Description: A fraud detection solution using real-time analytics to protect apps.
- Features: Device intelligence, real-time transaction monitoring, and fraud risk scoring.
- Benefits: Detects fraud patterns and protects against account takeover and identity theft.
- URL: https://www.threatmetrix.com
Application Security Architecture Review:
- OWASP ASVS
- Description: A framework for testing web application security across various levels.
- Features: Security verification standard for web applications.
- Benefits: Provides a baseline for application security architecture and testing.
- URL: https://owasp.org/www-project-application-security-verification-standard/ - OWASP SAMM
- Description: A self-assessment security model for software development.
- Features: Framework for improving software security maturity.
- Benefits: Helps organizations assess and improve their secure software development processes.
- URL: https://owasp.org/www-project-software-assurance-maturity-model/
Threat Modeling:
- MS Threat Modeling Tool
- Description: A Microsoft tool that helps developers identify and mitigate security risks in their applications.
- Features: Diagramming and risk analysis for threat modeling.
- Benefits: Helps integrate threat modeling into the development lifecycle.
- URL: https://learn.microsoft.com/en-us/security/threat-modeling - IriusRisk
- Description: A threat modeling platform for identifying security threats early in development.
- Features: Automated threat identification, integrates with DevSecOps tools.
- Benefits: Streamlines the threat modeling process and integrates security into DevOps.
- URL: https://www.iriusrisk.com - OWASP Threat Dragon
- Description: An open-source threat modeling tool from OWASP.
- Features: Web-based, easy-to-use for creating threat models, integrated with other tools.
- Benefits: Free and easy integration with OWASP’s threat modeling practices.
- URL: https://owasp.org/www-project-threat-dragon/ - ThreatModeler
- Description: A platform for automated threat modeling for secure software development.
- Features: Model creation, risk identification, and visualization of security threats.
- Benefits: Simplifies threat modeling and risk management processes.
- URL: https://www.threatmodeler.com
Encryption In Transit:
- m(TLS)
- Description: Transport Layer Security (TLS) for securing communication between systems.
- Features: Encryption, integrity checking, and authentication.
- Benefits: Ensures secure communication and data integrity during transmission.
- URL: https://www.ietf.org/rfc/rfc5246.txt - TLS 1.2+
- Description: An encryption protocol for secure communications over networks.
- Features: Stronger encryption, improved security, and backward compatibility.
- Benefits: Provides strong protection against data breaches and eavesdropping.
- URL: https://tools.ietf.org/html/rfc5246
Data security is a fundamental aspect of a Holistic Cloud Security Defense-In-Depth Strategy, ensuring sensitive information remains protected throughout its lifecycle. Data classification categorizes information based on sensitivity, enabling appropriate security controls. Data lifecycle management (DLM) governs data from creation to disposal, enforcing retention and access policies. Data privacy assessments evaluate compliance with regulations like GDPR, CCPA, and HIPAA, identifying risks in data handling. Encryption at rest secures stored data using cryptographic techniques such as AES-256 to prevent unauthorized access. De-identification removes personal identifiers to protect sensitive information while maintaining usability, while data masking conceals real data in non-production environments to prevent exposure. Together, these measures enhance data confidentiality, integrity, and compliance in cloud environments.
Encryption at Rest:
- Google Cloud Key Management Service (GCP KMS)
- Description: GCP KMS is a cloud-based encryption key management service that allows organizations to create, use, and manage cryptographic keys for securing data at rest.
- Features: Centralized key management, automatic key rotation, integration with Google Cloud services, Cloud HSM support, IAM-based access control.
- Benefits: Simplifies encryption, ensures compliance with security standards, integrates seamlessly with Google Cloud services.
- URL: https://cloud.google.com/kms - AWS Key Management Service (AWS KMS)
- Description: AWS KMS is a fully managed service that enables organizations to create and control cryptographic keys used for encrypting data across AWS services and applications.
- Features: FIPS 140-2 validated HSMs, key rotation, fine-grained access controls, automatic encryption integration with AWS storage and databases.
- Benefits: Enhances security and compliance, reduces key management complexity, integrates seamlessly with AWS services.
- URL: https://aws.amazon.com/kms/ - Azure Key Vault
- Description: Azure Key Vault is a cloud service for managing and safeguarding cryptographic keys, secrets, and certificates used for encryption in Microsoft Azure environments.
- Features: Secure key storage, access policies, hardware security module (HSM) support, integration with Azure services, automated key rotation.
- Benefits: Strengthens security posture, reduces key management complexity, provides centralized control over encryption keys and secrets.
- URL: https://azure.microsoft.com/en-us/products/key-vault/
Data Privacy Assessment:
- OneTrust
- Description: OneTrust is a privacy, security, and data governance platform that helps organizations assess and manage compliance with global data protection regulations.
- Features: Automated privacy impact assessments (PIA/DPIA), data mapping, consent management, risk assessments, compliance reporting.
- Benefits: Streamlines compliance with GDPR, CCPA, and other regulations, automates risk assessments, enhances transparency in data processing.
- URL: https://www.onetrust.com/ - TrustArc
- Description: TrustArc is a privacy management and compliance platform that provides tools for data governance, risk assessment, and regulatory compliance tracking.
- Features: Privacy impact assessments, automated data flow mapping, risk assessment frameworks, compliance monitoring, AI-powered insights.
- Benefits: Simplifies compliance with global privacy regulations, automates risk identification, improves data governance and security.
- URL: https://www.trustarc.com/
Network, Endpoint, Application, and Data (NEAD) security is an integral part of a Holistic Cloud Security Defense-in-Depth Strategy, ensuring robust protection across all layers of a cloud environment. Cloud Security Posture Management (CSPM) continuously assesses configurations to detect misconfigurations and compliance gaps, while adherence to compliance standards like ISO 27001, NIST, CCPA, GDPR, and HIPAA ensures regulatory alignment. Security is embedded into the Secure Development Lifecycle (SDLC) through threat modeling, code analysis, and automated security testing. Certificate and Secrets Lifecycle Management safeguard digital certificates, API keys, and credentials through secure storage, rotation, and automated renewal. Identity & Access Management (IAM) enforces least privilege access and multi-factor authentication (MFA) to control user and system access. Vulnerability and Risk Management involve continuous scanning, risk assessments, and remediation strategies to minimize security threats. Auditing, Logging & Monitoring, along with Security Information & Event Management (SIEM), provide real-time visibility, anomaly detection, and incident response capabilities. In case of security incidents, Digital Forensics enables detailed investigation and evidence collection, while Encryption Key Lifecycle Management ensures the secure handling of encryption keys to protect sensitive data. By integrating these security measures, organizations can establish a resilient cloud security framework that protects critical assets, ensures compliance, and strengthens overall security posture.
Cloud Security Posture Management (CSPM):
- GCP Security Command Center
- Description: Google Cloud's CSPM solution that helps identify security risks and compliance violations.
- Features: Threat detection, misconfiguration analysis, asset discovery, and security posture monitoring.
- Benefits: Provides centralized security visibility and automated risk assessment for Google Cloud environments.
- URL: https://cloud.google.com/security-command-center - Wiz
- Description: A cloud security platform that provides full-stack visibility and risk assessment across cloud environments.
- Features: Agentless scanning, workload security, identity risk detection, and compliance monitoring.
- Benefits: Offers real-time cloud security insights, prioritizes risks, and automates security response.
- URL: https://www.wiz.io - Orca Security
- Description: A cloud-native security platform that provides deep insights into security risks without deploying agents.
- Features: Agentless scanning, cloud vulnerability management, identity risk assessment, and compliance checks.
- Benefits: Provides continuous visibility and proactive threat detection for multi-cloud environments.
- URL: https://orca.security
Security Information and Event Management (SIEM):
- Google Chronicle
- Description: A cloud-native SIEM that provides advanced threat detection and log analysis.
- Features: High-speed log ingestion, real-time threat detection, integration with Google security tools.
- Benefits: Scalable, cost-effective SIEM with fast search capabilities and AI-driven threat intelligence.
- URL: https://cloud.google.com/chronicle - Azure Sentinel
- Description: A cloud-native SIEM and SOAR solution from Microsoft.
- Features: AI-powered threat detection, automated incident response, integration with Microsoft security tools.
- Benefits: Reduces investigation time, provides advanced analytics, and scales across hybrid environments.
- URL: https://azure.microsoft.com/en-us/products/microsoft-sentinel - Splunk
- Description: A powerful SIEM platform for security monitoring and event correlation.
- Features: Log analysis, real-time threat detection, machine learning-based insights, customizable dashboards.
- Benefits: Provides deep security analytics, fast threat response, and broad third-party integrations.
- URL: https://www.splunk.com/en_us/solutions/siem.html
Information Security Risk Assessment:
- OneTrust
- Description: A platform for risk management, privacy compliance, and security assessments.
- Features: Risk assessment automation, regulatory compliance tools, data protection monitoring.
- Benefits: Streamlines security risk assessments and enhances compliance with regulatory requirements.
- URL: https://www.onetrust.com - LogicGate Risk Cloud
- Description: A no-code risk management platform that helps organizations assess and mitigate security risks.
- Features: Automated workflows, compliance tracking, risk assessment templates.
- Benefits: Reduces risk exposure with automated risk assessments and integrated compliance management.
- URL: https://www.logicgate.com
Governance, Risk, and Compliance (GRC):
- RSA Archer
- Description: A GRC platform that helps organizations manage risk, compliance, and business continuity.
- Features: Risk and compliance automation, third-party risk management, audit tracking.
- Benefits: Centralized risk visibility, improved compliance, and automated risk assessments.
- URL: https://www.archerirm.com - MetricStream
- Description: A cloud-based GRC solution for enterprise risk and compliance management.
- Features: Risk assessment, policy management, audit tracking, and AI-driven insights.
- Benefits: Provides a unified platform for managing risk, compliance, and governance.
- URL: https://www.metricstream.com - IBM OpenPages
- Description: An AI-powered GRC platform that integrates risk management with business processes.
- Features: Risk modeling, compliance management, AI-driven insights, third-party risk monitoring.
- Benefits: Enhances enterprise risk visibility and automates compliance workflows.
- URL: https://www.ibm.com/products/openpages-governance-risk-compliance - ServiceNow GRC
- Description: A cloud-based governance, risk, and compliance management solution.
- Features: Risk quantification, policy automation, real-time compliance monitoring.
- Benefits: Streamlines risk management processes and integrates security operations.
- URL: https://www.servicenow.com/products/governance-risk-and-compliance.html - Riskonnect
- Description: A risk management platform that combines GRC, compliance, and operational risk insights.
- Features: Risk assessment, compliance automation, third-party risk management.
- Benefits: Provides real-time risk intelligence and automates compliance tracking.
- URL: https://www.riskonnect.com
Information security general guidelines establish fundamental principles and best practices to protect sensitive data, systems, and networks from threats. Within the Holistic Cloud Security Defense-in-Depth Strategy, these guidelines ensure multi-layered protection across cloud environments. Key areas include access control, enforcing least privilege and multi-factor authentication (MFA); data protection, using encryption, secure storage, and lifecycle management for secrets and certificates; risk management, identifying and mitigating security threats; and incident response, defining structured procedures for threat detection, response, and recovery. Additionally, this strategy emphasizes compliance with industry regulations (e.g., ISO 27001, NIST, GDPR, CCPA, HIPAA), security awareness training to foster a security-first culture, and continuous monitoring, auditing, and logging for proactive threat detection. By implementing these guidelines, organizations can strengthen cloud security posture, ensure regulatory compliance, and enhance overall resilience against cyber threats.
Comparing Key Security Frameworks
NIST Cybersecurity Framework (CSF), ISO/IEC 27001, and COBIT for Information Security are three prominent security frameworks used to establish comprehensive information security programs. Each framework has distinct features and approaches but shares common goals of improving security posture and managing risks effectively.
NIST Cybersecurity Framework (CSF)
NIST CSF provides a policy framework of computer security guidance for how private sector organizations in the U.S. can assess and improve their ability to prevent, detect, and respond to cyberattacks.
Key Components:
- Five Functions: Identify, Protect, Detect, Respond, Recover.
- Core: Provides a set of activities to achieve specific cybersecurity outcomes, and references examples of guidance to achieve those outcomes.
- Implementation Tiers: Describe the degree to which an organization's cybersecurity risk management practices exhibit the characteristics defined in the framework.
- Profiles: Align organizational requirements and objectives, risk appetite, and resources against the desired outcomes of the Framework Core.
Application:
- Risk Assessment: Helps identify and prioritize cybersecurity risks.
- Control Implementation: Provides specific actions to improve cybersecurity posture.
- Performance Monitoring: Regularly assesses and adjusts the cybersecurity program as needed.
ISO/IEC 27001
ISO/IEC 27001 is an international standard for managing information security. It provides a systematic approach to managing sensitive company information so that it remains secure.
Key Components:
- ISMS (Information Security Management System): A systematic approach to managing sensitive information, encompassing people, processes, and IT systems.
- Annex A Controls: 114 controls covering various aspects of information security, such as physical security, access control, and incident management.
- PDCA Model: Plan-Do-Check-Act cycle to ensure continuous improvement.
- Risk Assessment: Requires a structured risk assessment process to identify, analyze, and manage risks.
- Control Implementation: Specifies controls based on identified risks and legal, regulatory, and contractual requirements.
- Performance Monitoring: Continuous monitoring and reviewing of the ISMS to ensure its effectiveness and make necessary improvements.
COBIT (Control Objectives for Information and Related Technologies) provides a comprehensive framework for the management and governance of enterprise IT.
Key Components:
- Processes: Defines IT processes and control objectives.
- Governance and Management: Distinguishes between governance (setting direction and monitoring) and management (planning, building, running, and monitoring).
- Maturity Models: Provides maturity models to assess the level of IT management capabilities.
- Risk Assessment: Integrates with enterprise risk management to identify IT-related risks.
- Control Implementation: Offers detailed control objectives and practices to mitigate identified risks.
- Performance Monitoring: Uses performance metrics and maturity models to monitor and improve IT governance and management practices.
Establishing a Comprehensive Information Security Program
By leveraging the following frameworks, organizations can establish a robust information security program that encompasses risk assessment, control implementation, and performance monitoring.
Risk Assessment
- NIST CSE: Use the Identify function to catalog assets, identity vulnerabilities, and evaluate the risk to critical infrastructure.
- ISO/EC 27001: Conduct a formal risk assessment to identify risks to information assets and determine their impact.
- COBIT: Integrate IT risk assessment into the overall enterprise risk management process, ensuring alignment with business objectives.
Control Implementation
- NIST CSF: Implement controls across the Protect, Detect, Respond, and Recover functions based on prioritized risks.
- ISO/EC 27001: Select controls from Annex A based on the risk assessment and ensure they are documented in the Statement of Applicability.
- COBIT: Apply control objectives and practices to address identified risks, ensuring proper governance and management of IT processes
Performance Monitoring
- NIST CSF: Regularly review and update the framework profile and implementation tiers to reflect changes in the cybersecurity landscape.
- ISO/IEC 27001: Monitor and measure the performance of the ISMS, conduct regular internal audits, and perform management reviews to ensure continuous improvement.
- COBIT: Use performance metrics and maturity models to assess the effectiveness of IT governance and management practices, making improvements as necessary.
By combining elements from NIST CSF, ISO/IEC 27001, and COBIT, organizations can create a comprehensive information security program that is not only mitigates risks but also aligns with business objectives and regulatory requirements. This integrated approach ensures a balanced and effective security posture, capable of adapting to evolving threats and challenges.
Key Principles of Privacy Protection
Data Minimization
Data minimization involves collecting only the data necessary for a specific purpose and no more.
Importance:
- Risk Reduction: Limits exposure to data breaches by reducing the amount of sensitive data stored.
- Compliance: Ensures adherence to privacy regulations requiring minimal data collection.
Example: An e-commerce site collects only essential customer information such as name, address, and payment details, avoiding unnecessary data like social security numbers.
Purpose Limitation
Purpose limitation requires that data be collected for specific, explicit, and legitimate purposes and not further processed in a manner incompatible with those purposes.
Importance:
- Transparency: Builds trust by clearly defining and communicating the purposes for data collection.
- Compliance: Ensures data is used in line with the expectations set during collection.
Example: A healthcare provider collects patient information solely for medical treatment and does not use it for marketing purposes without explicit consent.
Storage Limitation
Storage limitation mandates that personal data should be kept in a form which permits identification of data subjects for no longer than necessary for the purposes for which the data is processed.
Importance:
- Security: Reduces the risk of data breaches by minimizing the time data is held.
- Compliance: Aligns with regulatory requirements to delete data after it is no longer needed.
Example: A recruitment firm deletes candidates' personal information after six months if the individuals are not hired, aligning with job application retention policies.
Data Subject Rights
Data subject rights are the rights granted to individuals over their personal data, including access, rectification, erasure, restriction of processing, and data portability.
Importance:
- Empowerment: Gives individuals control over their personal information.
- Trust: Enhances transparency and trust between organizations and individuals.
Example: A social media platform allows users to download their data, correct inaccuracies, and delete their accounts, thereby exercising their data subject rights.
Regulations Enforcing Privacy Principles
General Data Protection Regulation (GDPR)
The GDPR is a comprehensive data protection regulation in the European Union (EU) that enforces strict guidelines on data collection, processing, and storage.
Key Provisions:
- Data Minimization: Requires organizations to collect only the data necessary for specified purposes.
- Purpose Limitation: Ensures data is used only for the purposes stated at the time of collection.
- Storage Limitation: Mandates that personal data be retained only as long as necessary for the purposes for which it was collected.
- Data Subject Rights: Grants individuals rights such as access, rectification, erasure, and data portability.
Implications for Organizations:
- Compliance Costs: Organizations must invest in processes and systems to comply with GDPR requirements.
- Penalties: Non-compliance can result in significant fines, up to €20 million or 4% of global annual turnover, whichever is higher.
- Enhanced Data Protection Practices: Organizations need to implement robust data protection measures, including privacy by design and data protection impact assessments.
California Consumer Privacy Act (CCPA)
The CCPA is a state statute intended to enhance privacy rights and consumer protection for residents of California, USA.
Key Provisions:
- Data Minimization: Encourages businesses to limit data collection to what is necessary for disclosed purposes.
- Purpose Limitation: Requires businesses to disclose the purposes for which personal information is collected and used.
- Storage Limitation: Implies data retention should align with the purposes for which it was collected, though not explicitly stated like GDPR.
- Data Subject Rights: Provides California residents with rights such as access, deletion, and opting out of the sale of their personal information.
Implications for Organizations:
- Transparency Requirements: Businesses must disclose data collection practices and the purposes of data use.
- Opt-Out Provisions: Organizations must provide a mechanism for consumers to opt out of the sale of their personal information.
- Penalties for Non-Compliance: Enforcement actions can lead to fines and penalties, emphasizing the need for compliance with CCPA requirements.
Impact on Organizational Privacy Practices
Both GDPR and CCPA have significant implications for how organizations handle personal data. Key impacts include:
- Enhanced Data Governance: Organizations must establish robust data governance frameworks to ensure compliance with data minimization, purpose limitation, and storage limitation principles.
- Increased Accountability: Businesses are held accountable for their data processing activities, requiring clear documentation, regular audits, and adherence to privacy policies.
- Data Protection Measures: Implementation of technical and organizational measures such as encryption, access controls, and data protection impact assessments to safeguard personal data.
- Consumer Rights Management: Development of processes and systems to facilitate the exercise of data subject rights, including responding to data access requests, correcting inaccuracies, and enabling data deletion.
- Global Reach and Compliance: Organizations with international operations must navigate varying privacy regulations and ensure compliance across different jurisdictions, adding complexity to data management practices.
By adhering to these privacy principles and regulations, organizations can not only avoid penalties but also build trust with their customers, demonstrating a commitment to protecting their personal data.
Key Components of an Identity and Access Management (IAM) Solution
Identity and Access Management (IAM) is a framework of policies and technologies that ensures the right individuals have the appropriate access to technology resources. An effective IAM solution includes several key components:
User Provisioning
User provisioning is the process of creating, managing, and deactivating user accounts and access rights within an organization.
Key Points:
- Automated Account Creation: Streamlines the process of setting up user accounts, reducing administrative burden.
- Access Assignment: Ensures that users are granted the appropriate access rights based on their role.
- Lifecycle Management: Manages the entire lifecycle of user accounts, from creation to deactivation.
Benefits:
- Efficiency: Reduces the time and effort required to manage user accounts.
- Security: Minimizes the risk of unauthorized access by ensuring that only authorized users have access to systems and data.
Example: When a new employee joins an organization, user provisioning systems automatically create accounts for them in various systems, assign them the appropriate access rights based on their role, and ensure they have the resources they need from day one.
Role-Based Access Control (RBAC)
Definition: RBAC is an approach to restricting system access to authorized users based on their roles within an organization.
Key Points:
- Role Definitions: Defines roles based on job functions and responsibilities.
- Access Policies: Establishes policies that specify what resources each role can access.
- Role Assignment: Associates users with one or more roles, granting them access based on their assigned roles.
Benefits:
- Simplicity: Simplifies access management by reducing the number of access rules.
- Scalability: Easily scales as the organization grows, allowing new roles to be added without significant reconfiguration.
Example: In a healthcare organization, roles might include "Doctor," "Nurse," and "Administrator," each with access to different systems and data. Doctors might have access to patient records, while administrators might have access to billing systems.
Single Sign-On (SSO)
SSO allows users to authenticate once and gain access to multiple systems without needing to log in again for each one.
Key Points:
- Unified Login: Provides a single point of authentication for multiple applications and systems.
- Session Management: Manages user sessions across different systems to maintain seamless access.
Benefits:
- User Convenience: Improves user experience by reducing the need to remember multiple passwords.
- Security: Reduces the risk of password fatigue and related security issues.
Example: An employee logs into their corporate portal once and gains access to email, HR systems, and other business applications without needing to log in separately to each one.
Access Review and Recertification
Access review and recertification involve periodically reviewing and validating users' access rights to ensure they remain appropriate.
Key Points:
- Regular Audits: Conducts regular audits of user access to verify that permissions are still valid.
- Compliance: Ensures compliance with regulatory requirements and internal policies.
- Revocation: Removes access that is no longer needed or authorized.
Benefits:
- Security: Helps identify and revoke unnecessary or outdated access rights, reducing the risk of unauthorized access.
- Compliance: Ensures that access controls comply with regulatory and policy requirements.
Example: Quarterly access reviews might involve managers reviewing the access rights of their team members to ensure they still align with their current job functions. Access rights for employees who have changed roles or left the organization are updated or revoked accordingly.
Benefits and Challenges of Implementing Multi-Factor Authentication (MFA)
Multi-Factor Authentication (MFA) adds an additional layer of security by requiring users to provide two or more verification factors to gain access to a resource.
Benefits of MFA:
- Enhanced Security: Significantly reduces the risk of unauthorized access by requiring multiple forms of verification.
- Reduced Risk of Credential Theft: Protects against common threats such as phishing and password breaches by requiring more than just a password.
- Compliance: Helps meet regulatory requirements for stronger authentication methods.
Challenges of MFA:
- User Convenience: Can be perceived as inconvenient by users, potentially leading to resistance or lower adoption rates.
- Implementation Complexity: Can be complex to implement and integrate with existing systems, especially in large or diverse IT environments.
- Cost: May involve additional costs for implementation and ongoing management, including purchasing and maintaining MFA solutions.
Common MFA Methods
- One-Time Passwords (OTP): OTPs are temporary, single-use codes generated for authentication purposes. They are typically sent to the user via SMS, email, or generated by an app.
Example: A user attempting to log into a bank account receives an OTP on their registered mobile phone, which they must enter along with their password to complete the login process. - Biometric Authentication: Biometric authentication uses unique biological characteristics, such as fingerprints, facial recognition, or iris scans, to verify identity.
Example: A smartphone uses facial recognition to unlock the device and grant access to applications, ensuring that only the authorized user can access the phone.
By implementing IAM solutions with robust components like user provisioning, RBAC, SSO, and regular access reviews, organizations can ensure secure and efficient management of user identities and access rights. Combining these solutions with MFA further enhances security, protecting against unauthorized access and ensuring compliance with security policies and regulations.
Key Techniques for Securing Networks and Endpoints
Securing networks and endpoints involves implementing a variety of strategies and tools to protect against unauthorized access, malware, and other cyber threats. Key techniques include Network Segmentation, Firewall Configuration, Intrusion Detection and Prevention Systems (IDPS), and Endpoint Detection and Response (EDR).
1. Network Segmentation
Network Segmentation involves dividing a network into smaller, isolated segments to control traffic flow and enhance security.
Benefits:
- Containment: Limits the spread of malware or breaches within the network.
- Access Control: Allows for more granular access control policies, ensuring that only authorized users can access specific segments.
- Performance: Improves network performance by reducing congestion and limiting broadcast traffic.
Example: Segmenting a corporate network into separate VLANs for finance, HR, and guest access, each with its own security policies.
2. Firewall Configuration
Firewall Configuration involves setting up firewalls to monitor and control incoming and outgoing network traffic based on predetermined security rules.
Benefits:
- Traffic Filtering: Blocks unauthorized access and potentially harmful traffic.
- Policy Enforcement: Enforces security policies to control access to network resources.
- Logging and Monitoring: Provides detailed logs and monitoring capabilities to track network activity and detect anomalies.
Example: Configuring a firewall to allow HTTP and HTTPS traffic while blocking all other traffic from the internet to an internal web server.
3. Intrusion Detection and Prevention Systems (IDPS)
Intrusion Detection and Prevention Systems (IDPS) monitor network traffic for suspicious activity and take action to prevent or mitigate threats.
Types:
- Network-based (NIDPS): Monitors network traffic for signs of malicious activity.
- Host-based (HIDPS): Monitors individual hosts for suspicious behavior.
Benefits:
- Real-time Monitoring: Provides real-time detection and response to threats.
- Threat Mitigation: Can automatically block or quarantine malicious traffic.
- Alerting and Reporting: Sends alerts and generates reports on detected threats.
Example: Deploying a network-based IDPS to monitor traffic for known attack patterns and automatically blocking malicious IP addresses.
4. Endpoint Detection and Response (EDR)
Endpoint Detection and Response (EDR) solutions focus on detecting, investigating, and responding to suspicious activities on endpoints (e.g., laptops, desktops, servers).
Benefits:
- Advanced Threat Detection: Detects sophisticated threats that traditional antivirus solutions might miss.
- Incident Response: Provides tools for investigating and responding to security incidents.
- Visibility: Offers comprehensive visibility into endpoint activities and behaviors.
Example: Using an EDR solution to detect and isolate a compromised endpoint that is exhibiting signs of a ransomware attack.
Detection Methods: Signature-Based vs. Anomaly-Based
Signature-Based Detection
Signature-Based Detection identifies threats by comparing network traffic or system activities against a database of known attack patterns (signatures).
Benefits:
- High Accuracy: Effective at detecting known threats with a high degree of accuracy.
- Low False Positives: Generates fewer false positives compared to anomaly-based methods.
Limitations:
- Limited to Known Threats: Cannot detect new or unknown threats that do not match existing signatures.
- Requires Regular Updates: Needs frequent updates to the signature database to remain effective.
Example: An antivirus program that detects malware based on a signature database of known virus patterns.
Anomaly-Based Detection
Anomaly-Based Detection identifies threats by comparing current network or system behavior against a baseline of normal activity and looking for deviations.
Benefits:
- Detects Unknown Threats: Can identify new or unknown threats based on unusual behavior.
- Adaptive: Learns and adapts to changes in normal behavior over time.
Limitations:
- Higher False Positives: More likely to generate false positives, as normal variations in behavior can be flagged as anomalies.
- Complexity: Requires more sophisticated algorithms and processing power.
Example: An IDPS that detects unusual spikes in network traffic that deviate from established patterns, potentially indicating a DDoS attack.
Importance of Data Classification
Data classification is a critical process for managing and protecting sensitive information within an organization. It involves categorizing data based on its level of sensitivity and the impact that could result from its unauthorized access, disclosure, modification, or destruction. By effectively classifying data, organizations can implement appropriate security measures to protect information, comply with regulatory requirements, and reduce risks associated with data breaches.
Key Benefits of Data Classification:
- Enhanced Security:
- Ensures that sensitive data is identified and protected according to its value and sensitivity.
- Helps in deploying appropriate security controls based on the classification level.
- Ensures that sensitive data is identified and protected according to its value and sensitivity.
- Regulatory Compliance:
- Facilitates compliance with laws and regulations that mandate specific protections for different types of data.
- Supports auditing and reporting requirements by providing a clear structure for data management.
- Facilitates compliance with laws and regulations that mandate specific protections for different types of data.
- Risk Management:
- Identifies high-risk data assets, allowing for targeted risk mitigation strategies.
- Reduces the risk of data breaches by ensuring that sensitive information is adequately protected.
- Identifies high-risk data assets, allowing for targeted risk mitigation strategies.
- Efficient Data Management:
- Streamlines data handling processes by providing clear guidelines for storing, accessing, and sharing information.
- Helps in managing data lifecycle, including retention and disposal, based on sensitivity.
- Streamlines data handling processes by providing clear guidelines for storing, accessing, and sharing information.
Common Data Classification Schemes
Data classification schemes typically include several levels, each with specific handling and protection requirements. A common scheme includes categories like Public, Internal, Confidential, and Restricted.
- Public: Public data is information that is intended for public dissemination and can be freely shared without any restrictions.
- Examples:
- Company brochures and marketing materials.
- Press releases and public announcements.
- Information on the company's public website.
- Company brochures and marketing materials.
- Handling and Protection:
- Labeling: Clearly label as "Public."
- Access Control: No special access restrictions; accessible by anyone.
- Retention: Retain according to business needs and public communication policies.
- Labeling: Clearly label as "Public."
- Examples:
- Internal: Internal data is information that is intended for use within the organization and should not be disclosed to the public.
- Examples:
- Internal memos and company policies.
- Employee directories and organizational charts.
- Internal reports and meeting minutes.
- Internal memos and company policies.
- Handling and Protection:
- Labeling: Mark as "Internal Use Only."
- Access Control: Restricted to employees and authorized personnel.
- Retention: Retain according to internal policies and operational needs.
- Labeling: Mark as "Internal Use Only."
- Examples:
- Confidential: Confidential data is sensitive information that, if disclosed, could harm the organization or its stakeholders. Access is limited to specific individuals who need the information to perform their duties.
- Examples:
- Employee personal information (e.g., social security numbers, health records).
- Financial records and strategic plans.
- Customer information and contracts.
- Employee personal information (e.g., social security numbers, health records).
- Handling and Protection:
- Labeling: Clearly mark as "Confidential."
- Access Control: Restricted to specific roles or departments; often requires authentication and authorization.
- Retention: Retain according to regulatory requirements and internal policies; securely dispose of when no longer needed.
- Labeling: Clearly mark as "Confidential."
- Examples:
- Restricted: Restricted data is highly sensitive information that requires the highest level of protection due to the significant harm that could result from its unauthorized disclosure.
- Examples:
- Intellectual property (e.g., patents, trade secrets).
- Critical infrastructure details.
- Classified information in regulated industries (e.g., healthcare, financial services).
- Intellectual property (e.g., patents, trade secrets).
- Handling and Protection:
- Labeling: Mark as "Restricted" with clear indicators of sensitivity.
- Access Control: Strict access control measures; limited to a very small group of individuals with a clear need-to-know basis.
- Retention: Retain according to strict regulatory and business requirements; employ secure methods for disposal, such as data shredding or encryption.
- Labeling: Mark as "Restricted" with clear indicators of sensitivity.
- Examples:
Implementing Data Labeling, Handling, and Retention Policies
Data Labeling
Purpose: Data labeling involves marking data with its classification level to ensure that it is handled appropriately throughout its lifecycle.
Implementation Steps:
- Create Standard Labels: Develop a set of standard labels for each classification level (e.g., "Public", "Internal" ,"Confidential", "Restricted").
- Automate Labeling: Use data classification tools to automatically label data based on predefined rules and patterns.
- Educate Employees: Train employees on the importance of data labeling and how to apply labels correctly.
Example: An organization uses data classification software to scan emails and documents for sensitive content. The software automatically labels documents containing financial information as "Confidential" and applies the appropriate handling restrictions.
Data Handling
Purpose: Data handling policies dictate how data should be accessed, shared, and stored based on its classification level.
Implementation Steps:
- Define Access Controls: Establish access control mechanisms for each classification level, including authentication and authorization requirements.
- Set Sharing Guidelines: Create guidelines for sharing data, such as encryption for confidential data and secure communication channels for restricted data.
- Implement Monitoring: Use monitoring tools to track data access and sharing activities to detect and prevent unauthorized actions.
Example: Confidential employee records are stored in an encrypted database accessible only to HR personnel with multi-factor authentication (MFA). Sharing these records externally requires approval from HR management and the use of encrypted email.
Data Retention
Purpose: Data retention policies determine how long data should be kept and how it should be disposed of based on its classification.
Implementation Steps:
- Define Retention Periods: Establish retention periods for each classification level based on legal, regulatoy, and business requirements.
- Automate Retention: Use data lifecycle management tools to automate the retention and deletion of data according to policies.
- Ensure Secure Disposal: Implement secure disposal methods for sensitive data, such as data wiping and shredding for physical documents.
Example: Confidential customer contracts are retained for seven years to comply with legal requirements. Alter this period, the documents are securely deleted from digital storage using data wiping software, and physical copies are shredded.
By implementing data classification schemes and corresponding labeling, handling, and retention policies, organizations can protect sensitive information, ensure compliance with regulations, and effectively manage data throughout its lifecycle.
Comparing Symmetric and Asymmetric Encryption Algorithms
Symmetric Encryption
Symmetric Encryption uses the same key for both encryption and decryption. It is also known as secret-key encryption.
Key Features:
- Single Key: One key is used for both encryption and decryption.
- Speed: Generally faster than asymmetric encryption, making it suitable for encrypting large amounts of data.
- Security: The key must be kept secret and securely shared between the communicating parties.
Use Cases:
- Data Encryption: Encrypting files and databases.
- Communication: Securing data transmission in VPNs and TLS.
- Storage: Protecting data at rest on storage devices.
Example:
Advanced Encryption Standard (AES): A widely used symmetric encryption standard that provides strong security and is efficient for both hardware and software implementations.
Asymmetric Encryption
Asymmetric Encryption uses a pair of keys, a public key for encryption and a private key for decryption. It is also known as public-key encryption.
Key Features:
- Key Pair: Consists of a public key (shared openly) and a private key (kept secret).
- Security: Provides robust security for key distribution and digital signatures.
Use Cases:
- Speed: Slower than symmetric encryption, making it less suitable for encrypting large amounts of data.
- Key Exchange: Securely exchanging keys for symmetric encryption.
- Digital Signatures: Verifying the authenticity and integrity of messages.
- Email Encryption: Encrypting emails and attachments. example:
- RSA (Rivest-Shamir-Adleman): A widely used asymmetric encryption algorithm for secure data transmisson and digital signatures.
Key Concepts of Key Management
Effective key management is crucial for maintaining the security of encryption systems. Key management involves key generation, key distribution, key storage, and key rotation.
Key Generation
Key Generation is the process of creating cryptographic keys.
Key Features:
- Randomness: Keys must be generated using a secure and unpredictable process to ensure they cannot be easily guessed.
- Length: The key length should be sufficient to provide the desired level of security (e.g., AES typically uses 128, 192, or 256-bit keys).
Example: Generating AES keys using a cryptographic random number generator.
Key Distribution
Key Distribution involves securely sharing cryptographic keys between parties.
Key Features:
- Secure Channels: Keys must be distributed over secure channels to prevent interception.
- Protocols: Use key exchange protocols like Diffie-Hellman or public-key encryption to securely distribute symmetric keys.
Example: Using RSA encryption to securely send an AES key to a recipient.
Key Storage
Key Storage refers to the secure storage of cryptographic keys.
Key Features:
- Protection: Keys must be stored in a secure manner to prevent unauthorized access.
- Hardware Security Modules (HSMs): Dedicated hardware devices designed to securely store and manage cryptographic keys.
Example: Storing keys in an HSM to protect against physical and logical attacks.
Key Rotation
Key Rotation involves regularly changing cryptographic keys to reduce the risk of key compromise.
Key Features:
- Regular Intervals: Keys should be rotated at regular intervals or after a specific number of uses.
- Automated Processes: Implement automated processes for key rotation to ensure consistency and compliance.
Example: Rotating encryption keys for a database every three months to enhance security.
Common Encryption Solutions
Advanced Encryption Standard (AES)
AES is a symmetric encryption algorithm widely used for securing data.
Key Features:
- Strong Security: Provides robust encryption with key sizes of 128, 192, and 256 bits.
- Efficiency: Fast and efficient in both hardware and software implementations.
- Versatility: Used in a variety of applications, including data encryption, secure communications, and storage encryption.
Use Cases:
- Encrypting sensitive files and databases.
- Securing data transmitted over networks.
Pretty Good Privacy (PGP)
PGP is an encryption program that provides cryptographic privacy and authentication for data communication.
Key Features:
- Hybrid Encryption: Combines symmetric encryption for data encryption and asymmetric encryption for key exchange.
- Digital Signatures: Supports digital signatures to verify the authenticity and integrity of messages.
- Email Security: Commonly used for encrypting emails and attachments.
Use Cases:
- Encrypting and signing emails.
- Securing file transfers.
Transparent Data Encryption (TDE)
TDE is a technology used to encrypt databases at the file level to protect data at rest.
Key Features:
- Automatic Encryption: Encrypts database files without requiring changes to applications.
- Performance: Minimal impact on database performance.
- Key Management: Integrates with enterprise key management solutions to manage encryption keys securely.
Use Cases:
- Encrypting databases to protect sensitive data stored on disk.
- Compliance with data protection regulations.
By understanding the differences between symmetric and asymmetric encryption, and implementing effective key management practices, organizations can enhance their data security and protect sensitive information from unauthorized access and breaches.
Key Components of a Public Key Infrastructure (PKI)
A Public Key Infrastructure (PKI) is a framework that enables secure, encrypted communication and authentication over networks. It uses a combination of hardware, software, policies, and standards to manage digital certificates and public-key encryption. Here are the key components:
Certificate Authorities (CAs)
CAs are trusted entities responsible for issuing, managing, and revoking digital certificates. They verify the identity of entities requesting certificates and vouch for their authenticity.
Functions:
- Issuance: Generate and issue digital certificates.
- Validation: Verify the credentials of entities requesting certificates.
- Revocation: Maintain and publish lists of revoked certificates.
- Lifecycle Management: Manage the entire lifecycle of digital certificates from issuance to expiration.
Example: Let's Encrypt is a widely used CA that provides free SSL/TLS certificates to secure websites.
Registration Authorities (RAs)
RAs act as intermediaries between entities requesting certificates and the CA. They perform the initial verification of entities before forwarding the certificate request to the CA for issuance.
Functions:
- Identity Verification: Authenticate the identity of entities requesting certificates.
- Request Handling: Forward verified certificate requests to the CA.
- Support: Assist in certificate renewal and revocation processes.
Example: In a large organization, the IT department might function as an RA, verifying employee identities and their need for digital certificates before requesting them from the CA.
Digital Certificates
Digital certificates are electronic credentials that bind a public key to an entity's identity. They are used to authenticate identities and secure communications.
Components:
- Public Key: The public key of the entity.
- Subject Information: Information about the entity (e.g., name, organization).
- Issuer Information: Information about the CA that issued the certificate.
- Validity Period: The start and end dates of the certificate's validity.
- Digital Signature: The CA's signature, which verifies the certificate's authenticity.
Example: An SSL/LS certificate for a website contains the website's public key, the CA's information, and the validity period, enabling secure HTTPS connections.
Certificate Revocation Lists (CRLs)
CRLs are lists of digital certificates that have been revoked by the CA before their expiration date. They are published regularly to ensure that entities do not trust compromised or invalid certificates.
Functions:
- Revocation: Record certificates that are no longer trusted.
- Publication: Regularly update and distribute the CRL to entities in the PKI ecosystem.
- Validation: Allow entities to check the revocation status of certificates.
Example: If a company's private key is compromised, the associated digital certificate is added to the CA's CRL, signaling to others that it should no longer be trusted.
Process of Issuing, Distributing, and Revoking Digital Certificates Issuing Digital Certificates
- Certificate Request:
- An entity generates a key pair (public and private keys) and creates a Certificate Signing Request (CSR) containing the public key and identity information.
- The CSR is submitted to an RA or directly to a CA.
- An entity generates a key pair (public and private keys) and creates a Certificate Signing Request (CSR) containing the public key and identity information.
- Identity Verification:
- The RA verifies the entity's identity and the validity of the CSR.
- The verified CSR is forwarded to the CA for processing.
- The RA verifies the entity's identity and the validity of the CSR.
- Certificate Generation:
- The CA generates a digital certificate by embedding the entity's public key, identity information, and other relevant details.
- The CA digitally signs the certificate using its private key.
- The CA generates a digital certificate by embedding the entity's public key, identity information, and other relevant details.
- Certificate Issuance:
- The digital certificate is issued to the requesting entity.
- The entity installs the certificate on its systems (e.g., web server, email client).
- The digital certificate is issued to the requesting entity.
Distributing Digital Certificates
- Publication:
- The CA may publish the digital certificate in a public repository or directory.
- Entities can download and verify the certificate as needed.
- The CA may publish the digital certificate in a public repository or directory.
- Installation:
- The certificate is installed on the entity's systems to enable secure communications.
- Web servers, for example, use SSL/TLS certificates to establish HTTPS connections with clients.
- The certificate is installed on the entity's systems to enable secure communications.
Revoking Digital Certificates
- Revocation Request:
- If a certificate needs to be revoked (e.g., due to a key compromise), the entity submits a revocation request to the CA.
- If a certificate needs to be revoked (e.g., due to a key compromise), the entity submits a revocation request to the CA.
- Verification:
- The CA verifies the revocation request and the reasons for revocation.
- The CA verifies the revocation request and the reasons for revocation.
- Updating CRL:
- The CA adds the revoked certificate to its CRL.
- The updated CRL is published and distributed to ensure that other entities do not trust the revoked certificate.
- The CA adds the revoked certificate to its CRL.
Role of PKI in Securing Electronic Transactions and Communications
PKI plays a critical role in securing electronic transactions and communications through the following mechanisms:
- Authentication:
- Digital certificates verify the identity of entities involved in electronic transactions, ensuring that parties are who they claim to be.
- Example: SSL/TLS certificates authenticate websites to users, preventing phishing attacks.
- Digital certificates verify the identity of entities involved in electronic transactions, ensuring that parties are who they claim to be.
- Encryption:
- Public key encryption, facilitated by PKI, secures data in transit by encrypting it with the recipient's public key. Only the recipient's private key can decrypt the data.
- Example: Secure email services use PKI to encrypt emails, ensuring that only the intended recipient can read the content.
- Public key encryption, facilitated by PKI, secures data in transit by encrypting it with the recipient's public key. Only the recipient's private key can decrypt the data.
- Integrity
- Digital signatures, enabled by PKI, ensure the integrity of data by providing a mechanism to deter any unauthorized alterations.
- Example: Software developers sign their applications with a digital certificate, allowing users to verify that the software has not been tampered with.
- Digital signatures, enabled by PKI, ensure the integrity of data by providing a mechanism to deter any unauthorized alterations.
- Non-repudiation:
- PKI provides non-repudiation by linking actions or communications to specific entities, preventing them from denying their involvement.
- Example: Digital signatures on legal documents provide evidence that the signer cannot later repudiate.
- PKI provides non-repudiation by linking actions or communications to specific entities, preventing them from denying their involvement.
By implementing a robust PKI, organizations can protect sensitive information, ensure the authenticity of communications, and maintain the integrity and confidentiality of electronic transactions.
Key Techniques for Securing Web Communications
Securing web communications is essential for protecting data transmitted between clients and servers from interception, tampering, and unauthorized access. Two primary protocols used for this purpose are Secure Sockets Layer (SSL) and Transport Layer Security (TLS).
Secure Sockets Layer (SSL) and Transport Layer Security (TLS)
SSL is the predecessor of TLS and was initially developed to secure web communications. TLS is an updated and more secure version of SSL. Both protocols provide three key security features: encryption, authentication, and integrity.
SSL/TLS Encryption
SSL/TLS Encryption ensures that data transmitted between the client and server is encrypted, making it unreadable to unauthorized parties who might intercept the communication.
How It Works:
- Symmetric Encryption: Used for the actual data transmission due to its speed and efficiency. A shared session key is used for this purpose.
- Asymmetric Encryption: Used during the initial handshake to securely exchange the session key. Public and private keys are involved in this process.
Example: When a user connects to a website using HTTPS, TLS encrypts the data exchanged between the user's browser and the web server, ensuring confidentiality.
SSL/TLS Authentication
SSL/TLS Authentication verifies the identities of the parties involved in the communication, ensuring that the client is connecting to a legitimate server and not an impostor.
How It Works:
- Digital Certificates: Servers present a digital certificate issued by a trusted Certificate Authority (CA) to prove their identity.
- Public Key Infrastructure (PKI): The client uses the server's public key, contained in the digital certificate, to verify the server's identity.
Example: When a user visits a banking website, the browser checks the digital certificate to ensure the website is legitimate and issued by a trusted CA.
SSL/TLS Integrity
SSL/TLS Integrity ensures that the data transmitted between the client and server has not been altered during transit.
How It Works:
- Message Authentication Codes (MACs): Used to verify data integrity. A MAC is a short piece of information used to authenticate a message and ensure that the message content is unaltered.
- Hash Functions: TLS uses hash functions to create MACs for the transmitted data.
Example: During a secure session, TLS uses MACs to detect any changes to the data. If the data is altered, the integrity check falls, and the session is terminated.
Common Web Security Vulnerabilities
Despite the protection offered by SSL/TLS, web applications can still be vulnerable to various security threats. Two common web security vulnerabilities are Cross-Site Scripting (XSS) and SQL Injection.
Cross-Site Scripting (XSS)
Cross-Site Scripting (XSS) is a vulnerability that allows attackers to inject malicious scripts into web pages viewed by other users.
How It Works:
- Injection: Attackers inject malicious scripts into a trusted website. These scripts are executed in the context of the user's browser.
- Execution: When a user visits the compromised page, the malicious script runs and can perform actions like stealing cookies, session tokens, or other sensitive information.
Example: An attacker injects a malicious JavaScript code into a comment section of a website. When another user views the comment, the script executes, potentially stealing the user's session cookies.
Prevention:
- Input Validation and Sanitization: Ensure that all user inputs are properly validated and sanitized to prevent malicious scripts from being injected.
- Content Security Policy (CSP): Implement CSP to restrict the sources from which scripts can be loaded.
SQL Injection
SQL Injection is a vulnerability that allows attackers to execute arbitrary SQL code on a database by inserting malicious SQL statements into input fields.
How It Works:
- Injection: Attackers inject malicious SQL code into input fields (e.g., login forms, search boxes) that are not properly sanitized.
- Execution: The web application passes the malicious code to the database, which executes the unauthorized SQL commands.
Example: An attacker enters'; DROP TABLE users; - into a login form. If the input is not sanitized, the database might execute this command, deleting the users table.
Prevention:
- Prepared Statements and Parameterized Queries: Use prepared statements to ensure that user inputs are treated as data, not executable code.
- Input Validation and Sanitization: Validate and sanitize all user inputs to prevent malicious SQL code from being injected.
Securing web communications using SSL and TLS protocols is crucial for protecting data during transmission by providing encryption, authentication, and integrity. Despite these protections, web applications can still be vulnerable to attacks like Cross-Site Scripting (XSS) and SQL Injection, which highlight the importance of comprehensive security measures, including input validation, sanitization, and the use of security best practices like prepared statements and content security policies. Implementing these measures can significantly enhance the security of web communications and protect against common vulnerabilities.
Key Security Challenges and Best Practices for Virtualized Environments
Virtualized environments present unique security challenges due to the abstraction of hardware resources and the consolidation of multiple virtual machines (VMs) on a single physical server. To maintain security, organizations must address several key areas:
- Hypervisor Security
- Security Challenges:
- Single Point of Failure: The hypervisor, as the core component managing VMs, is a critical point of attack.
- Exploits and Vulnerabilities: Hypervisors can have vulnerabilities that attackers might exploit to gain control over VMs.
- Single Point of Failure: The hypervisor, as the core component managing VMs, is a critical point of attack.
- Best Practices:
- Patch Management: Regularly update and patch the hypervisor to protect against known vulnerabilities.
- Access Controls: Implement strict access controls and role-based access to the hypervisor.
- Monitoring and Logging: Continuously monitor and log hypervisor activities to detect and respond to suspicious behaviour.
- Minimal Attack Surface: Disable unused services and features to minimize the attack surface.
- Patch Management: Regularly update and patch the hypervisor to protect against known vulnerabilities.
- Security Challenges:
- Virtual Machine Isolation
- Security Challenges:
- Escape Attacks: Attackers might attempt to escape from a VM to access the host or other VMs.
- Inter-VM Traffic: Inadequate isolation can lead to unauthorized access and data breaches.
- Escape Attacks: Attackers might attempt to escape from a VM to access the host or other VMs.
- Best Practices:
- Strong Isolation Mechanisms: Use strong isolation mechanisms to ensure that VMs cannot interfere with each other.
- Network Segmentation: Segment network traffic between VMs to prevent unauthorized communication.
- Resource Controls: Implement resource controls to prevent one VM from consuming excessive resources and affecting others.
- Strong Isolation Mechanisms: Use strong isolation mechanisms to ensure that VMs cannot interfere with each other.
- Security Challenges:
- Virtual Network Security
- Security Challenges:
- Virtual Network Traffic: Traffic between VMs on the same host might bypass traditional network security controls.
- Visibility: Reduced visibility into virtual network traffic can hinder security monitoring and incident response.
- Virtual Network Traffic: Traffic between VMs on the same host might bypass traditional network security controls.
- Best Practices:
- Virtual Firewalls: Deploy virtual firewalls to inspect and control traffic between VMs.
- Network Monitoring: Use virtual network monitoring tools to gain visibility into virtual network traffic.
- Security Policies: Define and enforce security policies for virtual networks, similar to those used for physical networks.
- Virtual Firewalls: Deploy virtual firewalls to inspect and control traffic between VMs.
- Security Challenges:
- Virtual Machine Image Management
- Security Challenges:
- Image Sprawl: Uncontrolled proliferation of VM images can lead to security risks.
- Outdated Images: Use of outdated VM images can expose vulnerabilities.
- Image Sprawl: Uncontrolled proliferation of VM images can lead to security risks.
- Best Practices:
- Centralized Management: Implement a centralized management system for VM images.
- Image Hardening: Harden VM images by disabling unnecessary services and applying security configurations.
- Regular Updates: Keep VM images updated with the latest security patches and configurations.
- Version Control: Use version control to manage changes to VM images and ensure that only approved images are used.
- Centralized Management: Implement a centralized management system for VM images.
- Security Challenges:
Micro-Segmentation in Virtualized Infrastructures
Micro-segmentation is a network security technique that involves creating isolated segments within a virtualized environment at a granular level. It allows for the enforcement of security policies and access controls for individual workloads or applications within a data center.
How Micro-Segmentation Works:
- Fine-Grained Policies: Security policies are applied to individual VMs, containers, or applications rather than broad network segments.
- Software-Defined Networking (SDN): Utilizes SDN to dynamically create and manage network segments.
- Automation: Automates the application of security policies based on predefined rules and conditions.
Benefits of Micro-Segmentation:
- Enhanced Security: Limits the lateral movement of attackers within the data center, containing breaches to isolated segments.
- Granular Control: Provides granular control over network traffic, enabling precise enforcement of security policies.
- Visibility: Improves visibility into traffic patterns and security events within the virtualized environment.
- Compliance: Helps meet regulatory requirements by ensuring sensitive data is segmented and access is controlled.
Implementation Example: A financial services company uses micro-segmentation to secure its virtualized environment. Each VM hosting sensitive financial applications is segmented, and security policies are applied to control access to these VMs. For example, only specific VMs within the accounting department can communicate with the financial database VM, and all traffic between them is monitored and inspected by virtual firewalls.
Applying Best Practices in Virtualized Environments
- Hypervisor Security: Regularly update the hypervisor with security patches.
- Implement strong authentication and access controls for hypervisor management interfaces.
- Enable logging and monitoring to detect any unusual activities.
- Implement strong authentication and access controls for hypervisor management interfaces.
- Virtual Machine Isolation: Use hypervisor-based security features to enforce VM isolation.
- Implement network segmentation to control inter-VM communication.
- Use resource controls to prevent any single VM from exhausting shared resources.
- Implement network segmentation to control inter-VM communication.
- Virtual Network Security: Deploy virtual firewalls and intrusion detection/prevention systems (IDS/IPS) to inspect and filter virtual network traffic.
- Use network segmentation to isolate critical workloads and control traffic flow.
- Monitor virtual network traffic for anomalies and potential threats.
- Use network segmentation to isolate critical workloads and control traffic flow.
- Virtual Machine Image Management: Centralize VM image management to control and track all VM images.
- Harden VM images by disabling unnecessary services and applying security best practices.
- Regularly update VM images to include the latest security patches.
- Implement version control to ensure only approved and secure VM images are deployed.
- Harden VM images by disabling unnecessary services and applying security best practices.
- Micro-Segmentation: Use SDN to dynamically manage and enforce micro-segmentation policies.
- Define fine grained security policies based on workloads and applications.
- Monitor and log all traffic within micro-segments to detect and respond to security incidents.
- Define fine grained security policies based on workloads and applications.
By addressing these key security challenges and implementing best practices, organizations can significantly enhance the security of their virtualized environments, protecting sensitive information and maintaining compliance with regulatory requirements
Conclusion
By seamlessly integrating these security measures, a Holistic Cloud Security Defense-In-Depth Strategy establishes a proactive, resilient, and multi-layered security framework across all facets of cloud infrastructure, spanning data, application, endpoint, and network security layers. This comprehensive approach not only minimizes attack surfaces and mitigates risks but also strengthens regulatory compliance, enhances threat detection and response, and ensures business continuity in an ever-evolving cyber threat landscape.
Disclaimer: This documentation is intended for educational purposes only. The content provided herein is meant to inform and educate individuals about security practices, techniques, and tools. Security-Science does not support, endorse, or encourage any illegal or unethical activities, including but not limited to unauthorized access to computer systems, networks, or data. Users are advised to apply the knowledge gained responsibly and ensure compliance with all applicable laws and regulations. Security-Science shall not be held liable for any misuse of the information provided.