Author: Arnel C. Reyes
Published: 30 August 2024
Last Updated: 31 August 2024
ProxyChains is a tool that allows users to route their network traffic through multiple proxy servers, enhancing privacy and anonymity. By chaining proxies together, it becomes more challenging for someone to trace the origin of network traffic. ProxyChains supports different types of proxies, including HTTP, SOCKS4, SOCKS5, and raw proxies, including HTTP, SOCKS4, SOCKS5, and raw proxies, and offers various modes for handling the ProxyList.
Background
ProxyChains is often used in environments where anonymity and privacy are crucial, such as penetration testing, secure web browsing, or bypassing firewalls and censorship. The concept behind ProxyChains is to create a chain of proxies through which traffic is routed, making it difficult for third parties to track user's online activities. Each proxy in the chain only knows the previous and next proxies, not the original source or final destination of the traffic. This multi-layered approach is an effective method to obfuscate the true source of network connections.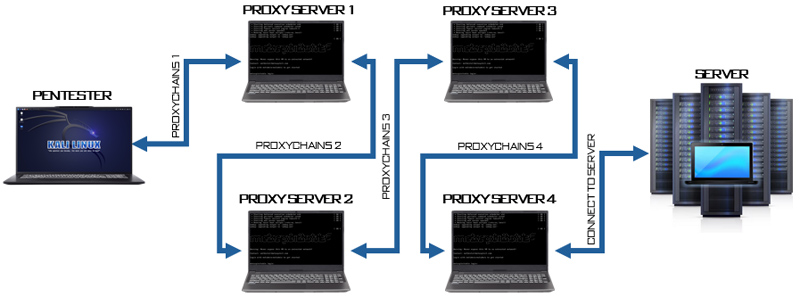
Configuration
To configure ProxyChains, it is needed to edit the configuration file typically located at '/etc/proxychains4.conf' on Unix-like systems (e.g. Kali Linux). The configuration involves specifying the mode of chaining and listing the proxies to be used.
Chaining Options
- dynamic_chain: This option allows ProxyChains to continue routing traffic through the remaining proxies if one in the chain fails. This mode increases reliability but could reduce anonymity.
- strict_chain: All proxies listed in the ProxyList must be operational for the traffic to pass through. If any proxy fails, the connection fails, providing high anonymity but less reliability.
- round_robin_chain: Proxies are used sequentially, and the traffic is routed through them in a circular order. This mode is balanced between reliability and anonymity.
- random_chain: Proxies are selected randomly from the list for each connection, adding another layer of unpredictability, which can enhance anonymity but might affect performance.
Proxy Types
- http: Routes traffic through an HTTP proxy server. It's primarily used for web traffic.
- socks4: Uses a SOCKS4 proxy, which is an older protocol supporting TCP connections without authentication.
- socks5: The SOCKS5 protocol supports both TCP and UDP traffic and includes support for authentication.
- raw: The raw proxy type simply forwards traffic without any protocol translation, typically used for specialized applications.
How to Configure ProxyChains
Step 1: Locate ProxyChains executable and configuration-related files.
| $ locate proxychains /etc/proxychains4.conf /etc/alternatives/proxychains /etc/alternatives/proxychains.1.gz /usr/bin/proxychains /usr/bin/proxychains4 /usr/bin/proxychains4-daemon ...snip... |
Step 2: Configure ProxyChains using file editor.
| $ sudo nano /etc/proxychains4.conf |
Make the following changes in the configuration file. Uncomment the 'dynamic_chain' line to enable dynamic chaining.
| ...snip... dynamic_chain # # Dynamic - Each connection will be done via chained proxies # all proxies chained in the order as they appear in the list # at least one proxy must be online to play in chain # (dead proxies are skipped) # otherwise EINTR is returned to the app ...snip... |
Comment out the 'strict_chain' line to disable strict chaining.
| ...snip... # strict_chain # # Strict - Each connection will be done via chained proxies # all proxies chained in the order as they appear in the list # all proxies must be online to play in chain # otherwise EINTR is returned to the app ...snip... |
Uncomment the 'proxy_dns' line to enable DNS requests to be routed through the proxy chain.
| ...snip... # method 1. this uses the proxychains4 style method to do remote dns: # a thread is spawned that serves DNS requests and hands down an ip # assigned from an internal list (via remote_dns_subnet). # this is the easiest (setup-wise) and fastest method, however on # systems with buggy libcs and very complex software like webbrowsers # this might not work and/or cause crashes. proxy_dns ...snip... |
Edit the '[ProxyList]' section to add proxies and comment out the default ToR proxy if it's not needed.
| ...snip... # ProxyList format # type ip port [user pass] # (values separated by 'tab' or 'blank') # # only numeric ipv4 addresses are valid # # # Examples: # # socks5 192.168.67.78 1080 lamer secret # http 192.168.89.3 8080 justu hidden # socks4 192.168.1.49 1080 # http 192.168.39.93 8080 # # # proxy types: http, socks4, socks5, raw # * raw: The traffic is simply forwarded to the proxy without modification. # ( auth types supported: "basic"-http "user/pass"-socks ) # [ProxyList] # add proxy here ... # meanwile # defaults set to "tor" # socks4 127.0.0.1 9050 socks5 184.170.248.5 4145 socks5 98.175.31.195 4145 http 134.209.67.109 19752 http 152.26.229.42 9443 |
Note: The '[ProxyList]' entries are simply examples to provide variety of options. Free proxy lists can be obtained from spys.one website.
Here is an example of a basic ProxyChains configuration file:
| # Dynamic - Each connection will be done via chained proxies # all proxies chained in the order as they appear in the list # at least one proxy must be online to play in chain # (dead proxies are skipped) # otherwise EINTR is returned to the app dynamic_chain # This uses the proxychains4 style method to do remote dns proxy_dns # Some timeouts in milliseconds tcp_read_time_out 15000 tcp_connect_time_out 8000 [ProxyList] socks5 184.170.248.5 4145 socks5 98.175.31.195 4145 http 134.209.67.109 19752 http 152.26.229.42 9443 |
Step 3: Test ProxyChains, once configured, test with the following commands.
Test with Firefox:
| $ proxychains firefox https://www.whatismyip.com [proxychains] config file found: /etc/proxychains4.conf [proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4 [proxychains] DLL init: proxychains-ng 4.17 [proxychains] DLL init: proxychains-ng 4.17 [proxychains] DLL init: proxychains-ng 4.17 [proxychains] DLL init: proxychains-ng 4.17 [proxychains] DLL init: proxychains-ng 4.17 [proxychains] Dynamic chain ... 184.170.248.5:4145 ... 152.26.229.42:9443 ... whatismyip.com:443 ... OK [proxychains] DLL init: proxychains-ng 4.17 [proxychains] Dynamic chain ... 184.170.248.5:4145 ... 152.26.229.42:9443 ... contile.services.mozilla.com:443 ... OK [proxychains] Dynamic chain ... 184.170.248.5:4145 ... 152.26.229.42:9443 ... spocs.getpocket.com:443 [proxychains] DLL init: proxychains-ng 4.17 [proxychains] DLL init: proxychains-ng 4.17 ... OK [proxychains] Dynamic chain ... 184.170.248.5:4145 ... 152.26.229.42:9443 [proxychains] DLL init: proxychains-ng 4.17 ... content-signature-2.cdn.mozilla.net:443 [proxychains] DLL init: proxychains-ng 4.17 ... OK [proxychains] Dynamic chain ... 184.170.248.5:4145 ... 152.26.229.42:9443 ... www.whatismyip.com:443 ... OK |
Test result to check public IP Address:
Test with NMap:
| $ proxychains nmap -Pn -sT -p 80,443 scanme.nmap.org [proxychains] config file found: /etc/proxychains4.conf [proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4 [proxychains] DLL init: proxychains-ng 4.17 Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-08-30 23:54 EDT [proxychains] Dynamic chain ... 184.170.248.5:4145 ... 98.175.31.195:4145 ... 134.209.67.109:19752 ... 152.26.229.42:9443 ... scanme.nmap.org :80 <--socket error or timeout! [proxychains] Dynamic chain ... 184.170.248.5:4145 ... 98.175.31.195:4145 ... 134.209.67.109:19752 ... 152.26.229.42:9443 ... scanme.nmap.org :443 <--socket error or timeout! Nmap scan report for scanme.nmap.org (224.0.0.1) Host is up (4.3s latency). rDNS record for 224.0.0.1: all-systems.mcast.net PORT STATE SERVICE 80/tcp closed http 443/tcp closed https Nmap done: 1 IP address (1 host up) scanned in 6.86 seconds |
Conclusion
ProxyChains is a powerful tool for enhancing privacy and anonymity by routing network traffic through multiple proxies. With various configuration options and proxy types, it offers flexibility and control over how traffic is managed. Proper configuration and understanding of the different chaining methods are crucial to effectively leveraging ProxyChains for secure and anonymous online activities.
Disclaimer: This documentation is intended for educational purposes only. The content provided herein is meant to inform and educate individuals about security practices, techniques, and tools. Security-Science does not support, endorse, or encourage any illegal or unethical activities, including but not limited to unauthorized access to computer systems, networks, or data. Users are advised to apply the knowledge gained responsibly and ensure compliance with all applicable laws and regulations. Security-Science shall not be held liable for any misuse of the information provided.